The first CISSP domain focuses on the fundamentals of security and how to assess and manage risk. It makes sense since both of these concepts are an essential part of our personal and professional lives. Therefore, we have to analyze every risk associated with every action we take.
Moreover, technology adoption growth and digitalization require cybersecurity professionals to be aware of the topics discussed in CISSP Domain 1. It also focuses heavily on the critical factors of governance and compliance and how security helps by aligning and contributing to each.
Have a look at everything you need to know for the CISSP certification exam for domain 1 in this article.
1.1 Understand, adhere to, and promote professional ethics
Ethics
Ethics are a foundational element of a successful security program and should be adhered to throughout the organization. Proper ethical behavior is based upon one belief: abide by the rules and do nothing harmful to anyone else.
Within an organization, the best way to prescribe, promote, and instill consistent ethical behavior is through corporate rules or laws, more appropriately referred to as policies, to ensure that all employees employ the same set of ethics.
As a CISSP candidate, you are responsible for understanding and complying with the ISC2 Code of Professional Ethics, which applies to CISSP holders around the globe. In fact, the CISSP exam will most likely ask at least one question on this topic.
The Preamble and the Code of Professional Ethics Canons must be understood fully in the context of corporate and industry applications. The Canons should be memorized and adhered to in the order presented.
- The safety and welfare of society and the common good, the duty to our principals, and to each other, requires that we adhere, and be seen to adhere, to the highest ethical standards of behavior.
- Therefore, strict adherence to this Code is a condition of certification.
The ISC2 Code of Ethics consists of the Canons outlined here:
ISC2 Code of Ethics Canons | |
|---|---|
1 | Protect society, the common good, necessary public trust and confidence, and the infrastructure. |
2 | Act honorably, honestly, justly, responsibly, and legally. |
3 | Provide diligent and competent service to principals. |
4 | Advance and protect the profession. |
Remember, if a scenario is presented in which there's a conflict in the Canons, they need to be applied in order.
1.2 Understand and apply security concepts
Focus of security
Security focuses on anything that represents value, better referred to as assets, and implements control that ultimately increases the value of those assets.
Therefore, the focus of the security function is to:
- Allow and enable the organization to achieve its goals and objectives.
- Increase the organization's value.
Confidentiality, integrity, availability, authenticity, and nonrepudiation
The CIA triad is a foundational model that helps organizations design, structure, and implement security functions.
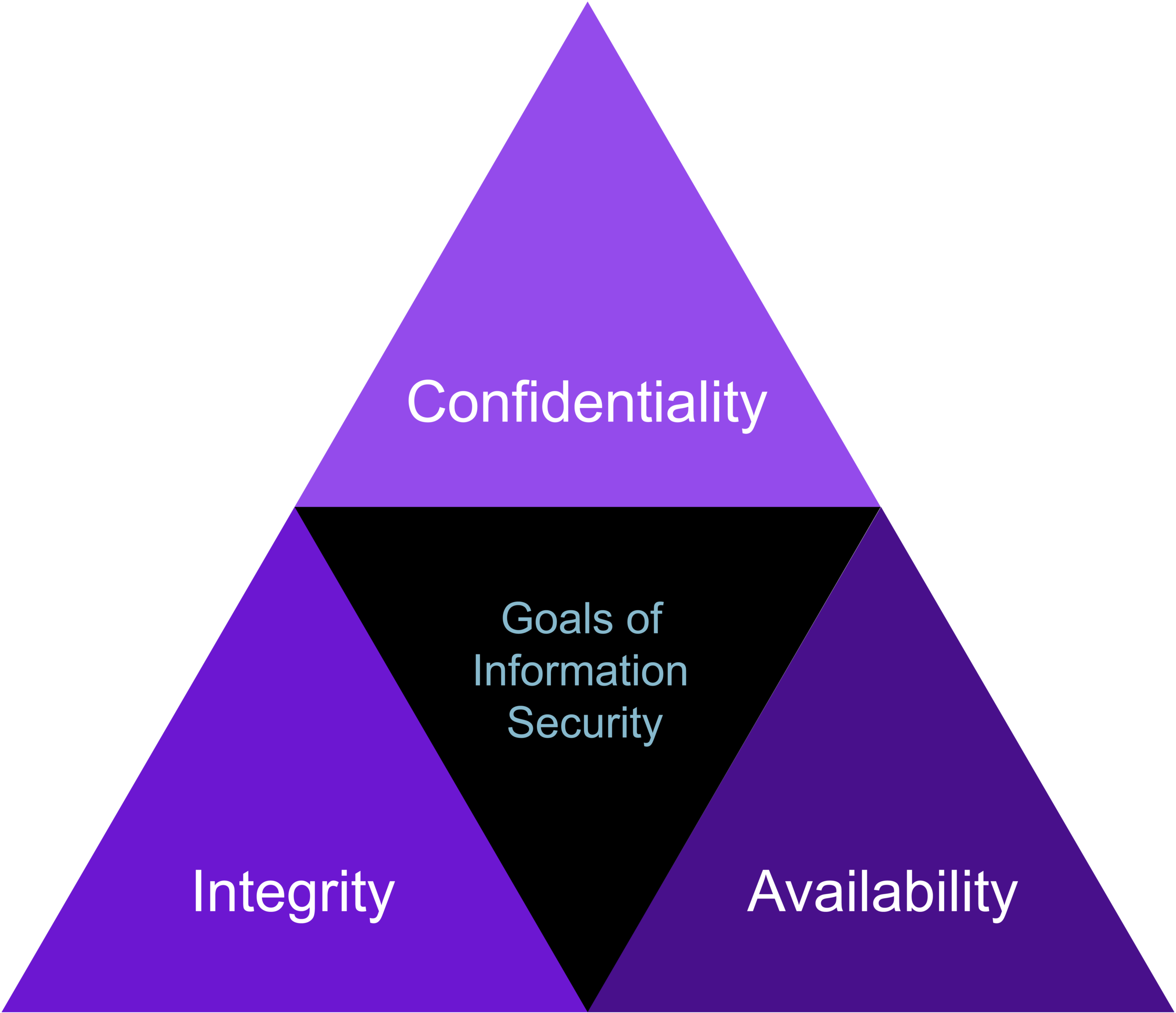
The elements of the CIA triad are as follows:
Confidentiality | Protects assets using important principles such as need-to-know and least privilege; prevents unauthorized disclosure. |
Integrety | Protects and adds value to assets by making them more accurate, timely, current, and meaningful; prevents unauthorized or accidental changes to assets such as information. |
Availability | Protects critical assets based on value to ensure organizational assets are available when required by stakeholders. |
The traditional pillars of security have been increased to include authenticity and nonrepudiation:
Authenticity | Proves assets are legitimate and bona fide and verifies that they are trusted and verified. Proves the source and origin of important, valuable assets. Also referred to as "proof of origin." |
Nonrepudiation | Assures that someone cannot dispute the validity of something; the inability to refute accountability or responsibility. Also, the inability to deny having done something. |
1.3 Evaluate and apply security governance principles
Alignment of the security function to business strategy, goals, mission, and objectives
The purpose of governance is to enhance organizational value, and corporate governance is based on the goals and objectives of the organization.
Security needs to enable the organization's goals and objectives, not just enforce information processes or fix technical issues, and must be managed top down instead of bottom up.
On the other hand, scoping and tailoring are used to align security objectives with organizational goals and objectives:
- Scoping looks at potential control elements and determines which ones are in scope—for example, security control elements that could adhere to applicable laws and regulations—and which ones are out of scope.
- Tailoring looks specifically at applicable—in scope—security control elements and further refines or enhances them so they're most effective and aligned with the goals and objectives of an organization.
Accountability versus responsibility
Accountable and responsible are two terms that are sometimes used mistakenly and interchangeably.
If someone is accountable for something, that accountability can never be delegated to anyone else. That person will always remain accountable. On the other hand, responsibility can be delegated, but the delegator will remain accountable.
Even if certain organization functions are managed by a responsible third party, like a payroll or Cloud Service Provider (CSP), accountability still resides with the owner of the assets being managed. A CSP will often have a contractual-based responsibility for protecting the data. Still, the data owner is always accountable for the data and, therefore, liable if there is a data breach.
Organizational roles and responsibilities
The following table outlines some of the key functions typically found in an organization and their accountabilities and responsibilities from a security perspective:
Owners / Controllers / Functional Leaders / Senior Management | Accountable for: |
|
Information Systems Security Professionals / IT Security Officer | Responsible for: |
|
Information Technology (IT) Officer | Responsible for: |
|
IT Function | Responsible for: |
|
Operator / Administrator | Responsible for: |
|
Network Administrator | Responsible for: |
|
Information Systems Auditors | Responsible for: |
|
Users | Responsible for: |
|
The responsibility for the corruption rests with the custodian. However, accountability for corruption rests with the asset owner.
Due care versus due diligence
Simply put:
- Due care is the responsible protection of assets
- Due diligence is the ability to prove due care
1.4 Determine compliance and other requirements
Establishing the right security controls isn't just about the internal needs of an organization. Plenty of contractual, legal, industry and regulatory requirements should inform how different assets are protected.
The legal, privacy, and audit/compliance functions must work together to ensure compliance, and once management understands compliance needs, they can work with security to implement controls.
1.5 Understand legal and regulatory issues that pertain to information security in a holistic context
Cybercrimes and data breaches
Every organization should be asking fundamental questions like:
- How is/are our information/assets protected?
- What are the issues pertaining to information security for our organization in a global context?
- What does the current threat landscape look like?
This is important because cybercrime is highly profitable. This fact explains why most organizations won't admit to being victims or prosecute the perpetrators of cybercrime.
Not every attack can be prevented, but effective security strategies can reduce attacks by making them:
- Not worthwhile
- Too time-consuming
- Too expensive
Bottom line: Don't be the low-hanging fruit that can be easily picked!
Licensing and intellectual property requirements
Intellectual property laws aim to encourage the creation of intellectual goods (inventions, literary and artistic works, designs, symbols, and names) and to protect the same.
The following table will show what trade secrets, patents, copyrights, and trademarks protect.
Term | Protects | Disclosure Required | Term of Protection | Protects Against |
|---|---|---|---|---|
Trade Secret | Business information | No | Potentially infinitive | Misappropriation |
Patent | Functional innovations, novel idea, inventions | Yes | Set period | Making, using, or selling an invention |
Copyright | Expression of an idea embodied in a fixed medium (books, movies, songs, etc.) | Yes | Set period of time | Copying or substantially similar work |
Trademark | Color, sound, symbol, etc. used to distinguish one product/company from another | Yes | Potentially infinitive | Creating confusion |
Import/export controls
Import and export controls are country-based rules and laws implemented to manage which products, technologies, and information can move in and out of those countries, usually meant to protect national security, individual privacy, economic well-being, and so on.
The Wassenaar Arrangement
The Wassenaar Arrangement was put in place to manage the risk that cryptography poses while still facilitating trade. It allows certain countries to exchange and use cryptography systems of any strength while also preventing the acquisition of these items by terrorists.
