
Cryptography plays a huge role in cybersecurity. From protocols like TLS to algorithms like AES, it helps to provide confidentiality, integrity, authenticity and nonrepudiation to our communications.
To put it formally, cryptography is the study and practice of protecting communications against attackers. But where did it come from?
Cryptography’s humble beginnings
Cryptography evolved along with civilization. If you were a caveman and you wanted to tell Zog where the best berries are without Grug finding out (everyone hates Grug), all you would have to do is whisper it out of Grug’s earshot. As long as Grug didn’t overhear and Zog didn't tell anyone, your wonderful berries would remain a secret.
Now, let’s fast-forward a few millennia. You’re an emperor and you want to send a message to your top general about when to launch the surprise attack. You can’t just whisper it to your general if he’s in another town. You could send a note with your most-trusted horse messenger, but what if he gets captured by the enemy, or if he’s secretly a double agent?
If you had written the message in plaintext, it would fall straight into the enemy’s hands and the surprise attack would be ruined. So humans needed to develop some kind of code that the enemy couldn't understand.
The scytale
Cryptography began to appear in some of the ancient kingdoms such as India, Israel, and Greece. The Ancient Greeks made use of a tool known as a scytale, which you can see in the pic at the top of the page (by Luringen and licensed under the GNU Free Documentation License. The image has been altered and the background color changed).
Scytales use rods of a specific diameter for both encryption and decryption. Both the sender and the recipient need rods of the same size in order to easily decrypt the messages. The sender takes a long strip of parchment or leather and wraps it around the rod to cover it.
They would then start writing on top of the leather, from left to right, writing each subsequent line beneath, similarly to how we would write on a page. It can be hard to wrap your head around how this works without holding a scytale in your hand, but we’ll give it a go. It probably wouldn’t hurt if you check out the image above as well.
Imagine that the following 2D diagram is really wrapped around a rod. The start of the strip of leather begins in the leftmost column, while the end is on the right. The bottom of each column wraps around to the top of the column to its right:

Once the sender has finished writing the message, they would unwrap the strip, meaning that it would no longer be easily legible. Instead, the strip would look like this (we’ve split it into two columns to save space):
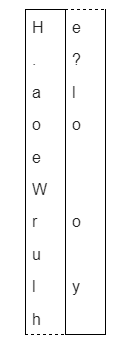
At a glance, it’s pretty hard to tell what this strip actually says. If an enemy intercepts it, they might realize that it’s a coded message. They could try wrapping it around a rod, but unless they knew the precise size of the rod it was written on, the initial message would not align. That’s why both the sender and the recipient both require rods of equal size. Once the recipient gets the message, all they have to do is wrap it around their matching rod, and the original message will align.
The scytale is far from perfect as an encryption technique, but given the rudimentary tools of the era, it was a lot better than just sending important messages as plaintext.
Transposition ciphers
The scytale falls into a class of cryptography known as transposition ciphers. Instead of substituting each letter for a different one, transposition essentially involves mixing around the positions of letters. As a simple demonstration, a transposition cipher could rearrange “HELLO” into “LOLEH. This contrasts with the substitution ciphers we discuss below, which substitute letters, changing “HELLO” into something like “KHOOR”.
Substitution ciphers
Substitution ciphers are another early form of cryptography. The most famous example we have is the Caesar cipher, a technique that Julius Caesar used to encode his messages.
The underlying premise is fairly simple. You take the message you want to encrypt:
HELLO
And then you shift each letter a set number of positions, whether it’s 3, 5, 22, or whatever. If we choose a shift of 3, H would skip over I and J to become K. E would skip over F and G to become H. L would become O and so on, giving us:
KHOOR
KHOOR looks nothing like HELLO, so the uninitiated adversary may not be able to figure out the meaning of the message. But if you and your intended recipient have agreed upon a substitution involving 3 shifts, they know that all they have to do is substitute each letter for the one 3 positions before it in the alphabet. This gives you and your recipient an easy way to keep your messages safe–unless your adversary knows the code.
Beyond the ancients
As Europe struggled through the dark ages, the Arabic world took much of the lead on cryptography, inventing code breaking techniques like frequency analysis. Once the Renaissance hit, Europeans again began making progress, producing more advanced ciphers and cryptanalysis techniques. This led into the machine age, where tools like the Enigma machine were critical for German encryption in World War II. Breaking the Enigma machine ended up playing a pivotal role in the Allies ultimate victory.
After World War II, computing began making significant progress. This brought us to the dawn of the digital era, when cryptography really started to come into its own with algorithms like DES, RSA and AES. But we’ll save that discussion for next time.

