SOC reports play a critical role in security auditing, but they can be a little confusing. The first stumbling block is the acronym. It used to stand for “Service Organization Controls”, but it has since been changed to “System and Organization Controls”.
The next stumbling block is that there are several variations. Not only are there SOC 1, SOC 2 and SOC 3 reports, but there are also subtypes known as type 1 and type 2 reports. Let’s jump in and explain them.
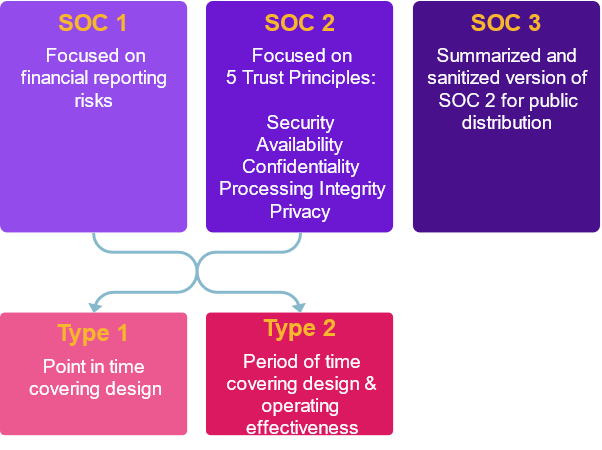
What are SOC 1 reports?
SOC 1 reports are focused on financial reporting, so security professionals don’t encounter them as often. These documents contain information about financial processes and controls, so they are only shared with a limited audience, such as current clients and auditors. They shouldn’t be shared with the wider public or prospective customers.
What are SOC 2 reports?
SOC 2 reports are audits concerned with five trust principles:
- Security
- Availability
- Confidentiality
- Processing Integrity
- Privacy
As security professionals, these are the documents that are most useful and interesting to us. A SOC 2 report must cover controls related to security, availability and confidentiality, but processing integrity and privacy are optional, so these may or may not be included in a given report.
SOC 2 reports are fairly detailed documents that contain a bunch of information about an organization’s systems, its controls and how they operate. This can include some sensitive information that we wouldn’t want to fall into the hands of adversaries. Because of this, SOC 2 reports are also only for limited audiences. To read a SOC 2 report, you generally have to be an existing customer and sign an NDA.
SOC 2 reports contain a lot of interesting information about an organization. If you’re a prospective customer looking for a service provider that meets your needs, you would love to get your hands on the provider’s SOC 2 report. It would give you a ton of great information about the organization’s security practices and help you decide whether the provider can meet your security, privacy and compliance needs. Unfortunately, it’s unlikely you’ll ever get your hands on one as a prospective client. But don’t worry, this is where SOC 3 reports come in.
What are SOC 3 reports?
SOC 3 reports are basically a stripped-down version of SOC 2 reports. They contain a lot of good information, but anything sensitive is generally removed. This means that SOC 3 reports can be shared much more widely, without risking harm to the organization. In many cases, SOC 3 reports essentially serve as a marketing tool for organizations. If a prospective customer wants information about a service provider’s privacy, security and compliance posture, the provider can hand them the SOC 3 report.
What’s the difference between type 1 and type 2 reports?
SOC 1 and SOC 2 reports can be further broken down into type 1 and type 2 reports. One of the main differences is that a type 1 report evaluates controls at a point in time, while a type 2 report evaluates controls over a period of time. This means that type 2 reports give you much more valuable information—you can find out a lot more if you look at controls over time instead of just a snapshot.