International Traffic in Arms Regulations (ITAR)
This is a US regulation that was built to ensure control over any export of items such as missiles, rockets, bombs, or anything else existing in the United States Munitions List (USML).
Export Administration Regulations (EAR)
EAR predominantly focuses on commercial use-related items like computers, lasers, marine items, and more. However, it can also include items that may have been designed for commercial use but actually have military applications.
Transborder data flow
Transborder data flow laws restrict the transfer of data across country borders. When sharing data across borders, applicable laws must be considered.
These laws primarily relate to personal data. The idea is to protect a country/state/province/region's citizens' personal data. If an organization is collecting citizens' data, then they are accountable for the protection of that data.
Given these laws, organizations must consider the potential implications of the flow of data across physical borders. This can be very challenging for organizations to keep track of with the proliferation of service providers and global cloud services.
Privacy
Privacy is the state or condition of being free from being observed or disturbed by other people, and personal data is information on its own or in combination that uniquely identifies an individual.
It's essential that personal data is well protected to comply with current privacy laws and to protect the value of the information and of the organization itself. This can become complex for multinational organizations since there's a significant variation around the world in both the definition of personal data and the laws that determine how to protect it.
Personal data
Depending on the location in the world, personal data may be referred to in different ways, and what constitutes personal data can vary significantly.
Personal data can be referred to as:
- PI: Personal Information
- PII: Personally Identifiable Information
- SPI: Sensitive Personal Information
- PHI: Personal Health Information
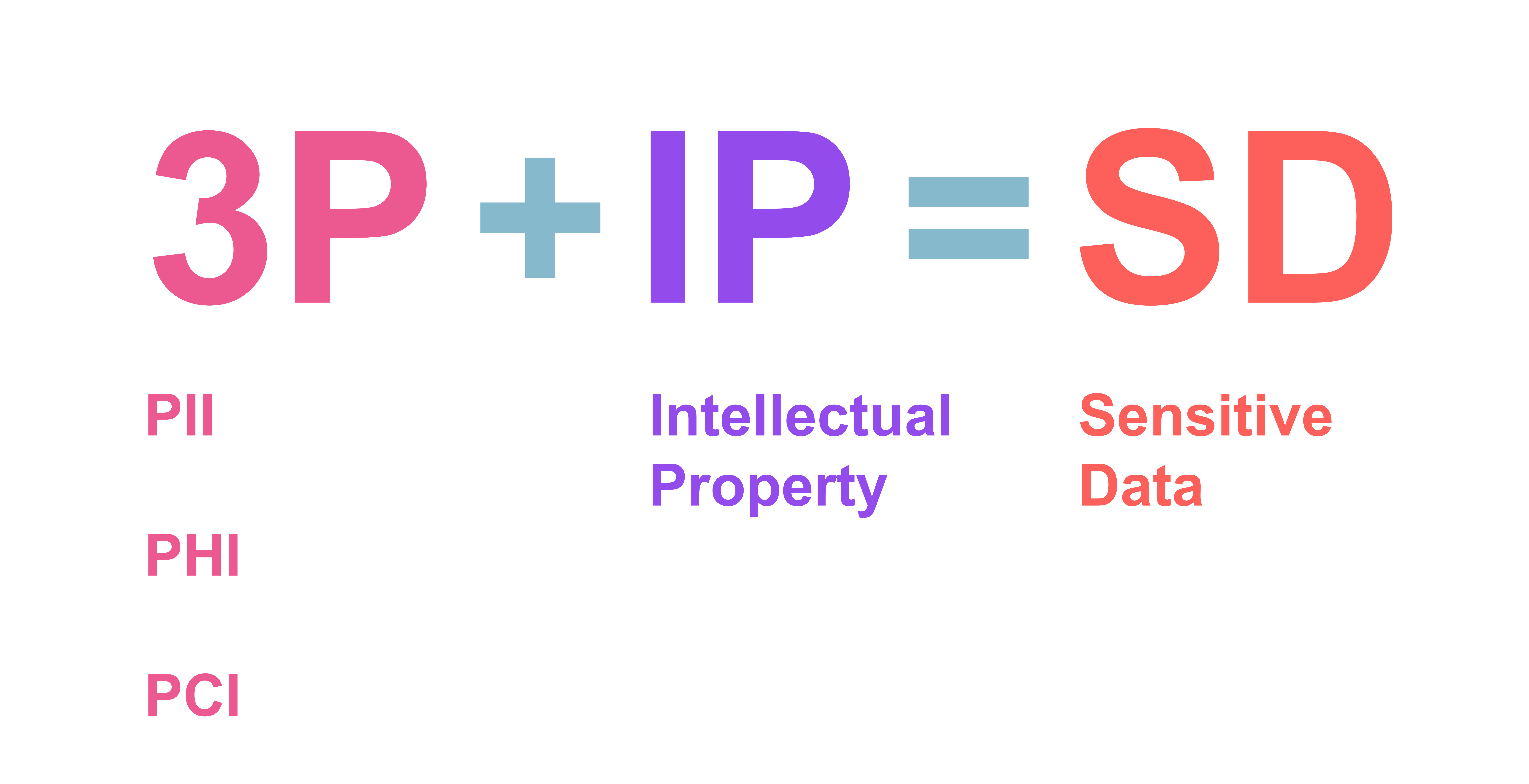
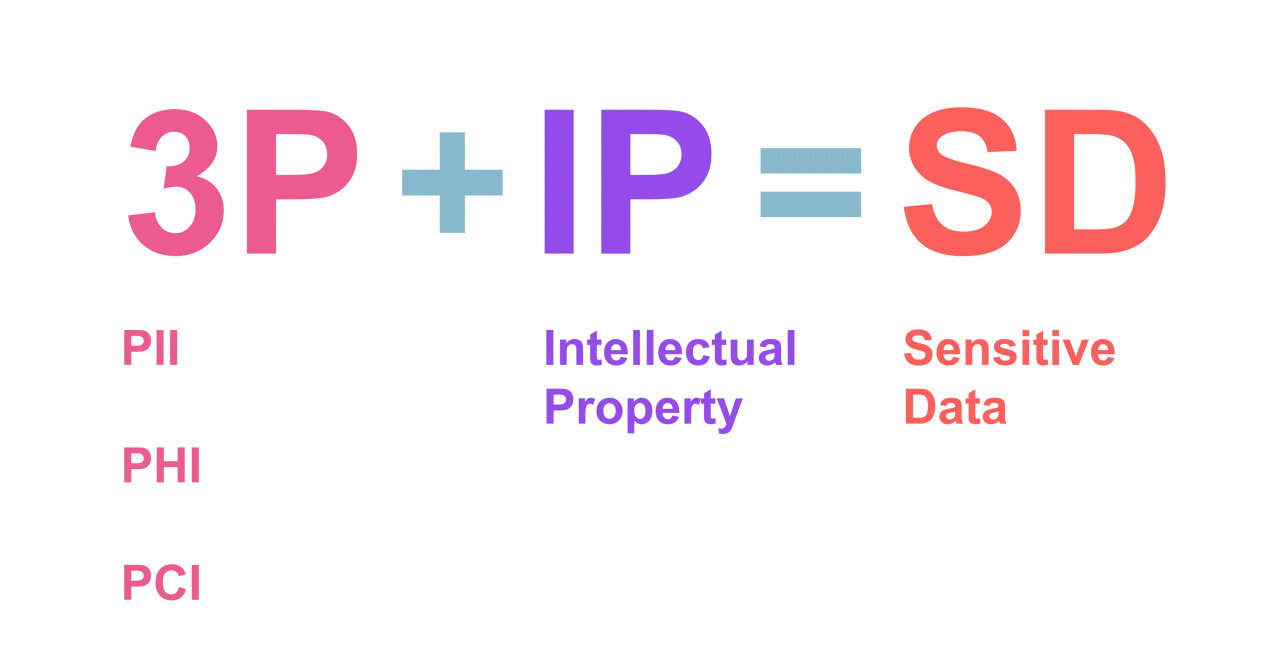
On the other hand, it's important to distinguish between direct identifiers, which include information that relates specifically to an individual, such as their name, address, biometric data, government ID, or other uniquely identifying numbers, while indirect identifiers include information that on its own cannot uniquely identify an individual but can be combined with other information to identify specific individuals.
Privacy requirements
Privacy policy requirements
The following table contains a summary of the key roles within the privacy realm:
Data owners | Owners need to have clearly defined accountabilities, including:
Different types of owners:
Companies that collect personal data about customers are accountable for the protection of the data |
Data custodians | Need to have clearly defined responsibilities. And who provides all this. Typically, the owners. |
Data processors | Need to have clearly defined responsibilities. Protects critical assets based on value to ensure organizational assets are available when required by stakeholders. |
Data subjects | Individuals to whom personal data relates. |
One privacy law that you should have a deeper understanding of is the GDPR, which is one of the most comprehensive privacy laws in the world, and many countries have modeled or are in the process of modeling their privacy laws on GDPR or plan to in the future.
OECD privacy guidelines
The Organization for Economic Cooperation and Development (OECD) is an international organization that is focused on international standards and policies and finding solutions to social, economic, and environmental challenges. One such challenge that they have been driving for decades is privacy.
OECD privacy guidelines are not mandatory for organizations to comply with, although they are considered a prudent course of action. These guidelines are:
- Collection limitation principle
- Data quality principle
- Purpose specification principle
- Use limitation principle
- Security safeguards principle
- Openness principle
- Individual participation principle
- Accountability principle
Privacy assessments
Privacy Impact Assessment (PIA) is a process undertaken on behalf of an organization to determine if personal data is being protected appropriately and to minimize risks to personal data where appropriate.
A PIA is performed with the goal to:
- Identify/evaluate risks relating to privacy breaches.
- Identify what controls should be applied to mitigate privacy risks.
- Offer organizational compliance with privacy legislation.
These are the PIA steps:
- Identify the need for a DPIA
- Describe the data processing
- Assess necessity and proportionality
- Consult interested parties
- Identify and assess risks
- Identify measures to mitigate the risks
- Sign off and record outcomes
- Monitor and review
1.6 Understand requirements for investigation types
To understand the requirements for investigation types, read our domain 7 article (section 7.1.7), in which we explain everything you need to know in this regard.
