Identity and Access Management comprises 13% of the CISSP exam. Domain 5 helps security professionals understand how they can control the way assets are accessed. Securing access control and management is needed to comply with the requirements of Confidentiality, Integrity, and Availability.
Having control over who has access to systems and information and the authorization mechanisms implemented in an organization is one of the most critical pillars of cybersecurity—for obvious reasons!
CISSP Domain 5: Identity and Access Management (IAM) addresses the following subdomains:
5.1. Control physical and logical access to assets
5.2. Manage identification and authentication of people, devices, and services
5.3. Federated identity with a third-party service
5.4. Implement and manage authorization mechanisms
5.5. Manage the identity and access provisioning lifecycle
5.6. Implement authentication systems
IAM helps organizations manage digital identities with the necessary technology to improve the end user experience, cost control, and risk mitigation. Let's have a look at the 5th domain's subdomains and key concepts you will need to know to pass the CISSP exam successfully.
5.1. Control physical and logical access to assets
Access control
What is access control?
Access control refers to the mechanisms that work together to protect organizational assets while simultaneously allowing controlled access to authorized subjects. Fundamental access control principles include: need to know, least privilege, and separation of duties. Access control is applicable at all levels of an organization and covers all types of assets.
Access control enables management to:
Specify which users can access the system
Specify what resources they can access
Specify what operations they can perform
Provide individual accountability—know who is doing what
Expect to be tested on: Understanding the fundamental access control principles and how they might be applied.
Access control principles
The fundamental access control principles are applied everywhere within access control:
Need to Know | Least Privilege | Separation of Duties |
|---|---|---|
Defending sensitive assets by restricting access to only required personnel who require access | Defending sensitive assets by granting only the minimum permissions required by the user or system | Defending sensitive assets by requiring more than one person to complete a task, to prevent errors and fraud. |
Access control applicability
Access control includes all aspects and levels of an organization and covers all types of assets, including:
- Facilities
- Systems/Devices
- Information
- Personnel
- Applications
Access control system
