Our organizations need many layers of defense if we want to stand a chance against sophisticated attackers. Intrusion detection systems (IDSs) and intrusion prevention systems (IPSs) play a critical role.
IDSs solely detect, while IPSs can also prevent and correct
Each of these devices monitor traffic and then send alerts when they detect suspicious activity or policy violations. The key difference is that an IDS cannot directly prevent or correct attacks, while an IPS can. However, it is possible to set up an IDS in conjunction with other tools, such as a firewall, so that the firewall will filter out suspicious packets in an attempt to prevent attacks.
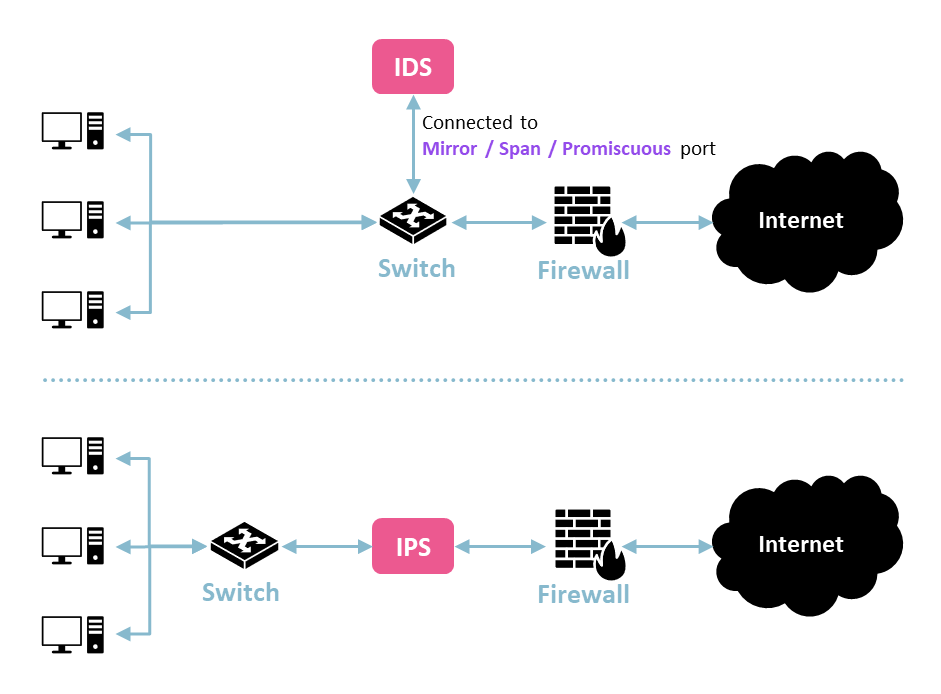
An IDS inspects mirrored packets, while an IPS is inline
One substantial difference between the two involves where they are placed. As you can see in the diagram, an IDS is generally connected to a SPAN port and analyzes mirrored copies of the network traffic passing through a switch. In contrast, an IPS is often placed inline, such as between a switch and the firewall. This placement is what allows it to prevent and correct malicious activity or rules violations. It can directly block traffic from passing through, while an IDS can’t because it is only inspecting copies of the network traffic.
Host-based IDS vs. network-based IDS
We can further break down IDSs into host-based intrusion detection systems (HIDSs) and network-based intrusion detection systems (NIDSs). A host-based intrusion detection system monitors the traffic for the host on which it is installed. We may have a bunch of hosts on our network where we want to specifically inspect the traffic going in and out. In contrast, a network-based intrusion detection system monitors traffic moving through a network segment.
Signature-based vs. anomaly-based detection
There are two major ways that IDSs and IPSs detect suspicious traffic. The first is through signatures, which involves inspecting packets for signatures of known malicious activity. When new threats are discovered, the IDS provider will add the signatures to the analysis engine so that we can detect them in the future. However, signature-based detection offers no protection against new attacks that haven’t had their signatures added.
Anomaly-based detection can complement signature-based detection by monitoring network traffic and creating a baseline for normal activity. Once this baseline has been created, anomaly-based detection involves picking up strange and suspicious deviations from the baseline. Statistical, state, traffic and protocol anomalies can then trigger alerts. Anomaly-based detection can be useful for picking up new threats that don’t already have their signatures in the analysis engine. However, it can generate a lot of false positives and it’s computationally expensive.