1.7 Develop, document, and implement security policies, procedures, standards, baselines, and guidelines
Policies, procedures, standards, baselines, and guidelines
The compendium of functional policies will be defined, supported, and informed by many standards, procedures, baselines, and guidelines, as seen in the following model:
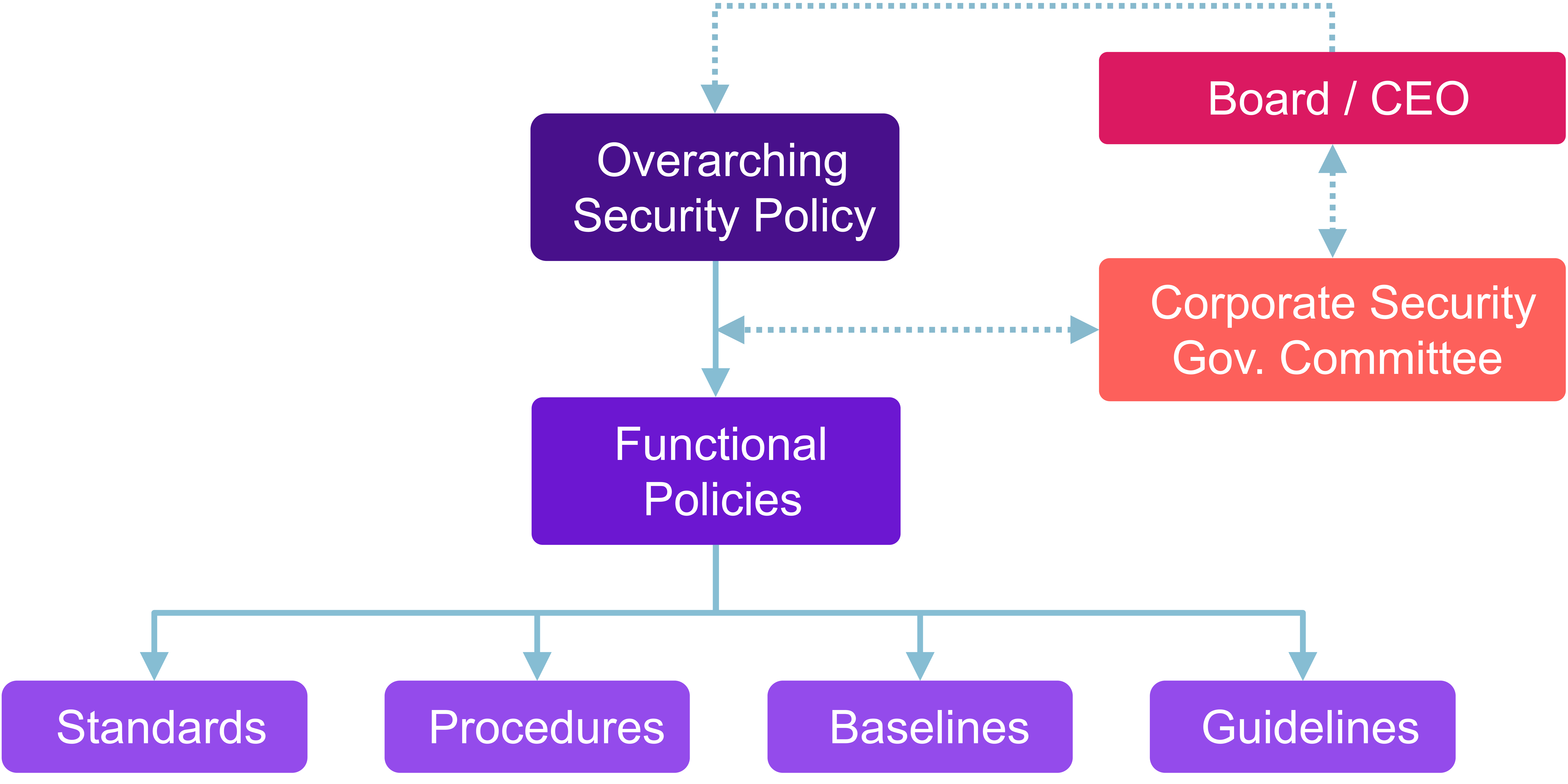
For the CISSP certification exam, you must be aware of the differences between policies, procedures, baselines, and guidelines:
Policies |
|
Standards | Specific hardware and software solutions, mechanisms, and products Examples:
|
Procedure | Step-by-step descriptions on how to perform a task; mandatory actions Examples:
|
Baselines | Defined minimal implementation methods/levels for security mechanisms and products Examples:
|
Guidelines | Recommended or suggested actions Examples:
(Note: Guidelines allow an organization to suggest something be done without making it a hard requirement and thus cause a negative audit finding.) |
The committee, reporting to the Board of Directors and CEO, should develop an overarching security policy that is aligned with organizational goals and objectives that covers the entire organization and clearly articulates the goals and objectives of the security function.
While policies don't need to be reviewed every year, standards, procedures, baselines, and guidelines may need to be updated frequently.
1.8 Identify, analyze, and prioritize business continuity (BC) requirements
Please check section 7.11 of our article on Domain 7 to know more about this topic.
1.9 Contribute to and enforce personnel security policies and procedures
Personal security policies
Some of the best practices for protecting the business and its important assets are listed below.
Candidate screening and hiring
New personnel represents a risk to security; every organization needs personnel security policies that address and mitigate this risk with the right security controls.
Employment agreements and policies
As part of bringing a new employee into an organization—also referred to as onboarding—company security policies, acceptable use policies, and similar agreements should be reviewed and agreed upon prior to giving a new employee their badge and any system credentials.
Prior to an employee leaving, or in conjunction with it, user system access should be disabled, and the fact that the employee's employment is being terminated should be conveyed to all relevant parties within the organization.
Employee duress
An employee acting under duress may be forced to perform an action or set of actions that they wouldn't do under normal circumstances. One common practice to handle these stressful situations is to have keywords that denote that an employee is acting under duress.
Personnel security controls
Here is a list of important personnel security controls:
- Job rotation. Job rotation is quite useful for protecting against fraud and provides cross-training. It entails rotating staff (especially individuals in key positions) so that an individual can't commit fraud and cover it up.
- Mandatory vocation. Mandatory vacation is a control also used by organizations to detect fraud. Employees are required to go on vacation for a set period of time, during which time another employee can step into the role and determine if any malicious or nefarious activity has taken place or is actively taking place.
- Separation of duties. Separation of duties is used to prevent fraud by requiring more than one employee to perform critical tasks.
- Need-to-know and Least privilege. Least privilege ensures that only the minimum permissions needed to complete the work are granted to any employee. Need to know ensures that access to sensitive assets is restricted only to those who require the information to complete the work.
Enforce personnel security controls
Enforcing personnel security controls commences with the hiring process, extends through the employment period, and ends only after the employee has left the organization.
Additionally, personnel-focused policies are often further supported by things like:
- Nondisclosure agreements (NDA). Contracts through which the parties agree not to disclose information covered by the agreement.
- Noncompete agreements (NCA)
- Ethical guideline and requirement questionnaires and agreements
- Vendor, consultant, and contractor agreements and controls
1.10 Understand and apply risk management concepts
Risk management
Risk management is the identification, assessment, and prioritization of risks and the economical application of resources to minimize, monitor, and control the probability and/or impact of these risks.
Here's an overview of the risk management process:
- Value. identifying the assets of the organization and ranking those assets from most to least valuable. This process is referred to as asset valuation, and the ranking of assets can be achieved via two methods or, most commonly, a combination of both quantitative value analysis and qualitative value analysis.
- Risk analysis. Determine the risks associated with each asset via the risk analysis process. The four key components are threat, vulnerability, impact, and probability/likelihood.
- Treatment. There are four risk treatment methods: avoid, transfer, mitigate, and accept.
Asset valuation
Before risks can be identified and managed, valuable assets of the organization must first be identified.
Two different forms of analysis can be used to rank the assets of the organization from most to least valuable: qualitative and quantitative:
Qualitative analysis | Quantitative analysis |
|---|---|
Does not attempt to assign monetary value | Assign objective monetary values |
Relative ranking system, based on professional judgment | Fully quantitative process when all elements are quantified |
Uses words like "Low," "Medium," "High," "1–5," "Probability," or "Likelihood" to express value | Cell |
Qualitative analysis is relatively simple and efficient | Purely quantitative is difficult to achieve and time-consuming |
Risk analysis
After the asset valuation process, related threats and vulnerabilities must be identified for each asset, and owners must be deeply involved in the risk analysis process.
Threats and vulnerabilities
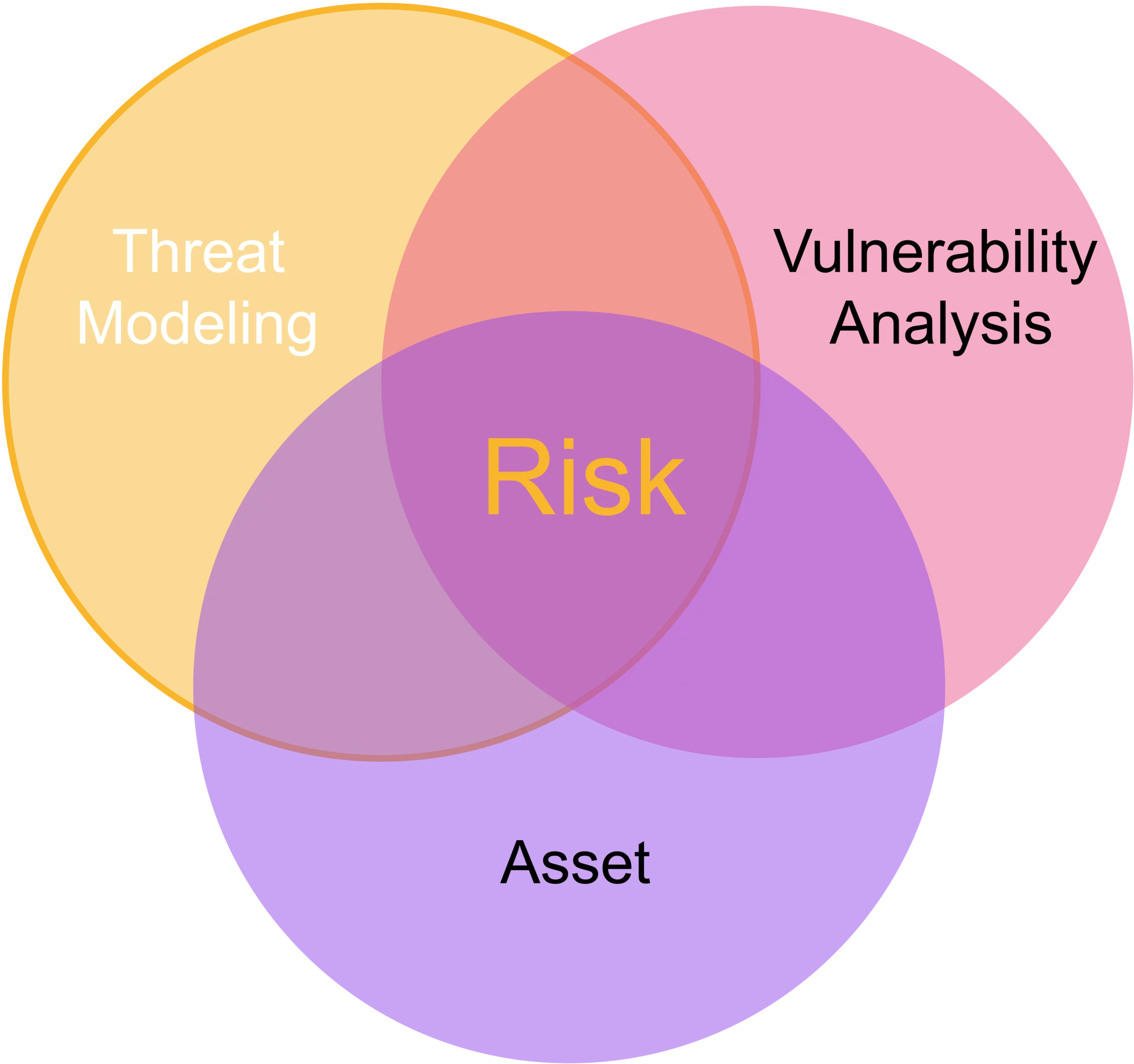
There are three main components to risk being present:
- Asset: anything of value to the organization
- Threat: any potential danger; anything that causes damage to an asset, like hackers, earthquakes, ransomware, social engineering, denial-of-service attacks, disgruntled employees, and many others.