Access control focuses on controlling a subject's access to an object through some form of mediation, which is based upon a set of rules.
The above point to the use of the RMC, or Reference Monitor Concept, where some type of rules-based decision-making tool is placed between subjects and objects to mediate access. All activity is logged and monitored for the sake of accountability and assurance. And any implementation of the RMC is known as a security kernel.
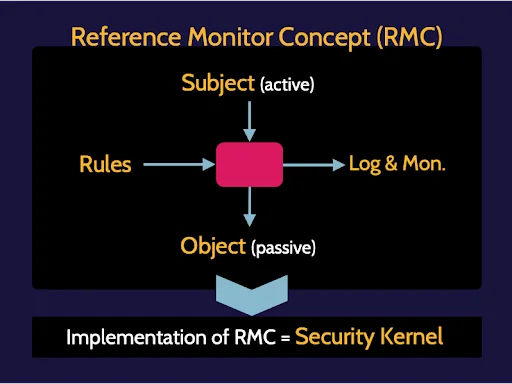
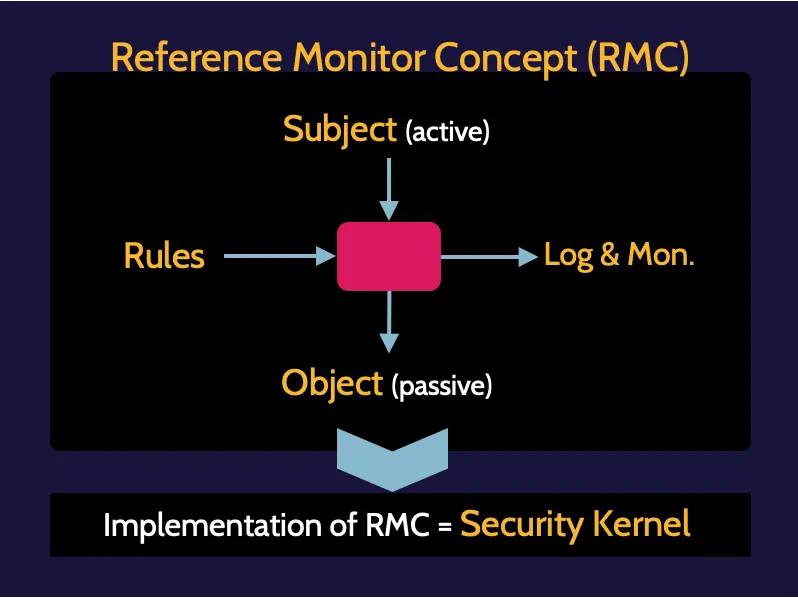
Logical access modes
Access control is more granular than simply allowing subjects to access objects.
Access control rules allow the access control mechanism to be much more granular.
Specific access rules allow precision concerning what subjects can access what objects and exactly what those subjects can do with those objects.
Access should be based on the use of concepts like need to know and least privilege.
Administration approaches
Access control administration often takes one of two approaches: centralized or decentralized. Many organizations also utilize a hybrid approach. Both offer pros and cons.
Expect to be tested on: Understanding access control administration approaches and the pros and cons of each approach.
Centralized | Hybrid | Decentralized |
|---|---|---|
|
|
|
|
|
|
| Cell |
|
Cell | Cell |
|
5.2. Manage identification and authentication of people, devices, and services
Access control services
- Access control services consist of identification, authentication, authorization, and accountability.Identification refers to the assertion of a user's identity or a process to a system.
- Authentication refers to the verification of identity through knowledge, ownership, or characteristic.
- Authorization refers to the level of access defined for the identified and authenticated user or process.
- Accountability refers to proper identification, authentication, and authorization that is logged and monitored. It's also known as the principle of access control.
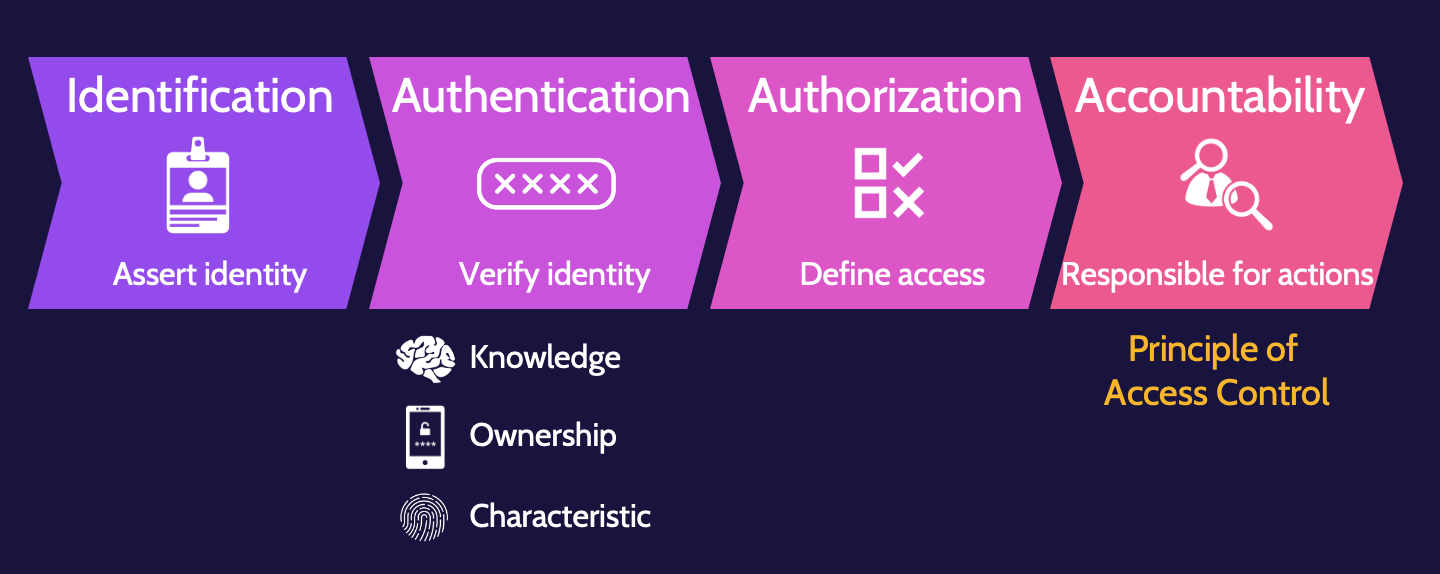
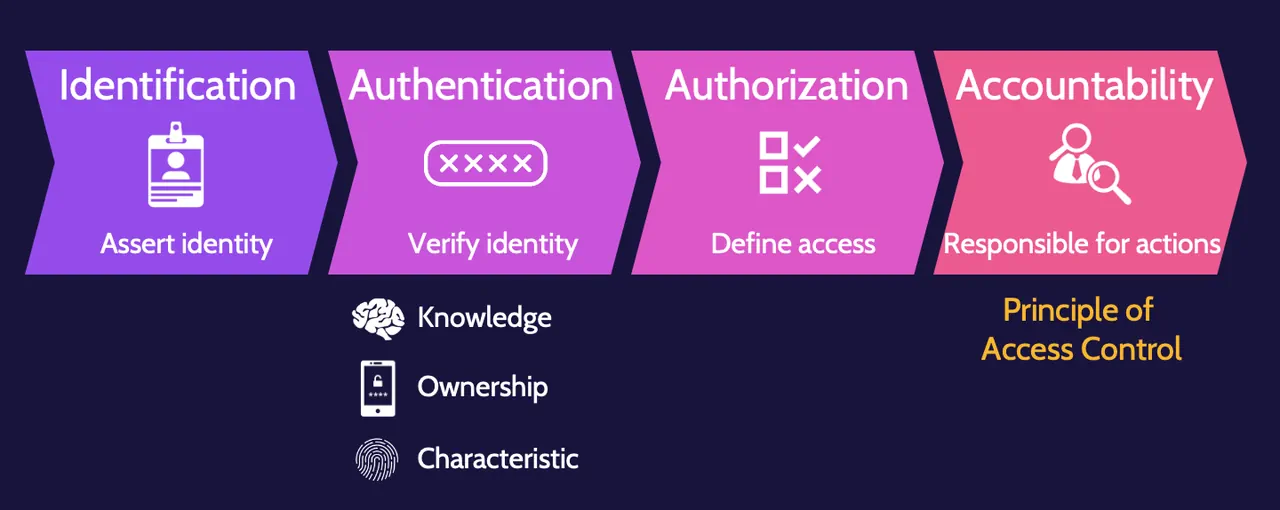
Identification
Identification is the component of access control services that uniquely asserts a user's identity or a process to a system. Identification guidelines include unique identifiers, nondescriptive of job/role and secure issuance.
Expect to be tested on: Identification as the first component of access control services, identification methods, and guidelines.
Authentication
There are three factors that can be used to verify a user's identity regarding authentication.
Authentication by knowledge | Authentication by ownership | Authentication by characteristic |
|---|---|---|
