Domain 2 - Asset Classification MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to Asset Classification in Domain 2, to understand how they interrelate, and to guide your studies.
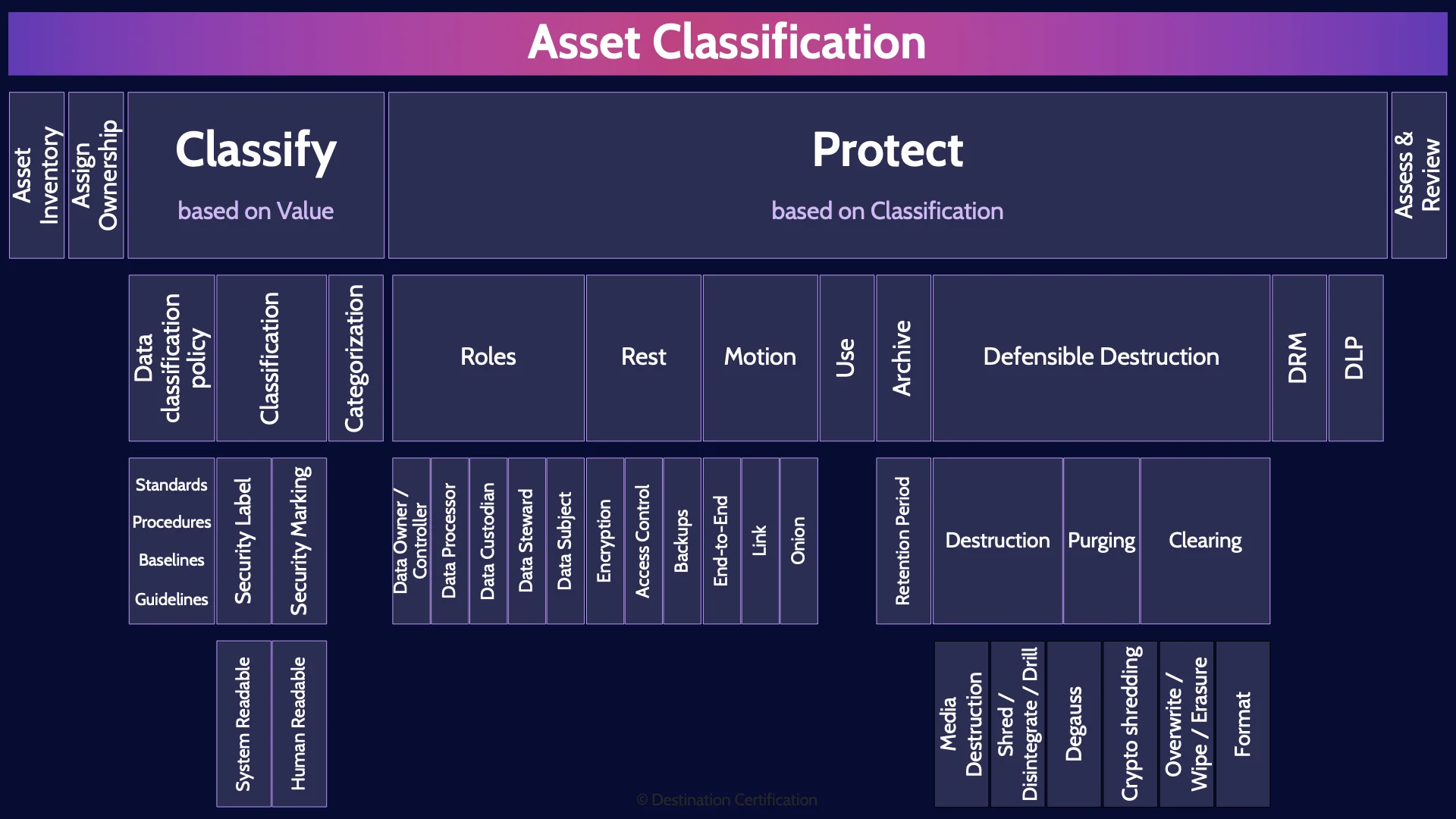
This is the only video for domain 2. I have included links to the other MindMap videos for the other domains in the description below. These MindMaps are one part of our complete CISSP MasterClass.
Asset Classification
Asset classification is fundamentally about ensuring that assets receive the appropriate level of protection.