- Vulnerability: a weakness that exists; anything that allows a threat to take advantage of it to inflict damage to the organization. Examples include open ports with vulnerable services, lack of network segregation, lack of patching, and OS updating.
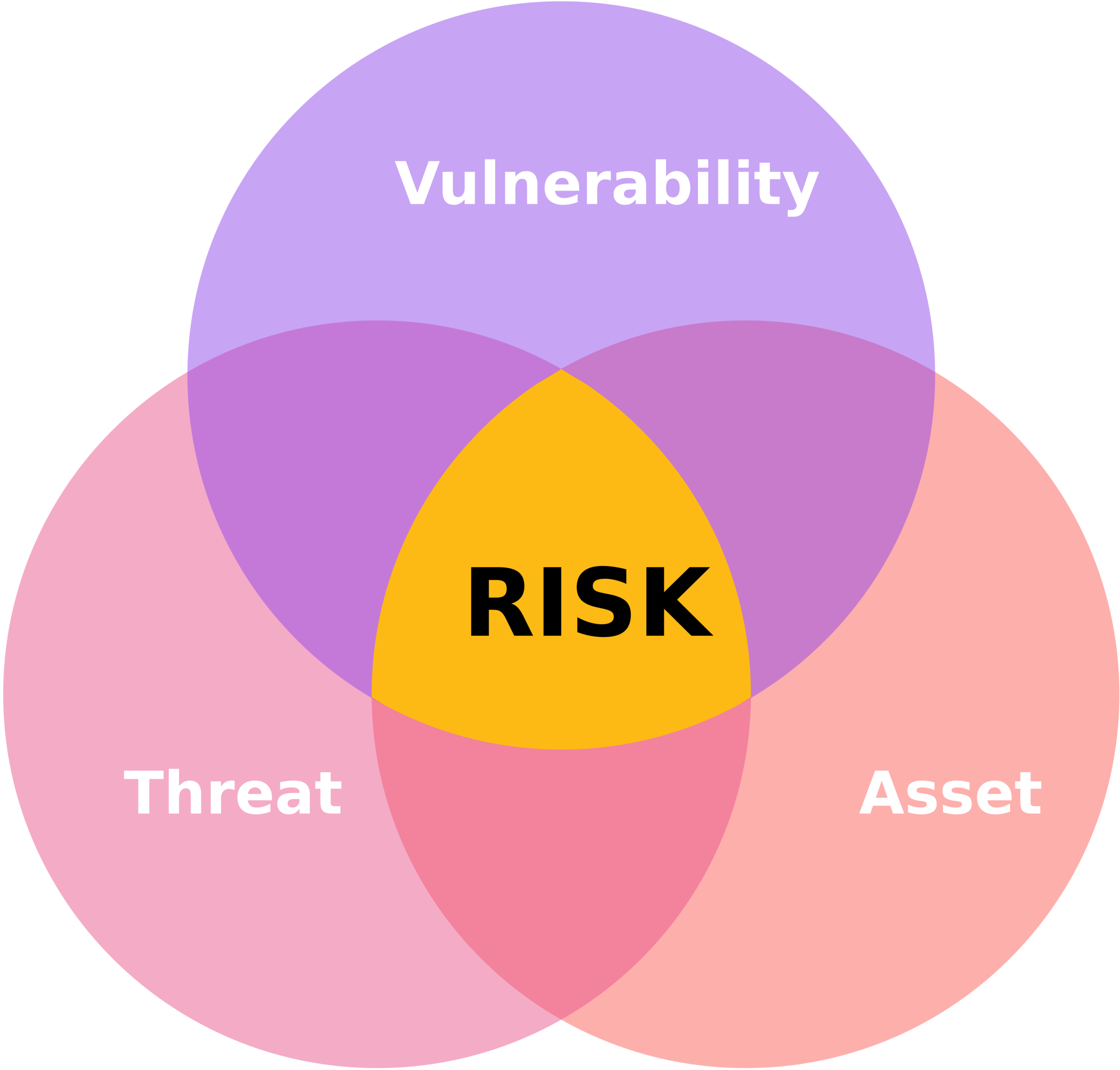
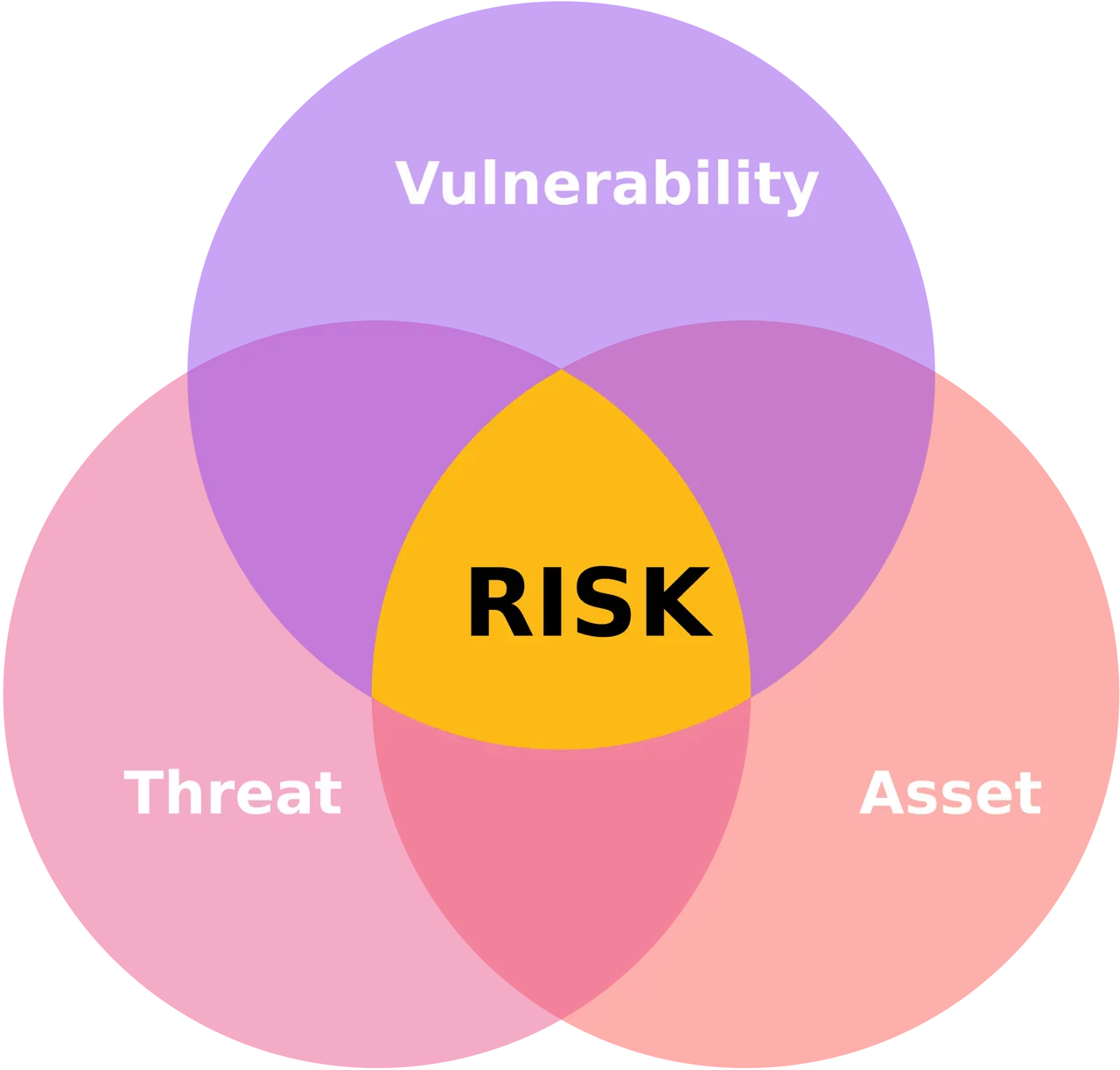
Risk management terms
The following list contains a list of core terms used in risk management and how they fit together.