Something you know | Something you have | How you behave or your physiology; something you are |
Authentication by knowledge
Authentication by knowledge is the component of access control services that refers to verifying identity through something known, like a password, passphrase, or questions.
It is also known as something you know; it simply means that a person uses a password, a passphrase, or a response to one or more security questions to authenticate to a system.
Ideally, whether a password, passphrase, or questions are used, each should be unique to the user and not easily guessed or otherwise determined.
Expect to be tested on:
- Authentication by knowledge as one type of authentication.
- Different forms of authentication by knowledge.
Authentication by ownership
Authentication by ownership is the component of Access Control Services that refers to the verification of identity through something a user possesses. These are some of the key concepts:
- One-Time Passwords (OTP) are generated via synchronous or asynchronous processes.
- Soft tokens refer to software-based applications, like Google Authenticator, that generate one-time passwords.
- Hard tokens refer to small physical tokens, like RSA's SecureID device, that generate one-time passwords.
- Smart cards are typically credit-card-size plastic cards with an embedded semiconductor chip that stores, accepts, and sends information; they work in collaboration with a smart card reader.
- Memory cards are typically credit-card-size plastic cards with a narrow magnetic strip on the back of that card that contains information related to the card owner, issuing bank, account number, PIN, etc.
Expect to be tested on:
- Authentication by ownership as another type of authentication.
- Understanding the difference between asynchronous and synchronous password generation
- Understanding the differences between smart and memory cards
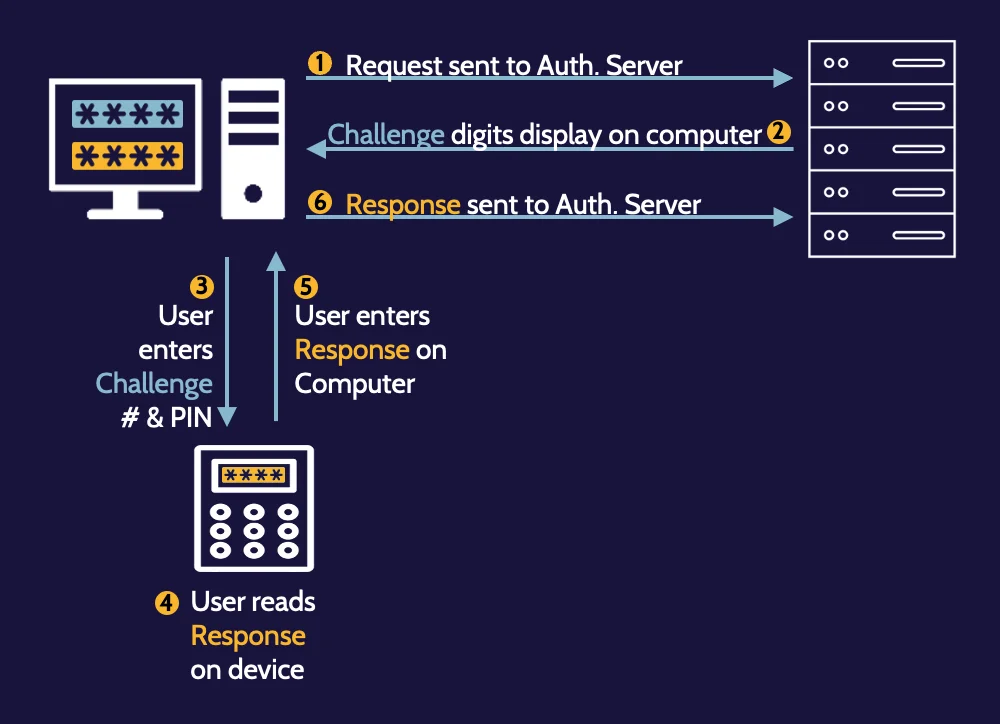
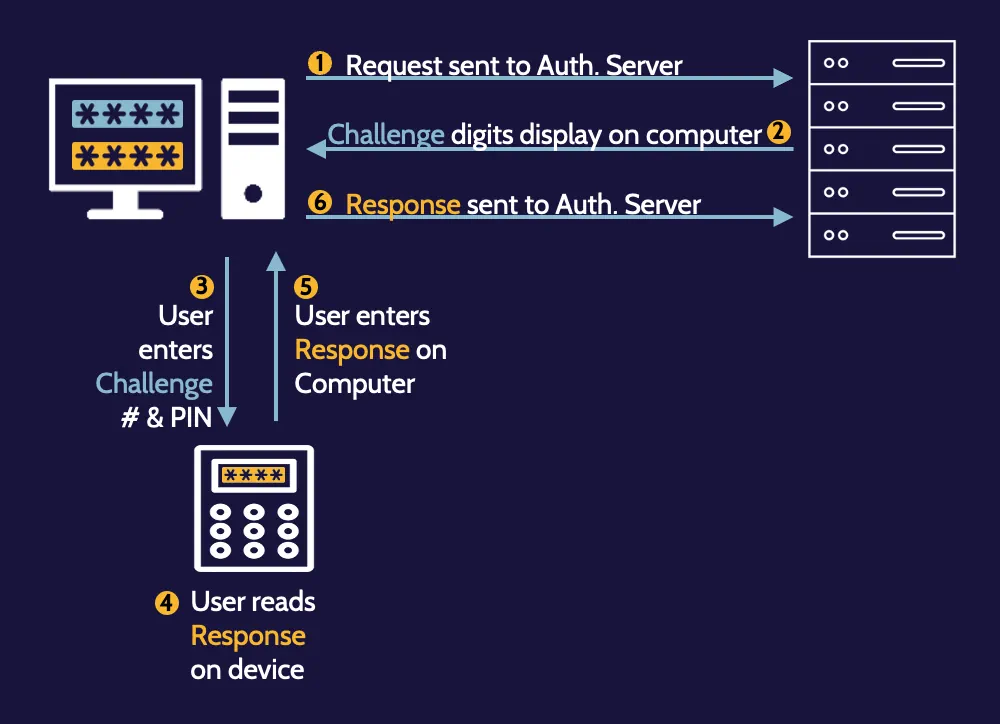
One-time passwords:
Asynchronous
(less commonly used)
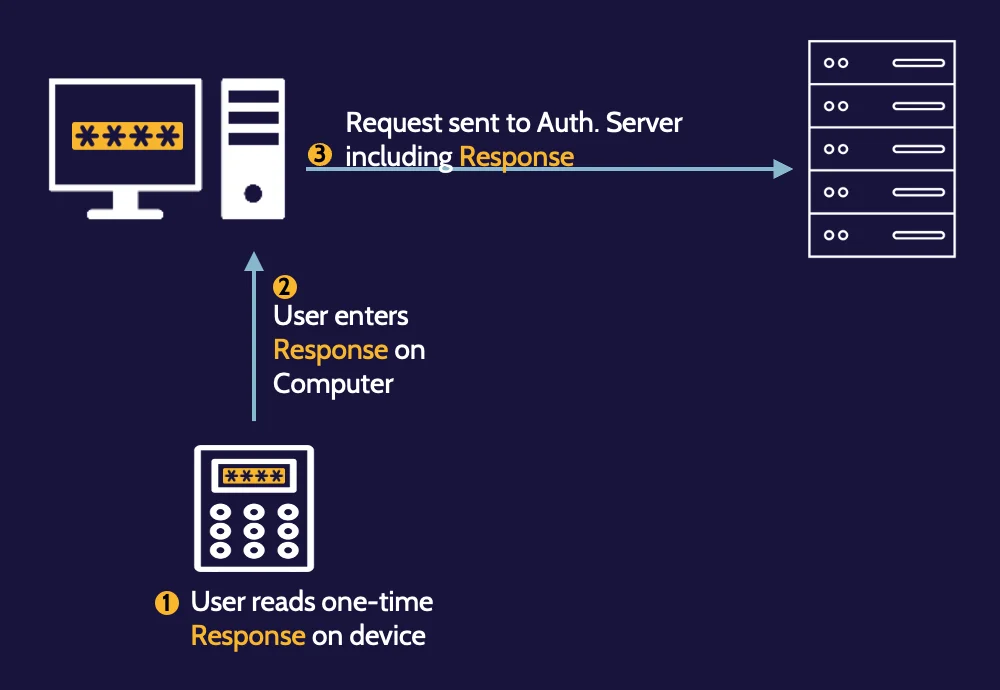
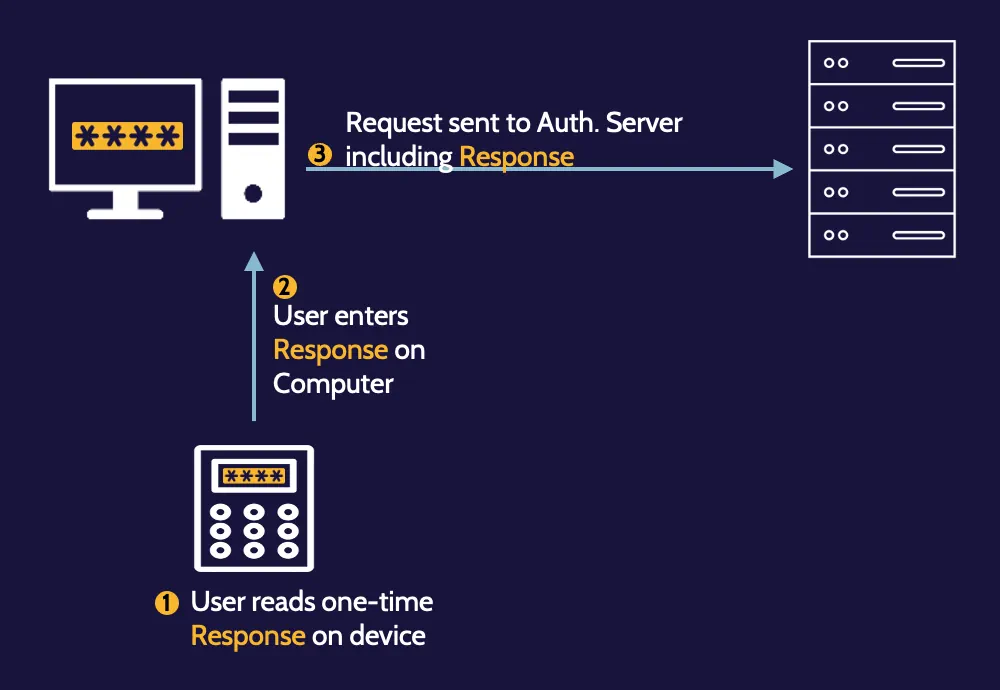
One-time passwords:
Synchronous
(more commonly used)
Authentication by characteristics
Authentication by characteristics refers to physiological and behavioral biometric types. The accuracy of biometric devices can vary and is not always 100 percent accurate. Their use must consider processing speed, user acceptance, protection of biometric data, and accuracy.
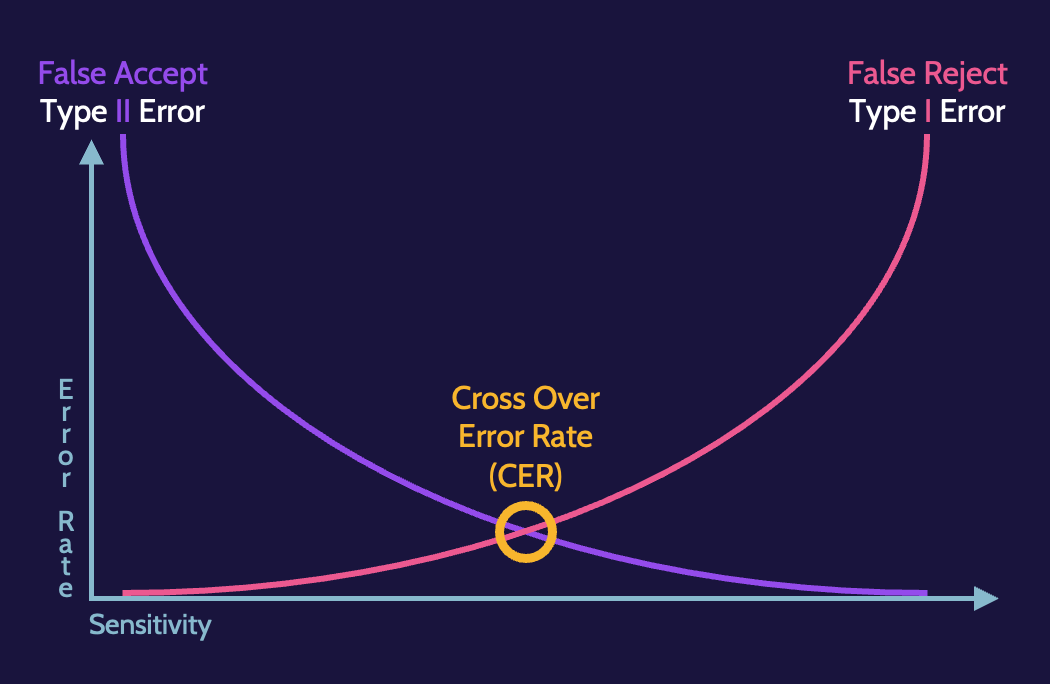
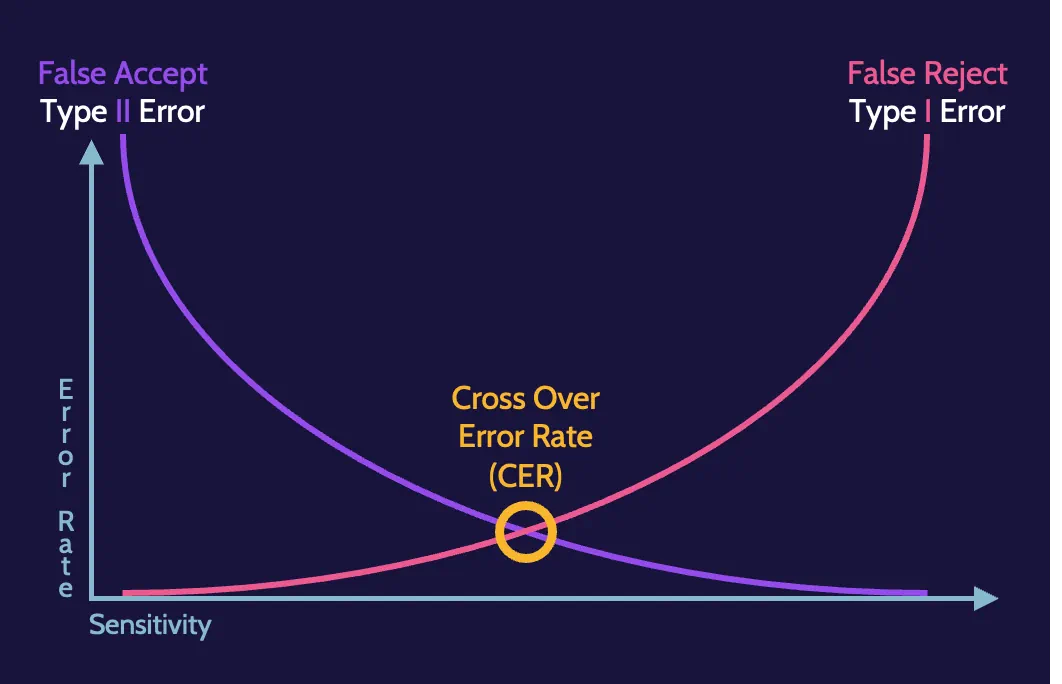
In addition, Crossover Error Rate (CER) represents the intersection between Type 1 (false reject) and Type 2 (false acceptance) errors, and it measures the accuracy of a biometric system.
Expect to be tested on:
- Biometric error types and which is worse
- Crossover error rate and what it represents
- Biometric device types and least/most accurate
Physiological and behavioral authentication types
Physiological characteristics | Behavioral characteristics |
|---|---|
Fingerprints | The way a person writes |
Hand geometry | The way a person walks—their gait |
Facial features | The way a person speaks—their voice |
Eyes (retina and iris) | The way a person types—keyboard dynamics |
Biometric device considerations
Due to the nature of how biometric authentication works, factors like the ones noted below must be considered:
- Processing speed
- User acceptance
- Protection of biometric data
- Accuracy
Biometric device accuracy/types of errors
They're not always 100% accurate. The same cannot be said of a system that uses physiological or behavioral attributes for authentication. When considering biometric systems and their accuracy, two primary types of errors need to be understood:
Type 1—False Rejection | Type 2—False Acceptance |
|---|---|
A valid user is falsely rejected by the system | An invalid user is given access to a system |
Cell | Much more serious and potentially dangerous situation |
Type 2 errors are much more dangerous than Type 1 errors.
Crossover Error Rate (CER)
When Type 1 (false reject errors) are low, Type 2 (false accept errors are high) and vice versa. The intersection of the two error plots is what's known as the Crossover Error Rate (CER).
The crossover error rate is a useful metric for biometric systems because it's a way to measure the system's overall accuracy. A number closer to zero means the system is more accurate.
Biometric templates
If someone's password is exposed, they can just change their password and memorize the new password. However, if their biometric data is exposed, they can't just grow a new finger or eyeball.
Accordingly, raw or original biometric data should never be stored, such as a simple picture of a fingerprint. Instead, good biometric systems will use one-way mathematical functions to create a representation of the features or characteristics of the source data. This digital representation is called a template.
Factors of authentication
- Factors of authentication refer to the three types of authentication: authentication by knowledge, authentication by ownership, and authentication by characteristic.
- Single-factor authentication refers to any of the three types of authentication used.
- Multifactor Authentication (MFA) refers to two (or more) of the three types of authentication being used.
Expect to be tested on: Understanding the difference between single-factor authentication and multifactor authentication and what constitutes each type.
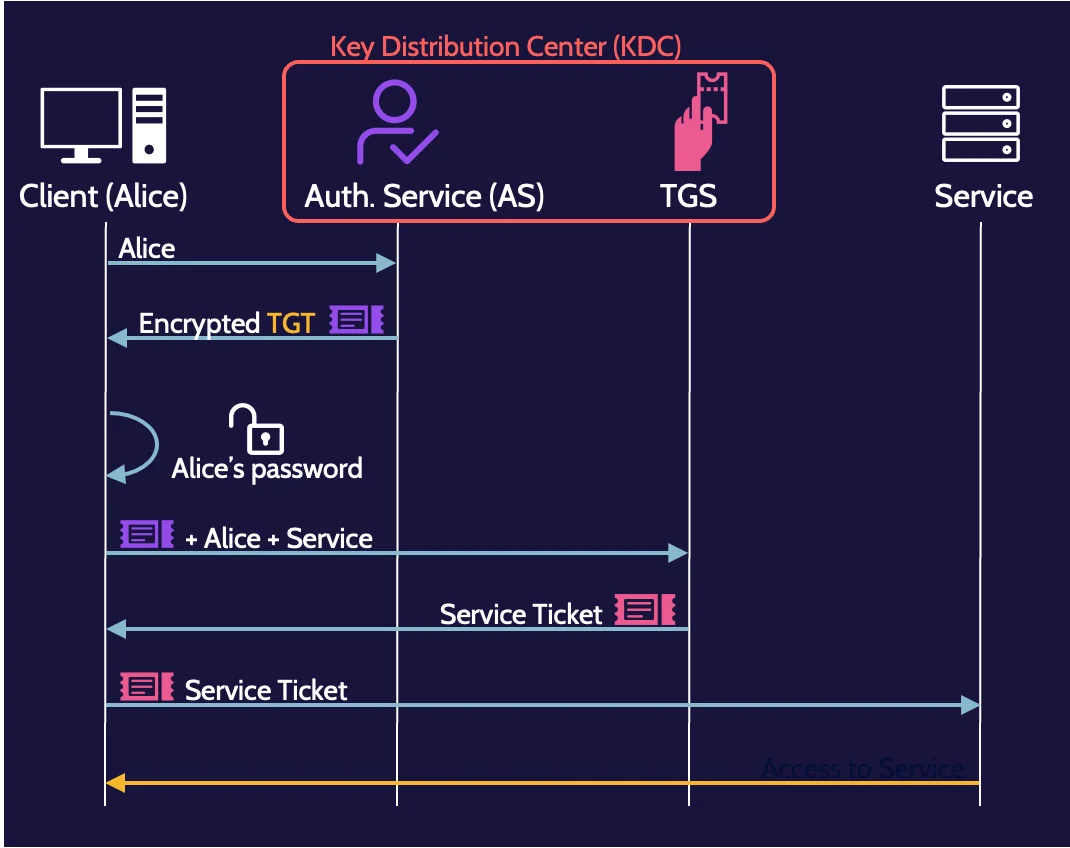
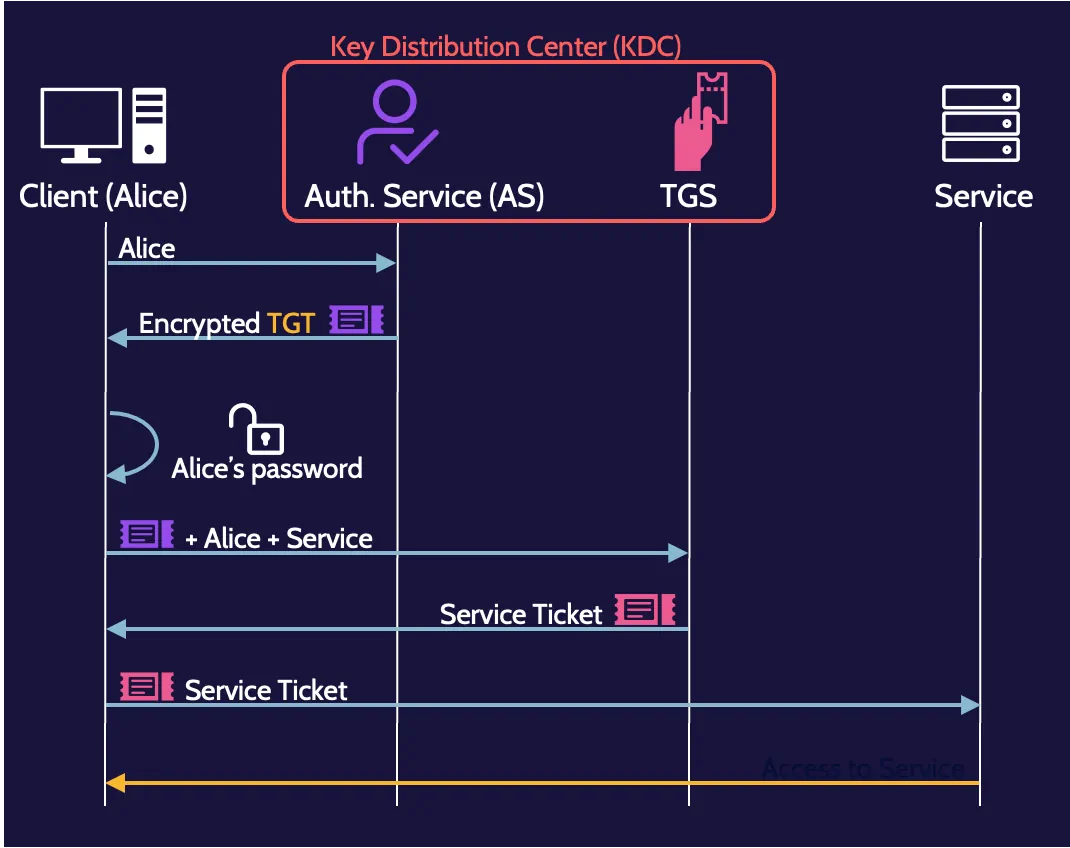
Kerberos
One of the major SSO authentication protocols is known as Kerberos. Drawing from the myth, Kerberos protects access to resources and provides three primary functionalities:
Accounting
Authentication
Auditing
Kerberos is an old and complicated protocol; thankfully, you do not need to be an expert on how the protocol works for the exam. This is a simplified description of the major steps in the Kerberos authentication process:

SESAME