Threat Agent | The entity that has the potential to cause damage to an asset (e.g., external attackers, internal attackers, disgruntled employees) |
Threat | Any potential danger |
Attack | Any harmful action that exploits a vulnerability |
Vulnerability | A weakness in an asset that could be exploited by a threat |
Risk | Significant exposure to a threat or vulnerability (a weakness that exists in an architecture, process, function, technology, or asset) |
Asset | Anything that is valued by the organization |
Exposure/Impact | Negative consequences to an asset if the risk is realized (e.g., loss of life, reputational damage, downtime, etc.) |
Countermeasures and Safeguards | Controls implemented to reduce threat agents, threats, and vulnerabilities and reduce the negative impact of a risk being realized |
Residual Risk | The risk that remains after countermeasures and safeguards (controls) are implemented |
Annualized Loss Expectancy (ALE) calculation
Quantitative analysis as part of ranking risks requires calculating how much risk is expected to cost the organization annually—the Annualized Loss Expectancy (ALE). The ALE can be calculated using this formula:
ALE = SLE (AV x EF) x ARO
The acronyms pertain to:
- Asset Value (AV)
- Exposure Factor (EF)
- Single Loss Expectancy (SLE)
- Annualized Rate of Occurrence (ARO)
- Annualized Loss Expectancy (ALE)
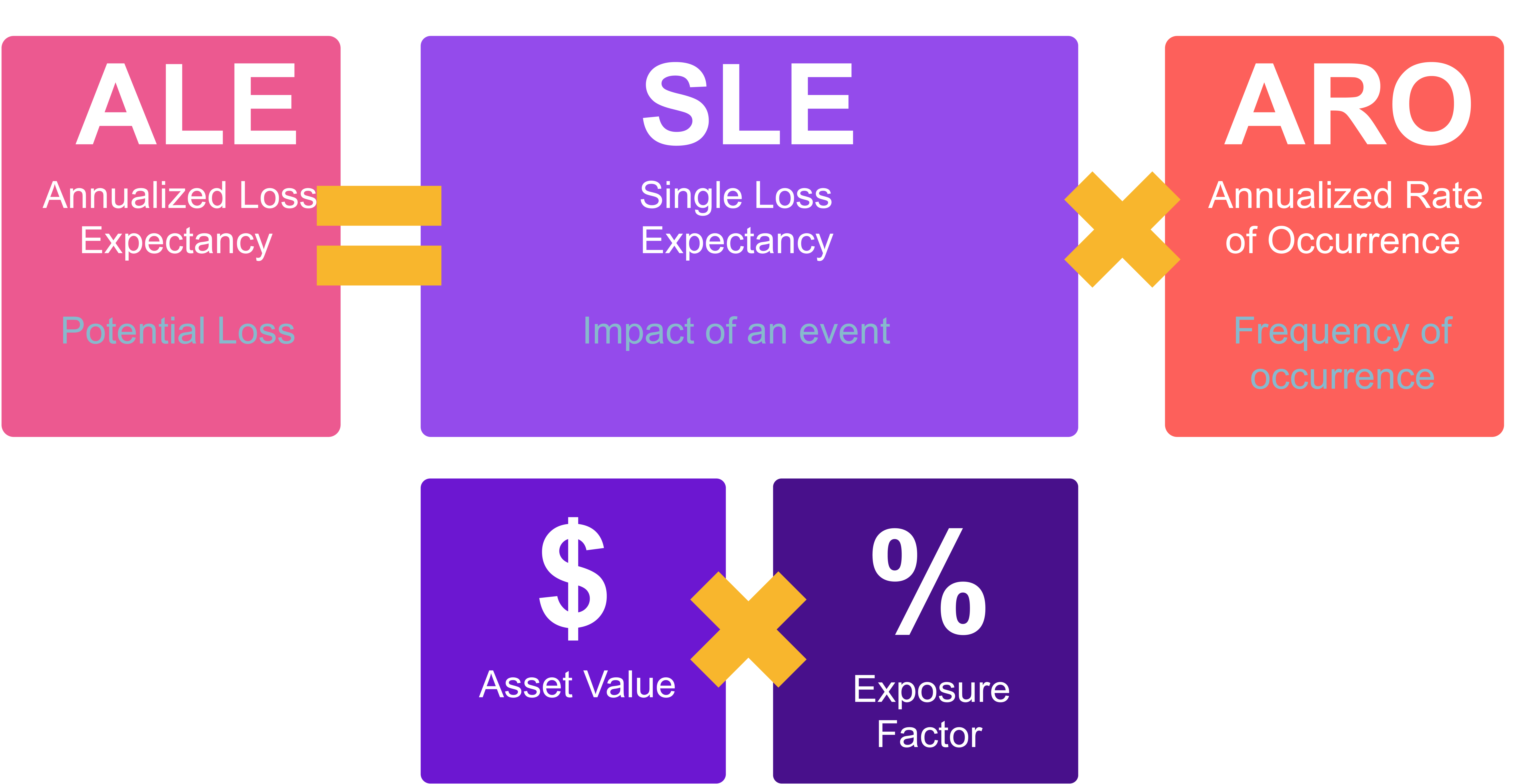
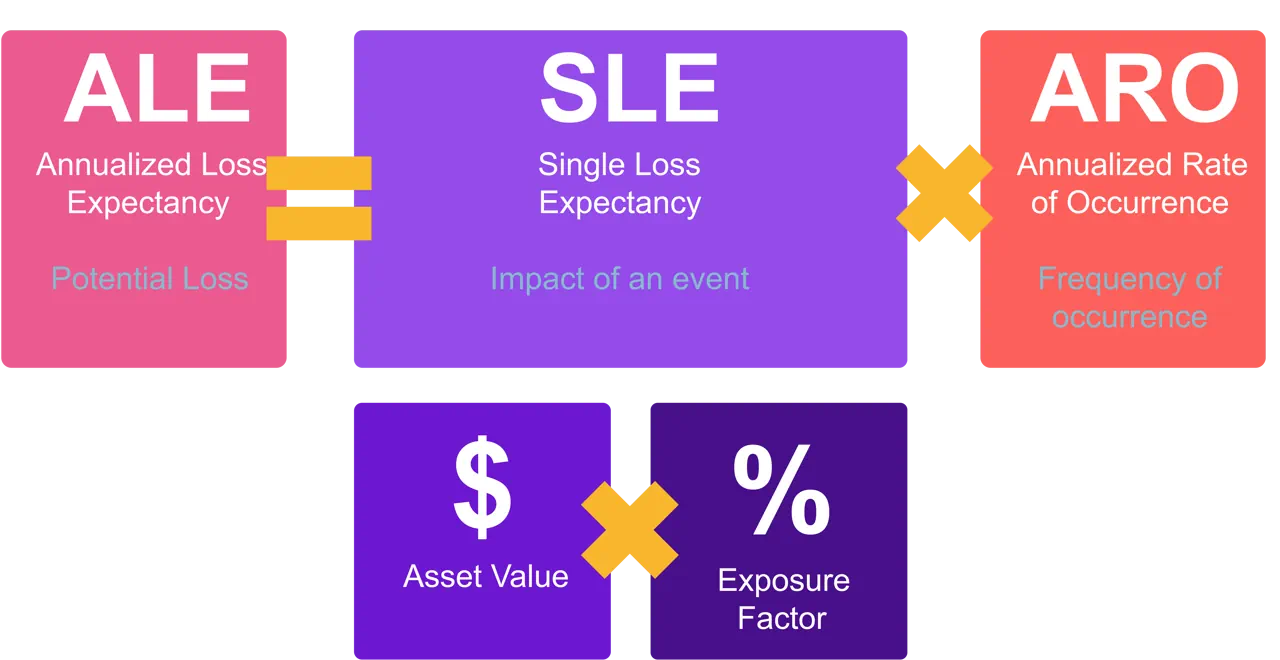
Risk response/ treatment
After the risk analysis process, security should implement the most cost-effective treatments. The right approach depends on the value of the asset and the type of risk identified in the previous steps.
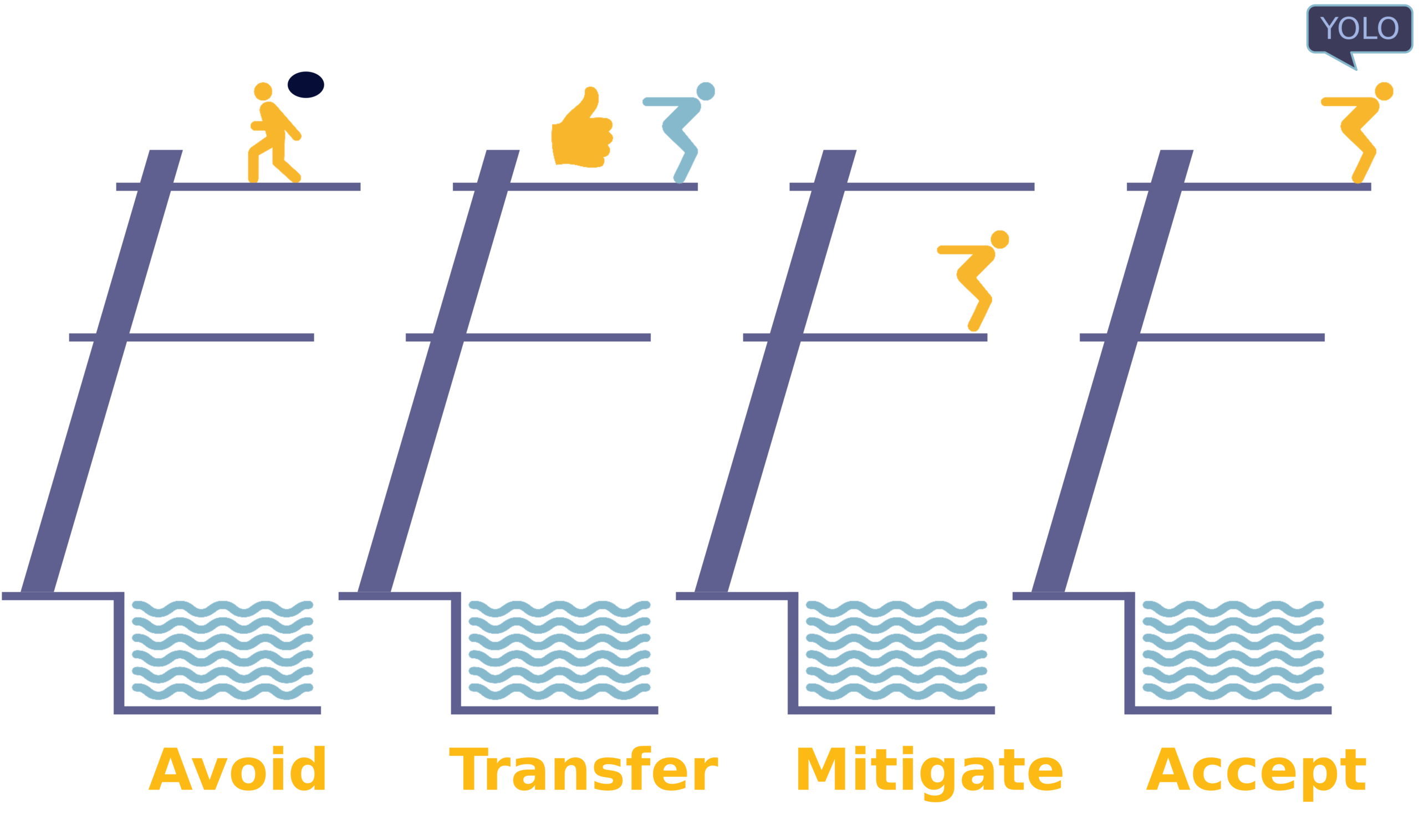
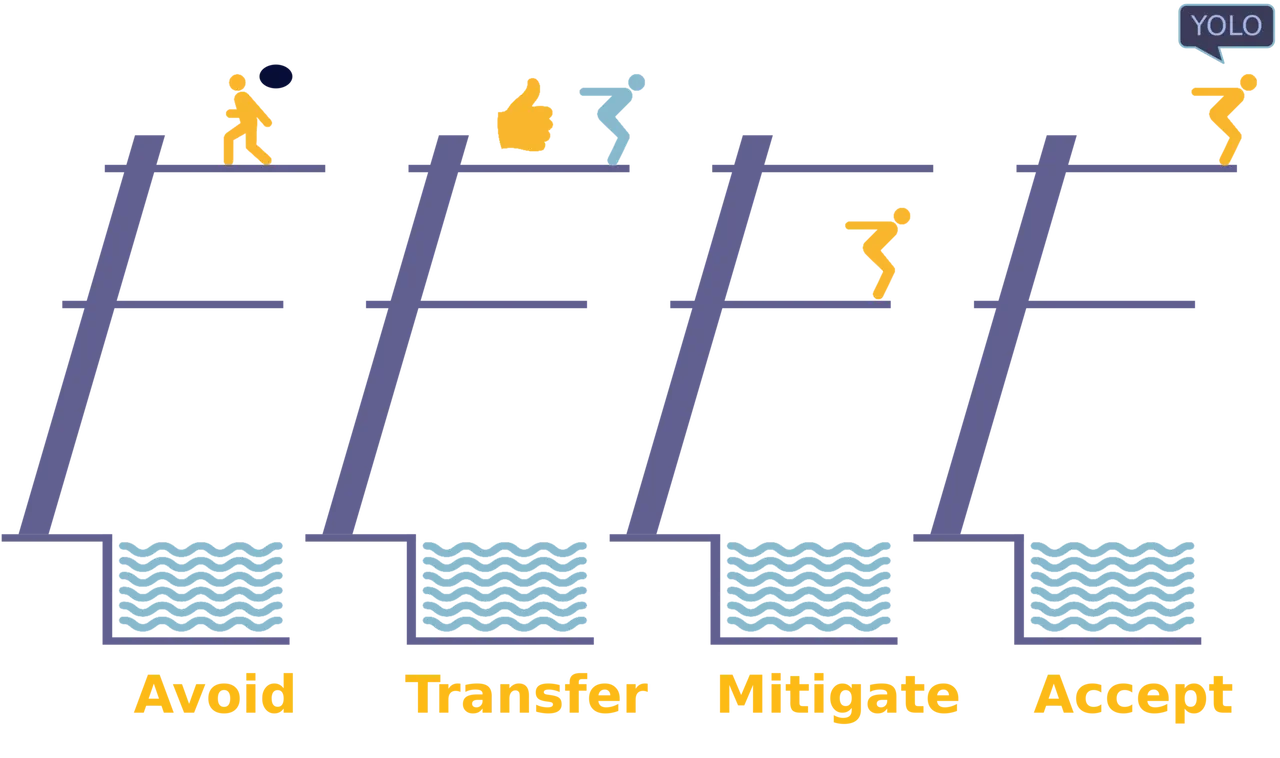
Although risk can never be entirely eliminated, it can be managed via the following approaches:
- Avoid. Choosing to stop doing whatever exposes the asset to risk. Not jumping can avoid the risk, but you can miss significant opportunities (the opportunity cost).