Secure European System for Applications in a Multi-Vendor Environment, better known as SESAME, is an improved version of Kerberos. Like Kerberos, SESAME is a protocol for enabling single sign-on.
Also, one of the big advantages of SESAME over Kerberos is that it supports symmetric and asymmetric cryptography, so it naturally solves the problem of key distribution.
Even though SESAME is a better protocol, Kerberos is far more prevalent because it's built into many prevalent systems, including the Windows operating systems, macOS, and various Linux and Unix distros.
CAPTCHA
CAPTCHA is a security measure that works by asking a user—typically a visitor to a website or portal—to complete a simple test to prove they're human and not a robot or automated program. It is used to prevent automated account creation, spam, and brute-force password decryption attacks.
Expect to be tested on: Understand what CAPTCHA is and why it is most often used.
Session management
Session management refers to the management of sessions created through successful user identification, authentication, and authorization process. A session represents the connection and interaction between a user and a system.
Session hijacking is a risk where no session management exists, and session termination and re-authentication is the best way to prevent or mitigate session hijacking.
Expect to be tested on:
What is session hijacking?
How can session hijacking be prevented?
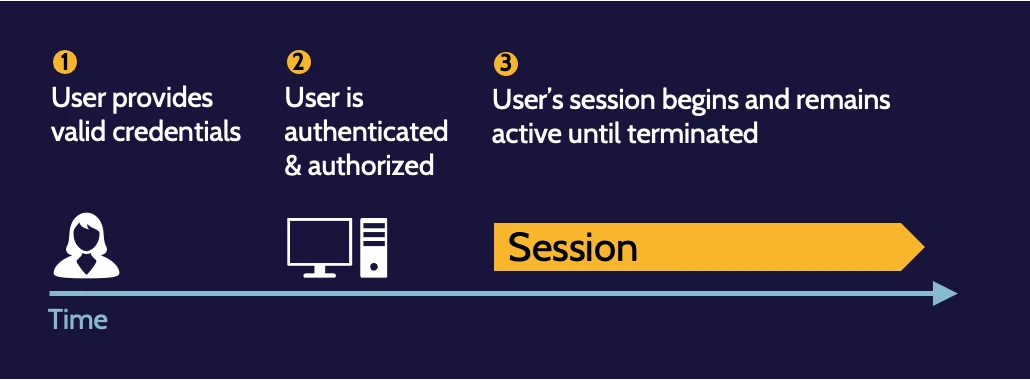
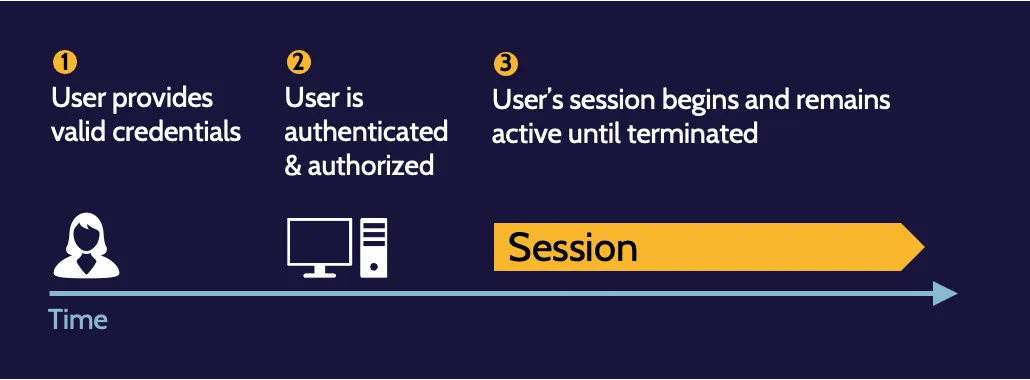
Session hijacking
Through simple carelessness or sophisticated technical means, somebody other than a legitimate user could gain access to a session and use it for malicious purposes.
How do you prevent session hijacking?
The preventive measure for session hijacking is session termination, which is an important component of session management. There are several major ways exist to terminate a session. The primary and best way to prevent session hijacking is through frequent re-authentication.
Additionally, a user is continually re-authenticated by the system in a manner that is transparent to the user. That makes it much more difficult for an attacker to compromise a user's active session.
Registration and proofing of identity
Identity proofing—registration—is the process of confirming or establishing that somebody is who they claim to be. It is a component of provisioning in the identity life cycle.
Authenticator Assurance Levels (AAL)
Authenticator Assurance Levels (AAL) refer to the strength of authentication processes and systems.
AAL levels rank from AAL1 (least robust) to AAL3 (most robust).
AAL1 |
|
AAL2 |
|
AAL3 |
|
Federated Identity Management (FIM)
Single sign-on refers to one-time authentication to gain access to multiple systems in one organization; federated identity management (FIM) refers to one-time authentication to gain access to multiple systems, including systems associated with other organizations. It relies on trust relationships established between different entities, including principal/user, identity provider, and relying party:
- Principal/user. The person who wants to access a system.
- Identity provider. The entity that owns the identity and performs the authentication.
- The relying party is also known as the service provider.