- Transfer. Transferring risk means sharing some risk with another party, usually an insurance company.
- Mitigate. Mitigate risk means implementing controls that reduce the risk to an acceptable level.
- Accept. Accepting risk simply means taking no action or no further action where the risk to a particular asset is concerned.
Types of controls
Seven major types of controls can be put in place, as shown in the following table:
Directive | Directive controls direct, confine, or control the actions of subjects to force or encourage compliance with security policies. |
Deterrent | Deterrent controls discourage violation of security policies |
Preventive | Preventive controls can prevent undesired actions or events |
Detective | Detective controls are designed to identify if a risk has occurred. Importantly, detective controls operate after an event has already happened |
Corrective | Corrective controls are used to minimize the negative impact of a risk occurring—minimize the damage. They are used to alleviate the effects of an event that has resulted in a loss and to respond to incidents to minimize risk. |
Recovery | Restore to normal |
Compensating | Make up for lack (e.g. supervision) |
A concept that is pervasively used in security is complete control. Complete control is a combination of preventive, detective, and corrective controls at a minimum.
In addition, in defense-in-depth (layered security), complete control should be implemented at each layer.
Categories of controls
A way to categorize the security controls is as safeguards or as countermeasures.
Safeguards are proactive controls; they are put in place before the risk has occurred to deter or prevent it from manifesting.
Countermeasures are reactive controls. They are put in place after risk has occurred and aim to allow us to detect and respond to it accordingly.
Controls can be further classified into three main categories:
- Administrative
- Logical/Technical
- Physical
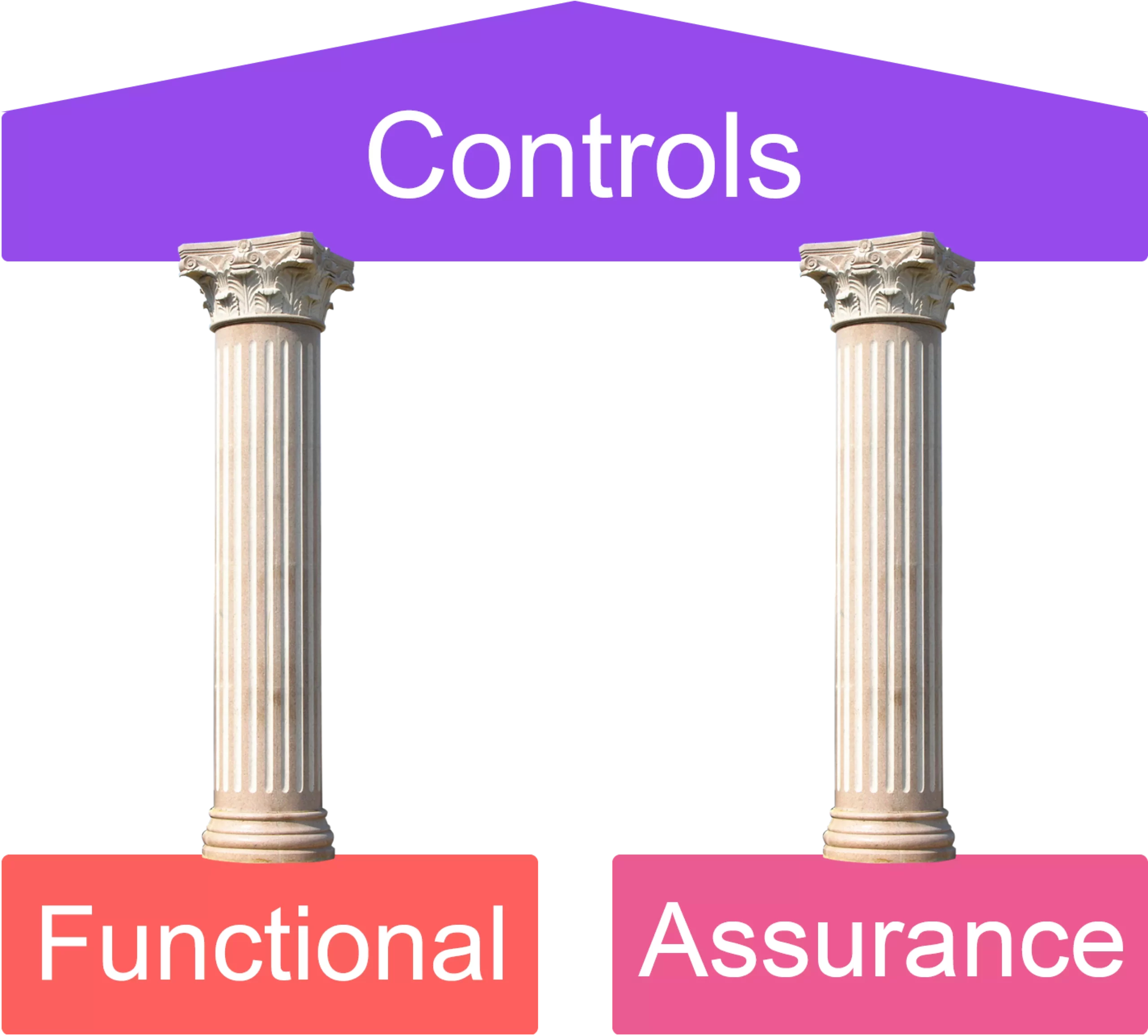
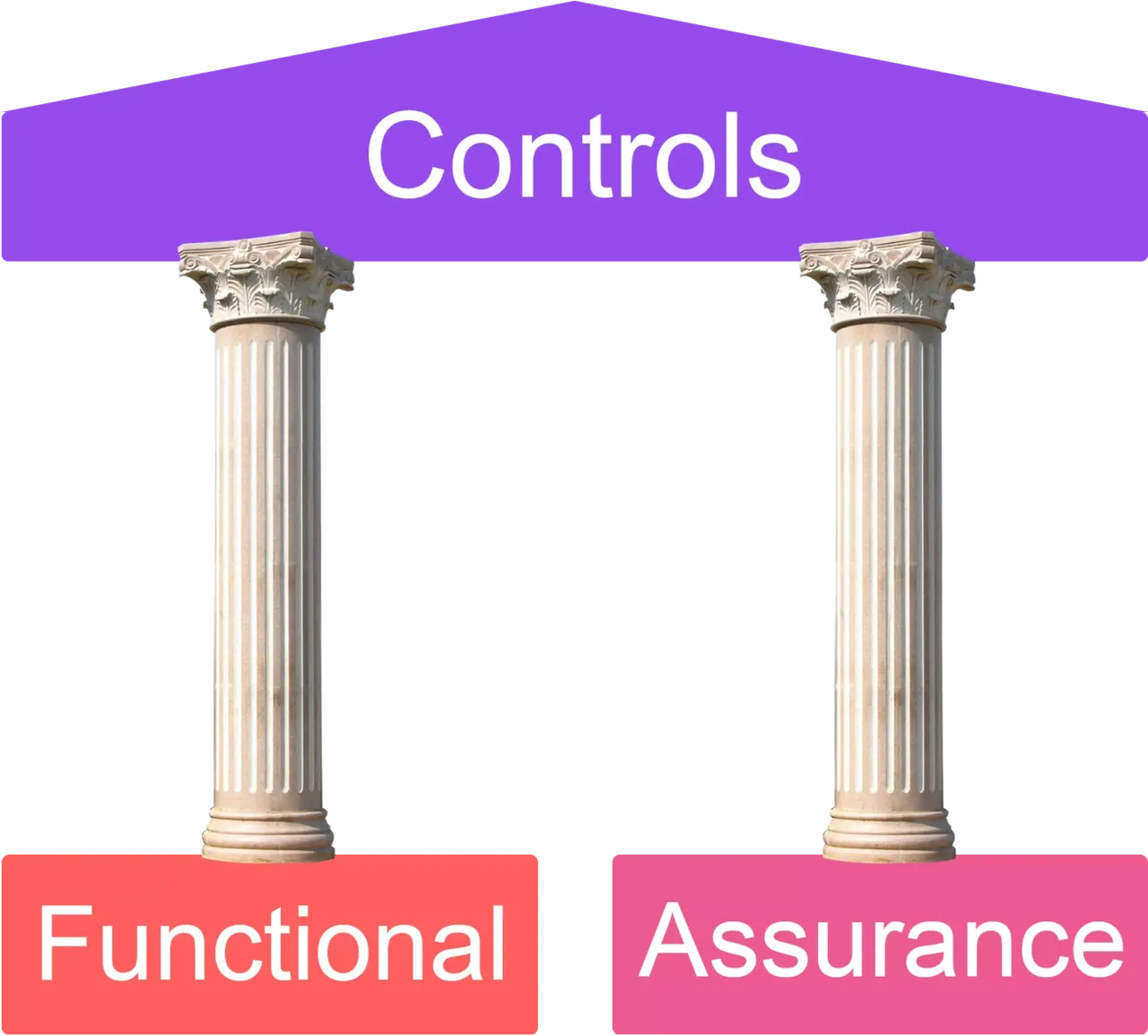
Functional and assurance
A good security control should always include two aspects: the functional aspect and the assurance aspect.
Functional | Assurance |
|---|---|
Control performs the function it was designed to address/does what it is meant to do—for example, a firewall filtering traffic between different subnets. | Control can be proven to be functioning properly on an ongoing basis, usually proven through testing, assessments, logging, monitoring, etc. |
Selecting controls
Selected controls must support organizational goals and objectives and be cost-effective.
Security is usually a balancing act between achieving the maximum level of security with the least cost and, at the same time allowing proper functionality.
Security controls make systems more difficult to use, slower, more complicated, and so on.
Measuring control effectiveness and reporting
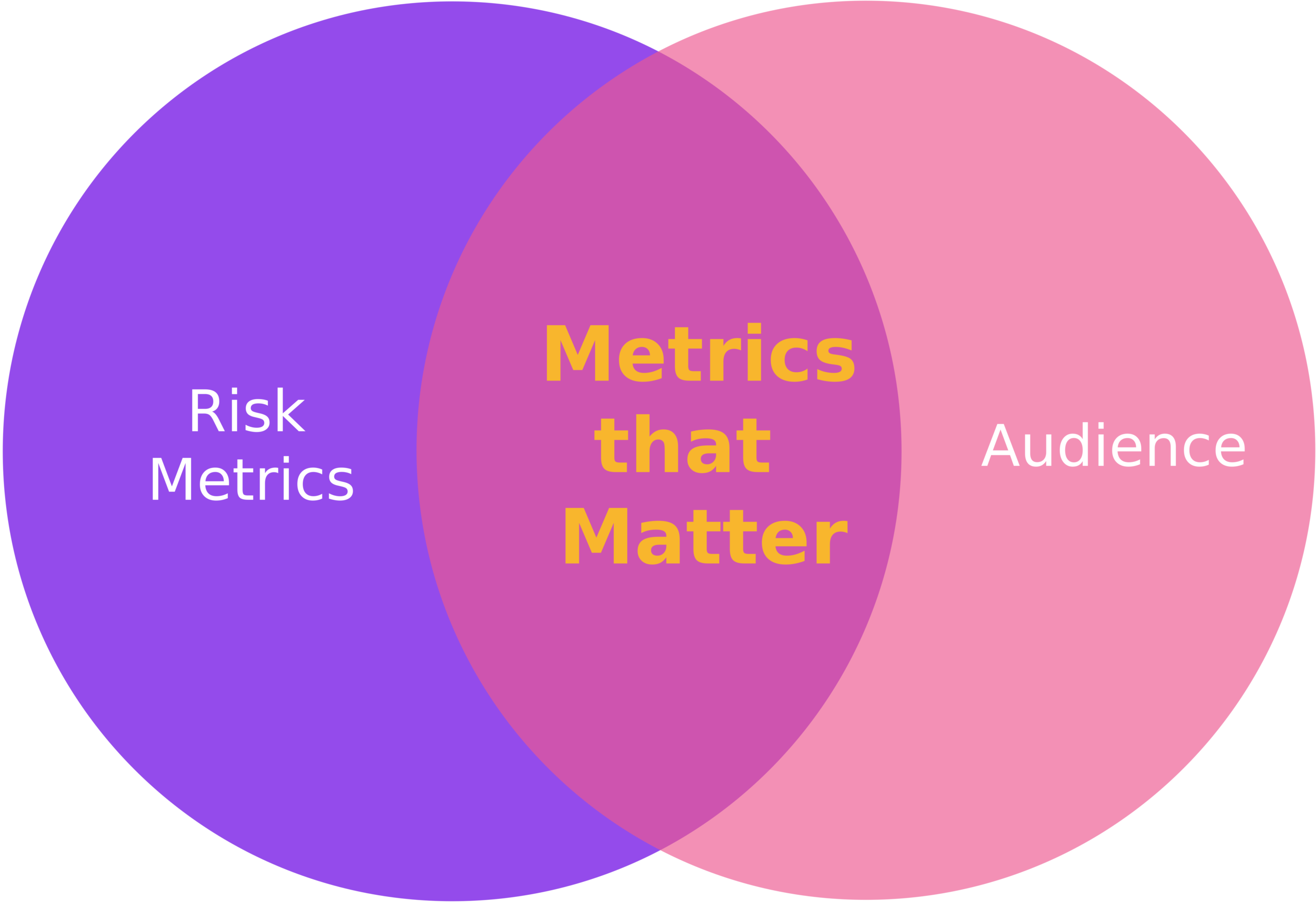
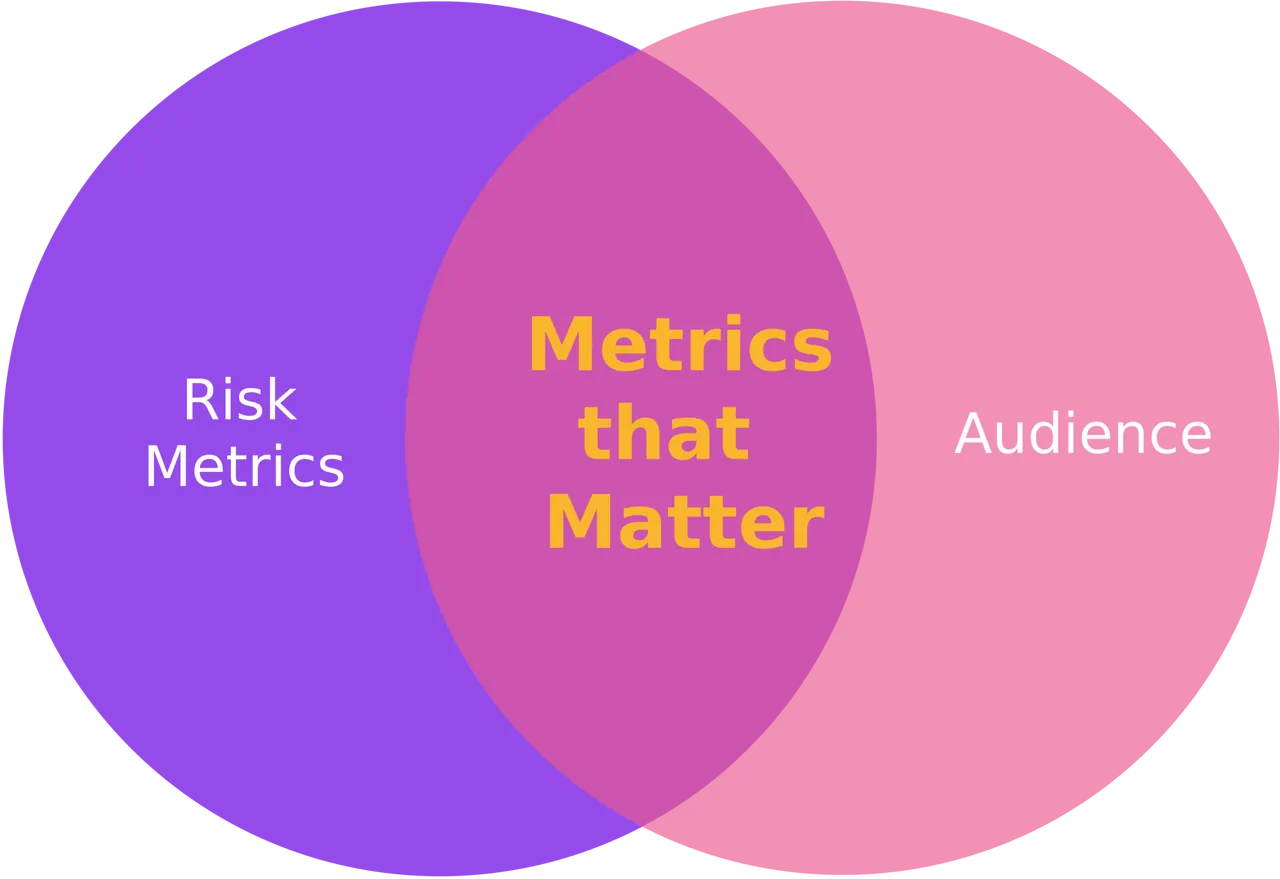
Once a control, or set of controls, has been decided upon and implemented, it is important to understand how well they're working. One of the best ways to do this is by using metrics.
To identify the metrics that will matter, the metrics that will be useful to implement and monitor, and the target audience must be identified.
Continuous improvement
Risk management is a continuous, arduous, and time-consuming process that needs to be continually updated.
The Deming Cycle, sometimes also referred to as Plan Do Check Act (PDCA), shown in the next figure, outlines the cyclical nature of many processes in security, including risk management.