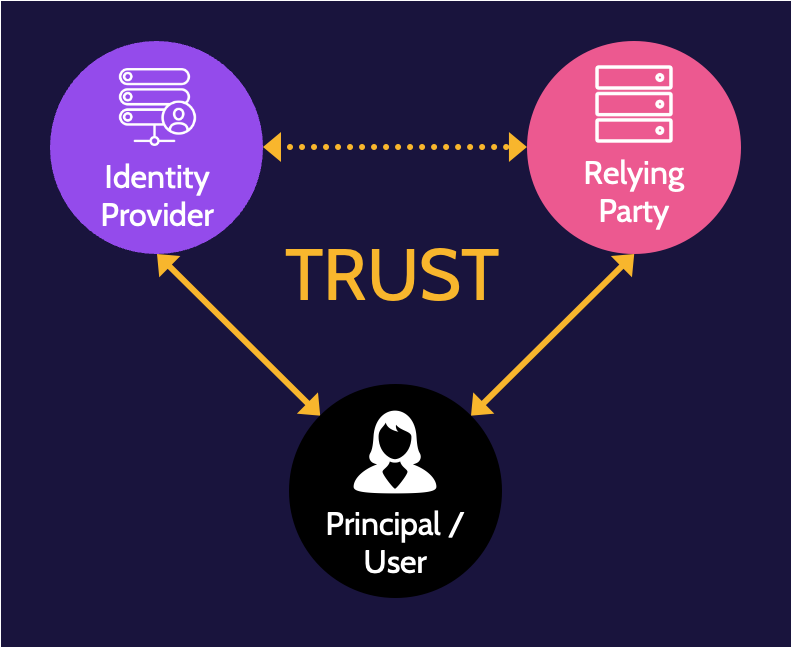
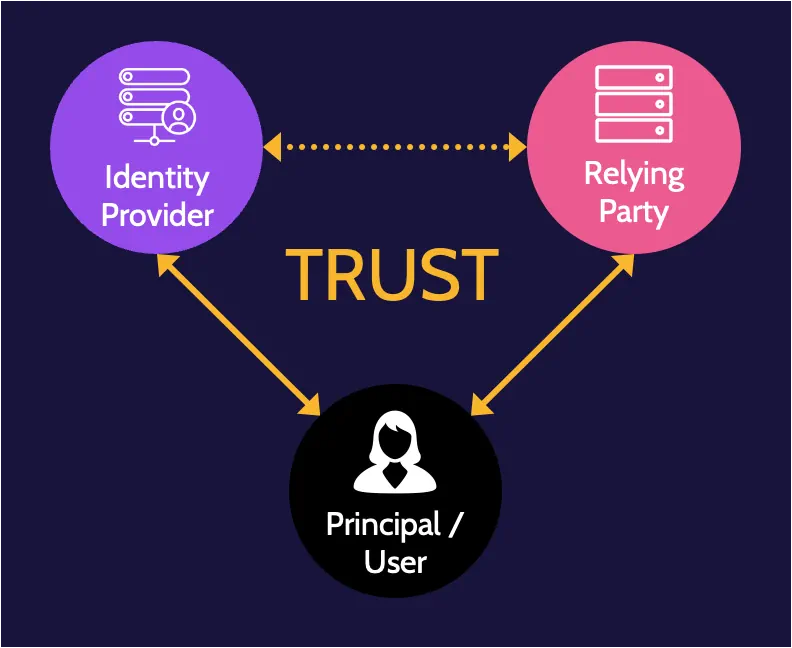
Federated access standards
Key Federated Access protocols include Security Assertion Markup Language (SAML), WS-Federation, OpenID (for authentication), and OAuth (for authorization):
SAML is frequently used in Federated Identity Management (FIM) solutions and provides authentication and authorization. SAML assertions are written in XML or Extensible Markup Language. XML is a way of communicating in a manner that is machine and human-readable.
OpenID and OAuth are open-standard federated access protocols that provide authentication via OpenID and authorization via OAuth.
Several major protocols enable federated access, with Security Assertion Markup Language (SAML) being one of the most important to understand. WS-Federation, OpenID, and OAuth are the others that should be known at a high level.
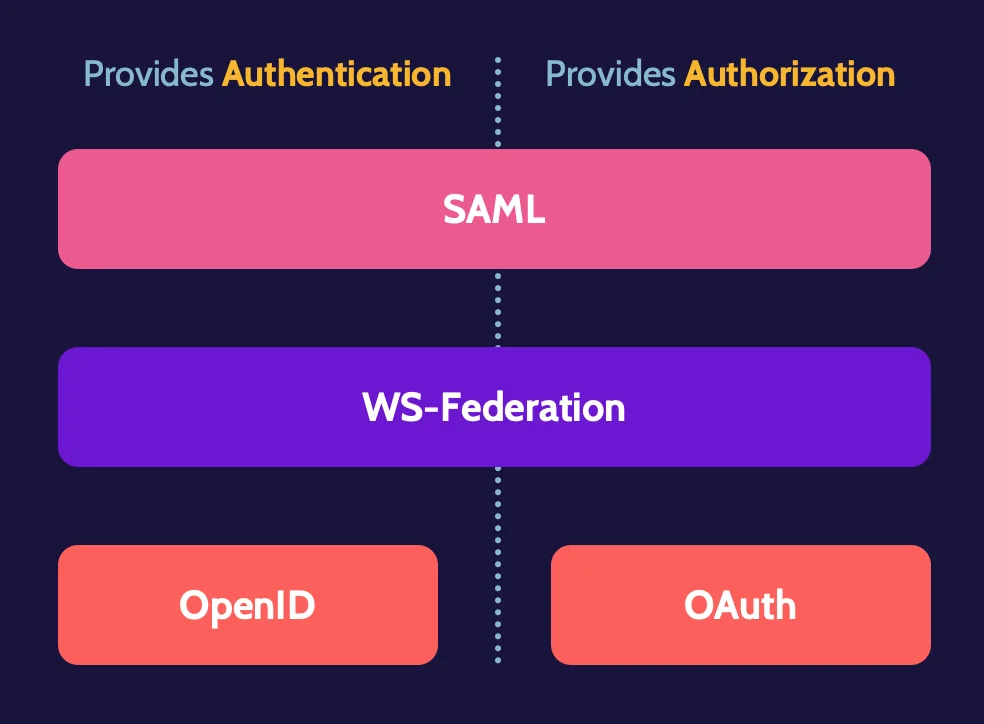
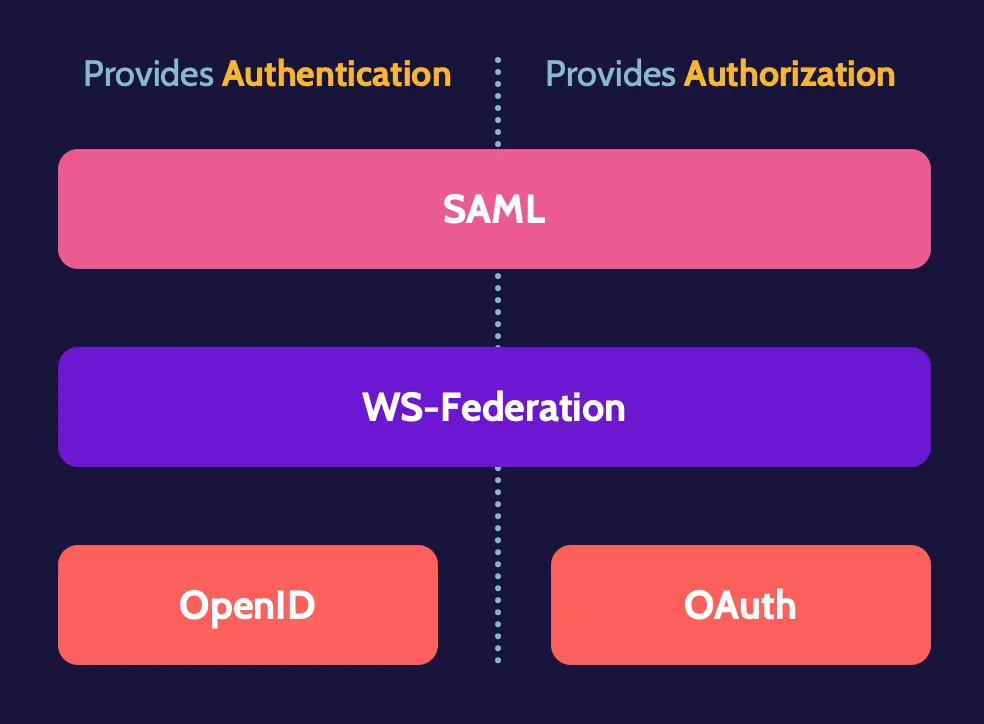
Security Assertion Markup Language (SAML)
SAML provides two capabilities: authentication and authorization.
First, the user (principal) must authenticate via the identity provider.
The identity provider will authenticate the user through the process of identification and authentication, at which point the user will be issued a SAML assertion ticket.
Once the SAML assertion ticket is provided to the user, the user will pass it on to the service provider.
These are SAML's key components:
Component | Function |
|---|---|
Assertion | Authentication, authorization, and other attributes |
Protocol | Defines how entities request and respond to requests |
Bindings | Mapping of SAML onto standard communication protocols (ex: HTTP) |
Profiles | Define how SAML can be used for different business use cases (ex: Web SSO, LDAP, etc.) |
Accountability = principle of access control
To achieve accountability, several things need to happen:
- Users must be uniquely identified
- Users must be properly authenticated
- Users must be properly authorized
- All actions should be logged and monitored
Just-in-time (JIT) Access
Just-in-time access refers to the elevation of user privileges to an authorized user for a short period, so a user may complete necessary but infrequent tasks.
It mitigates the need for long-term elevation of privileges, which minimizes potential security risks. The way it is set up and administered oftentimes allows for access to be granted in an automated fashion versus a manual process.
5.3 Federated identity with a third-party service
Identity as a Service (IDaaS)
Identity as a Service (IDaaS) refers to the implementation or integration of identity services in a cloud-based environment.
IDaaS has a variety of capabilities, which are:
- Provisioning
- Administration
- Single Sign-on (SSO)
- Multifactor authentication (MFA)
- Directory Services
- On-premise and in the Cloud
It supports multiple types of identities/accounts: cloud identity, synced identity, linked identities, and federated identity.
Header | Account Stored | Authentication by |
|---|---|---|
Cloud Identity | Created and managed in the cloud | Cloud service |
Synced Identity | Created and managed in a local store (e.g., active directory) and synced/copied to the cloud or vice versa | Either local or cloud |
Linked Identities | Two separate accounts which are linked. For example: one account in a local store and a second account in the cloud service | Either local or cloud |
Federated Identity | Identity Provider | Identity Provider |
Identity and Access Management Solutions
Identity and Access Management (IAM) solutions can use any of these three models: on-premise, cloud, and hybrid.
On-premise |
|
Cloud |
|
Hybrid |
|
IDaaS risks
The following are potential risks relating to IDaaS:
- Availability of the service. If the cloud service provider suffers an outage or the service is otherwise unavailable, the users will be unable to access systems.
- Protection of critical identity data. PII and other sensitive data will be under the control of the cloud service provider. That means adequate protection of data is based on protection mechanisms the provider has available.
- Entrusting a third party with sensitive or proprietary data. Based on the identity data shared with the cloud service provider, other information about the organization might also be gained. Protections need to be in place to protect against this information from being leaked or shared with any unauthorized parties.
5.4 Implement and manage authorization mechanisms
Within the realm of authorization, a number of different philosophies and methodologies exist, and these can be broadly categorized as discretionary, mandatory, and non-discretionary. Their main characteristics are illustrated in the following table:
Discretionary Access Control (DAC) |
|
Role-Based Access Control (RBAC) |
|
Rule-Based Access Control |
|
Attribute-Based Access Control |
|
Mandatory Access Control (MAC) |
|
Risk-Based Access Control |
|
Discretionary Access Control (DAC)
Discretionary Access Control (DAC) means an asset owner determines who can access the asset; access is given at the discretion of the owner. In other words, it means somebody determines who can access an asset. That somebody is the owner.
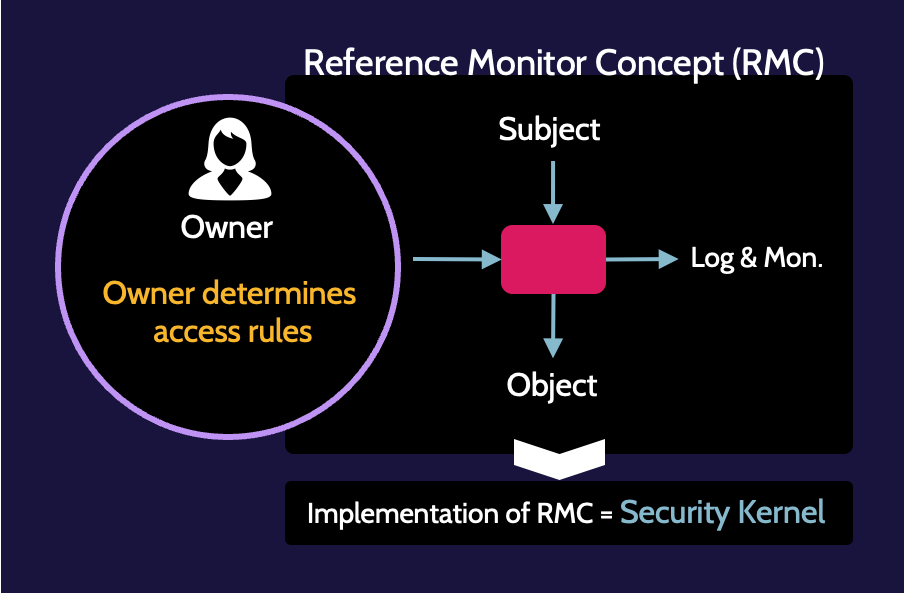

Three primary types of DAC exist: rule-based access control, role-based access control, and attribute-based access control.
Within the realm of discretionary access control, three primary types of DAC exist:
- Rule-Based Access Control: Access to an object by a given subject is based upon one or more rules determined by the owner.
- Role-Based Access Control (RBAC): Access to an object by a given subject is based upon the role or job function and related authorizations needed to perform duties.
- Attribute-Based Access Control: Access to an object by a subject is much more granularly controlled and based upon attributes, such as job function, type of device being used to access the object, time of day, classification of the asset, and so on.
Mandatory Access Control (MAC)
Mandatory Access Control is very rare to see in use and only typically used in government organizations, where confidentiality is often of primary importance, requiring every asset in an organization to have a classification and every user to be assigned a clearance level. It determines access based upon the clearance level of the subject and classification, or sensitivity, of the object.