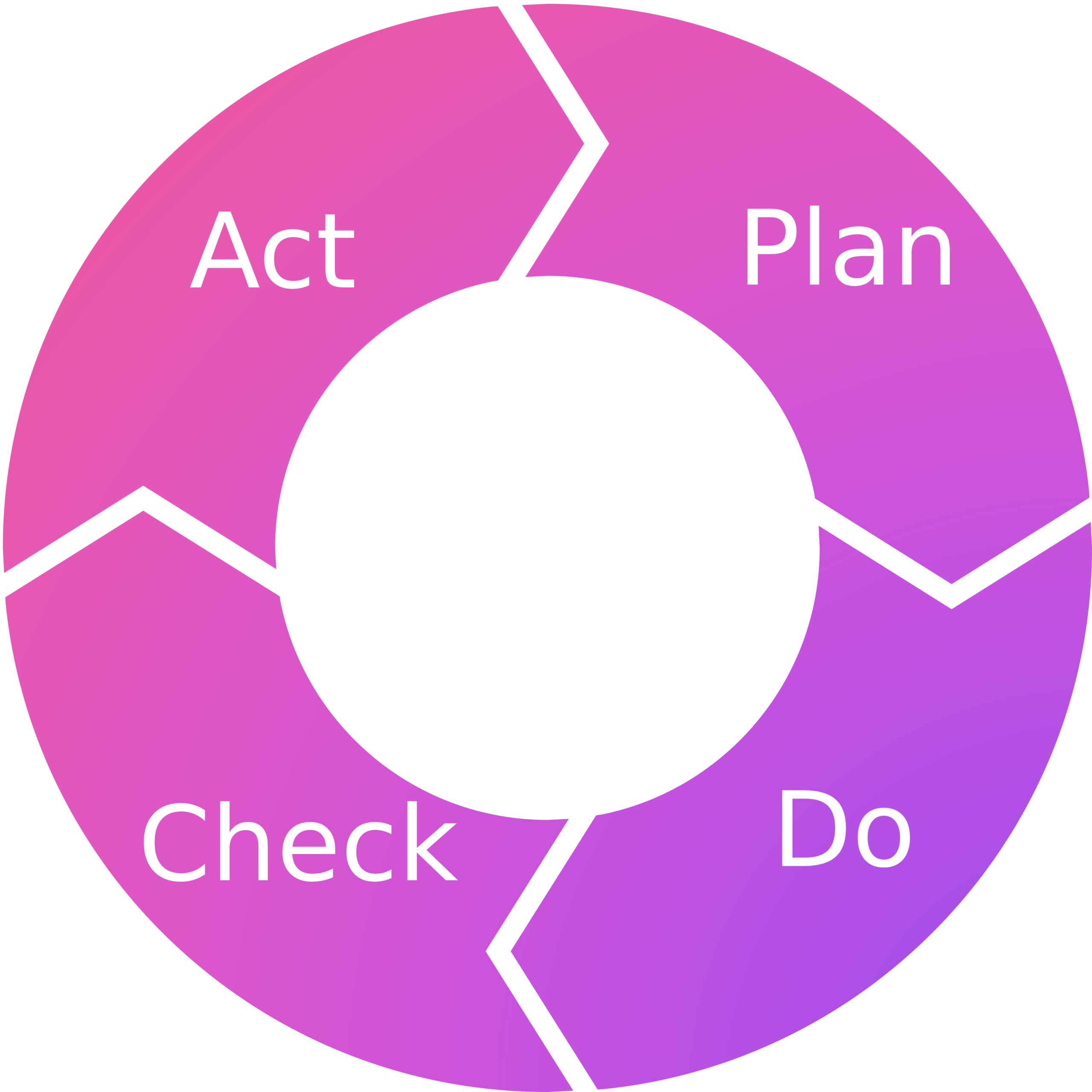
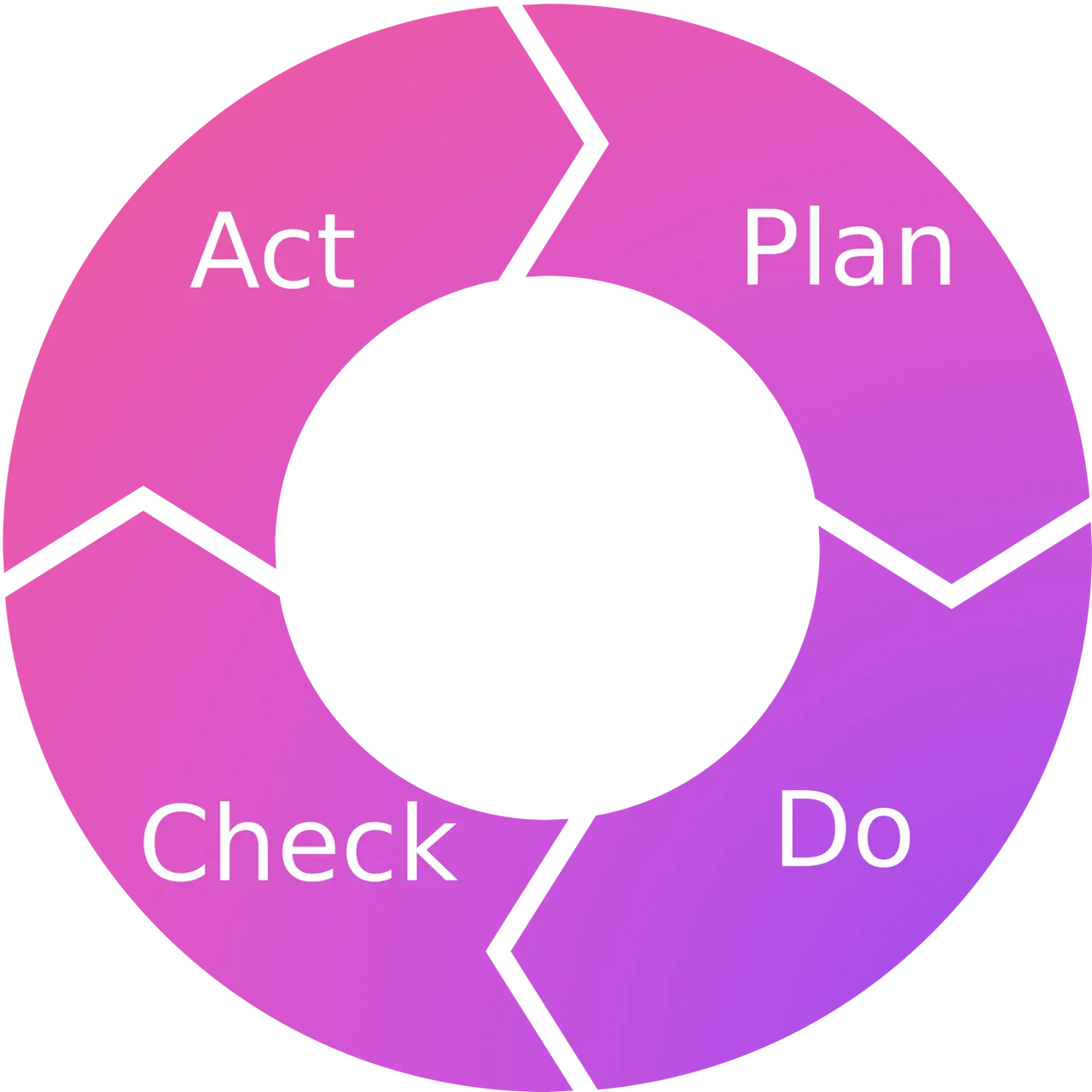
Plan | Determine which controls to implement based on the risks identified |
Do | Implement the controls |
Check | Monitoring and assurance; are the controls operating effectively? |
Act | Based upon findings during the "Check" step, take additional actions as necessary (react), which leads back to planning |
Apply supply chain risk management concepts
Risk management methodologies should be applied to all vendors, suppliers, and service providers, and it should include the following items:
- Governance review
- Site security review
- Formal security audit
- Penetration testing
- Adherence to the security baseline
- Evaluation of hardware and software
- Adherence to security policies
- Development of an assessment plan
- Identification of assessment requirements and which party will perform it
- Preparation of assessment and reporting templates
Risk management frameworks
Risk management frameworks provide comprehensive guidance for structuring and conducting risk management. The four risk management frameworks are shown in the following table:
NIST SP 800-37 (RMF) | This guide describes the risk management framework (RMF) and provides guidelines for applying the RMF to information systems and organizations. |
ISO 31000 | ISO 31000 is a family of standards relating to risk management. |
COSO | COSO provides a definition of essential enterprise risk management components, reviews ERM principles and concepts, and provides direction and guidance for enterprise risk management. |
ISACA Risk IT Framework | ISACA's Risk IT Framework contains guidelines and practices for risk optimization, security, and business value. The latest version places greater emphasis on cybersecurity and aligns with the latest version of COBIT |
1.11 Understand and apply threat modeling concepts and methodologies
Threat modeling is used to systematically identify, enumerate, and prioritize threats related to an asset.
Three major threat modeling methodologies you need to know about for the exam are STRIDE, PASTA, and DREAD.
STRIDE
STRIDE is a threat-focused methodology that's less strategic and thorough than PASTA. It is an acronym of:
- Spoofing
- Tampering
- Repudiation
- Information disclosure
- Denial-of-service
- Elevation of privilege
PASTA
Process for Attack Simulation and Threat Analysis (PASTA), contrary to STRIDE, is an attacker-focused, risk-centric methodology. It is much more detailed than STRIDE and performs threat analysis from a strategic perspective.
The stages in PASTA are as follows:
- Define objectives
- Define technical scope
- Application decomposition
- Threat analysis
- Vulnerability and weakness analysis
- Attack modeling
- Risk and impact analysis
DREAD
DREAD is a threat model primarily used to measure and rank the severity of threats. DREAD is often used in combination with the STRIDE model, where STRIDE identifies the threats, and DREAD is then used to rank the severity of threats. The acronym means:
- Damage
- Reproducibility
- Exploitability
- Affected users
- Discoverability
Social engineering
Social engineering can be defined as using deception or intimidation to get people to provide sensitive information that they shouldn't in order to facilitate fraudulent activities.
It is a prevalent means of attack against organizations and employees (the biggest security weakness that exists in most companies) because it's very effective. Common social engineering tactics include intimidation, deception, and rapport.
Social engineering attacks can be mitigated through awareness, training, and education.
1.12 Apply supply chain risk management (SCRM) concepts
SLR, SLA, and service level reports
Security must be considered for all acquisitions and be part of the procurement process. Even if the acquisition is of a well-known brand, product, or service, risks exist and must be evaluated as part of the acquisition, or procurement, process. This evaluation should occur as early as possible and include security considerations that minimize the risk.
Service level requirements (SLR)
With the acquisition of a service, additional organizational requirements must be considered, which is done through an SLR document. Specifically, an SLR outlines:
- Detailed service descriptions
- Detailed service level targets
- Mutual responsibilities
Security requirements must be clearly communicated (e.g., SLAs) to suppliers/vendors/service providers.
Service Level Agreement (SLA)
After a service is acquired, an SLA must be put in place between the customer and the service provider.
SLAs often include expectations and stipulations related to:
- Service levels
- Governance
- Security
- Compliance with law and regulations
Service level reports
Service level reports are issued by a vendor or service provider to a client and provide insight and information about the service provider's ability to deliver services as defined by the SLA.
It might contain any of the following components:
- Achievement of metrics defined in the SLA
- Identification of issues
- Reporting channels
- Management
- Third-party SOC reports
1.13 Establish and maintain security awareness, education, and training programs
Everyone is responsible for security; however, they must know what to do. Awareness within an organization is fostered to create cultural sensitivity to a given topic or issue.
In addition, education helps people understand fundamental concepts and therefore develop decision-making skills and abilities.
Methods and techniques to provide awareness and training
Common methods to provide awareness and training are:
- Live in-person sessions
- Live online sessions
- Pre-recorded sessions
- Requirements/rewards
- Regular communications/campaigns
The topics selected should directly align with the organization's goals and objectives. At the same time, training and education programs and materials should also evolve and be updated accordingly to be most effective.
Program effectiveness evaluation
Program participants should be surveyed from time to time. Some key metrics to consider are:
- Total number of people completing the awareness program
- Number of people providing feedback in comparison to total attendees
- Number of people reporting suspicious activities after training completion
- Tracking of how well staff members performed
- Total number of attempts each person took the course
Destination Certification: The next step to pass the CISSP exam
The CISSP exam can seem daunting, but it all comes down to having the right information and an adequate learning process.
On Destination Certification, we offer an intelligent learning system backed by our expertise in the field that makes it much more straightforward. We continually assess your strengths and weaknesses to guide you to what you really need
to learn to pass the exam.
Enroll now in our CISSP MasterClass and start your journey towards becoming a cybersecurity professional.