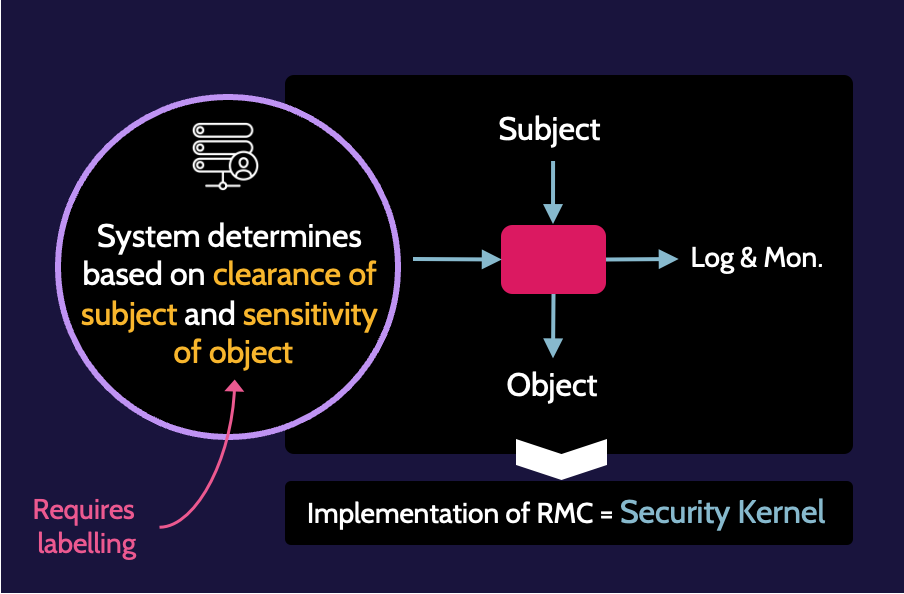
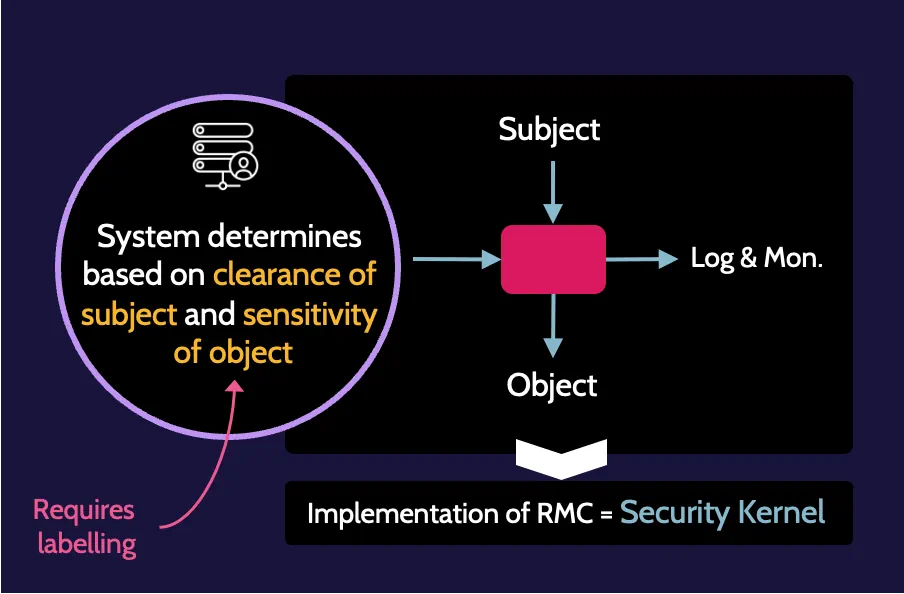
The system itself makes access control decisions based upon the classification of the objects being accessed and the clearance of the subject requesting access. In a MAC environment, every single object should be classified with a specific classification label, e.g., public, secret, top secret, and so on. Correspondingly, all users should have a security clearance that aligns with the classification system used for objects. Within this framework, access will then be granted or denied accordingly.
Non-discretionary access control
Non-discretionary Access Control means that somebody other than the asset owner determines who gets access. It should be avoided, if possible. Although this isn't a security best practice, it's an existing working practice in many companies and leads to someone in the IT department.
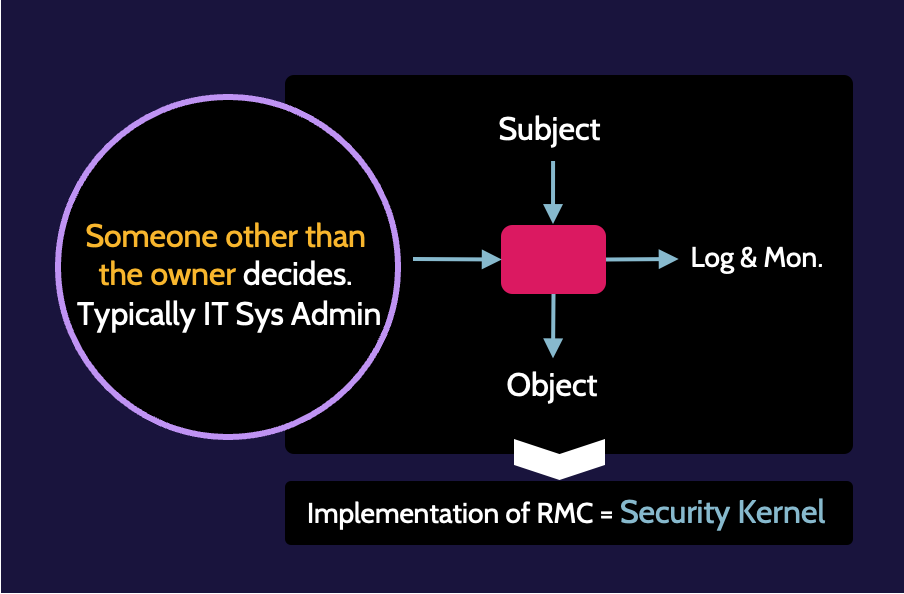
Additionally, situations may exist where the owner (accountable) delegates responsibility of access control to areas like IT, but then the owner doesn't offer input with regard to who should be given access.
5.5 Manage the identity and access provisioning life cycle
Vendor access
Vendor identity and access provisioning for systems and data should be considered with the same or more care than employee identity and access provisioning. It might also include a security review component that includes a deeper review of the vendor or inspection of a vendor's facilities, systems, and other relationships.
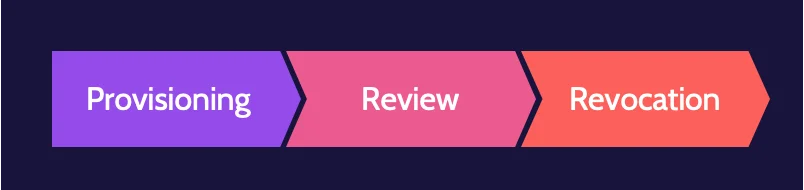
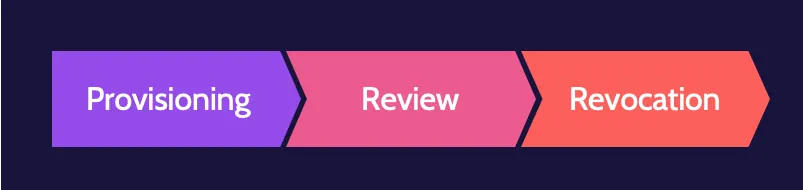
Identity life cycle
The identity life cycle comprises three parts: provisioning, review, and revocation.
- Provisioning: upon hire of a new employee and when an employee changes roles. Provisioning activities include background checks, confirming skills, and identity proofing, among other things.
- Review (also known as user access review): should take place as often as necessary and more frequently for higher privilege accounts. Assets and systems to which a user has access should be reviewed by the asset or system owner to determine if ongoing access is necessary or if access should be modified.
- Revocation: upon voluntary or involuntary termination. It typically takes place when an employee leaves the organization, through voluntary or involuntary separation, but it can also take place when an employee changes role.
User access review
Account access review is an ongoing process, regardless of the type of account (user, system, service), and its frequency should be based upon the value of resources and associated risks. However, privileged accounts should be reviewed more frequently.
How often should access reviews be performed?
In the case of a user changing roles, their access should be reviewed at the time of the change. New access should be granted as needed, and any access that is not needed should be removed. Of course, access should always be reviewed and approved by the owner. When someone leaves the company (through voluntary or involuntary termination), that user's access should be reviewed, and in most cases, all access should be removed.
Privilege escalation
In addition to more frequent reviews of privileged accounts, a recommended security practice is for system administrators (users with admin, root, and similar privileges) to only use their privileged accounts when strictly necessary.
Privileged users should utilize two accounts. They should use a standard user account for regular business purposes, such as checking email, participating in meetings, and so on, and they should use a separate account with elevated privileges only when performing administrative tasks that require a higher level of access.
5.6. Implement authentication systems
Authentication systems
Authentication systems are used to prove or verify an identity or system assertion. Popular authentication systems include:
- OpenID Connect (OIDC)/Open Authorization (OAuth)
- Security Assertion Markup Language (SAML)
- Kerberos
- Remote Authentication Dial-In User Service (RADIUS) and Terminal Access Controller Access Control System Plus (TACACS+)
OAuth is an access delegation standard that target applications can use to provide client applications with secure delegated access over HTTPS. It authorizes devices, APIs, servers, and applications with access tokens rather than credentials.
On the other hand, OpenID Connect (OIDC) is an identity layer built on top of the OAuth 2.0 framework. It allows third-party applications to verify the identity of the end user and obtain basic user profile information. While OAuth 2.0 is about resource access and sharing, OIDC is about user authentication.