What is an asset? Anything of value to the organization: people, buildings, equipment, software, data, and intellectual property are all assets, among many others.
In security, we often just speak of data classification. We should be talking about asset classification which encompasses data classification and clearly implies that we should be classifying all the assets of the organization and protecting them appropriately.
Asset Inventory
The first step in the asset classification process is creating and maintaining an asset inventory – a catalog, a listing, of all the assets from across the organization
Assign Ownership
For every single asset there should be a clearly defined owner. It is critical to determine who the asset owner is as the owner is accountable for the protection of an asset. The owner is best positioned to determine how valuable an asset is to the organization, and thus what classification the asset should be assigned.
Classify - based on Value
As I already mentioned, and want to emphasize here, the reason we classify assets is so that we can identify how valuable they are to the organization and therefore the appropriate level of protection required.
Data classification policy
Before we can begin classifying anything, we first need to define the classification levels, the classes, and clearly identify who is accountable and responsible for what. All of this should be documented in a data classification policy.
Standards Procedures Baselines Guidelines
Standards, procedures, baselines and guidelines should then be created based on the policy. Procedures will define step-by-step instructions for classifying data based on the classes defined in the policy. Baselines will define minimum security requirements for each class. Remember that point.
Classification
Classification is a system of classes, ordered according to value. For example, public, proprietary and confidential could be the 3 classes that an organization defines with public being the least valuable, and confidential being the most. Different organizations will choose different classes based on whatever best suits their needs. So don’t memorize any particular classification scheme as they vary significantly from organization to organization.
Security Label
Security Labels are the means used to associate a set of security attributes with a specific information object as part of the data structure for that object. In other words, labels are meant to be read by the system to understand the classification of data and therefore the protection required.
System Readable
So remember labels are meant to be read by the system and enable system-based enforcement.
Security Marking
Security marking is very similar. The means used to associate a set of security attributes with objects in a human-readable form. In other words, labels are meant to be read by people to understand the classification of data and therefore the protection required.
Human Readable
So remember markings are meant to be read by humans to enable organizational process-based enforcement of information security policies.
Categorization
And the final major piece here is Categorization which is the act of sorting assets into the defined classes. Categorization is a process of putting assets into different classes.
Protect - based on Classification
How do we go about protecting assets based on their classification.
Roles
We can begin by having clearly defined roles of who is accountable or responsible for what?
Data Owner / Controller
The data owner, also known as the data controller, is the most important role, as the owner is accountable for the protection of the data. The owner will define the classification for data and the owner is then accountable for ensuring the data is protected accordingly.
Data Processor
Data processors, as the name implies, are responsible for processing data on behalf of the owners. A typical example of a data processor is a cloud service provider – they are storing and processing data on behalf of the owner.
Data Custodian
Data Custodians have technical responsibility for the data. Meaning custodians are responsible for ensuring data security, availability, capacity, that backups are performed and that data can be restored. They are responsible for the technical aspects of data.
Data Steward
Data Stewards, on the other hand, have a business responsibility for the data. Meaning stewards are responsible for ensuring data governance, data quality, compliance. Essentially Stewards are employees from the business who are responsible for ensuring the data is useful for business purposes.
Data Subject
And the data subject is the individual to whom any personal data relates. It is data about them.
Rest
We can also think about how we would protect data based on whether it’s at rest on a storage device somewhere, or in motion across a network, being used, archived, or even defensibly destroyed. We’ll start with techniques for protecting data at rest.
Encryption
One of the major techniques we can use is encryption. We use one of the many excellent encryption algorithms which I’ll discuss in domain three to encipher the data and turn it into ciphertext. The ciphertext is then well protected unless an attacker can get their hands on the correct encryption key to decipher the data or they discover a flaw in the encryption.
Access Control
We can further have strong access controls in place, which I will discuss in domain 5, to ensure that only properly authenticated and authorized individuals have access to the data. We can implement controls like multi-factor authentication and have good logging and monitoring in place to make users accountable for what they do with the data.
Backups
To ensure data is not accidentally lost or destroyed, we can have all sorts of different data backup and data resiliency controls, which I will discuss in domain 7.
Motion
The next major grouping of controls we can look at for protecting data, are for data in motion – data that is in transit across a network. All of these data in motion controls involve encrypting the data in some fashion while it is in transit across potentially insecure networks.
End-to-End
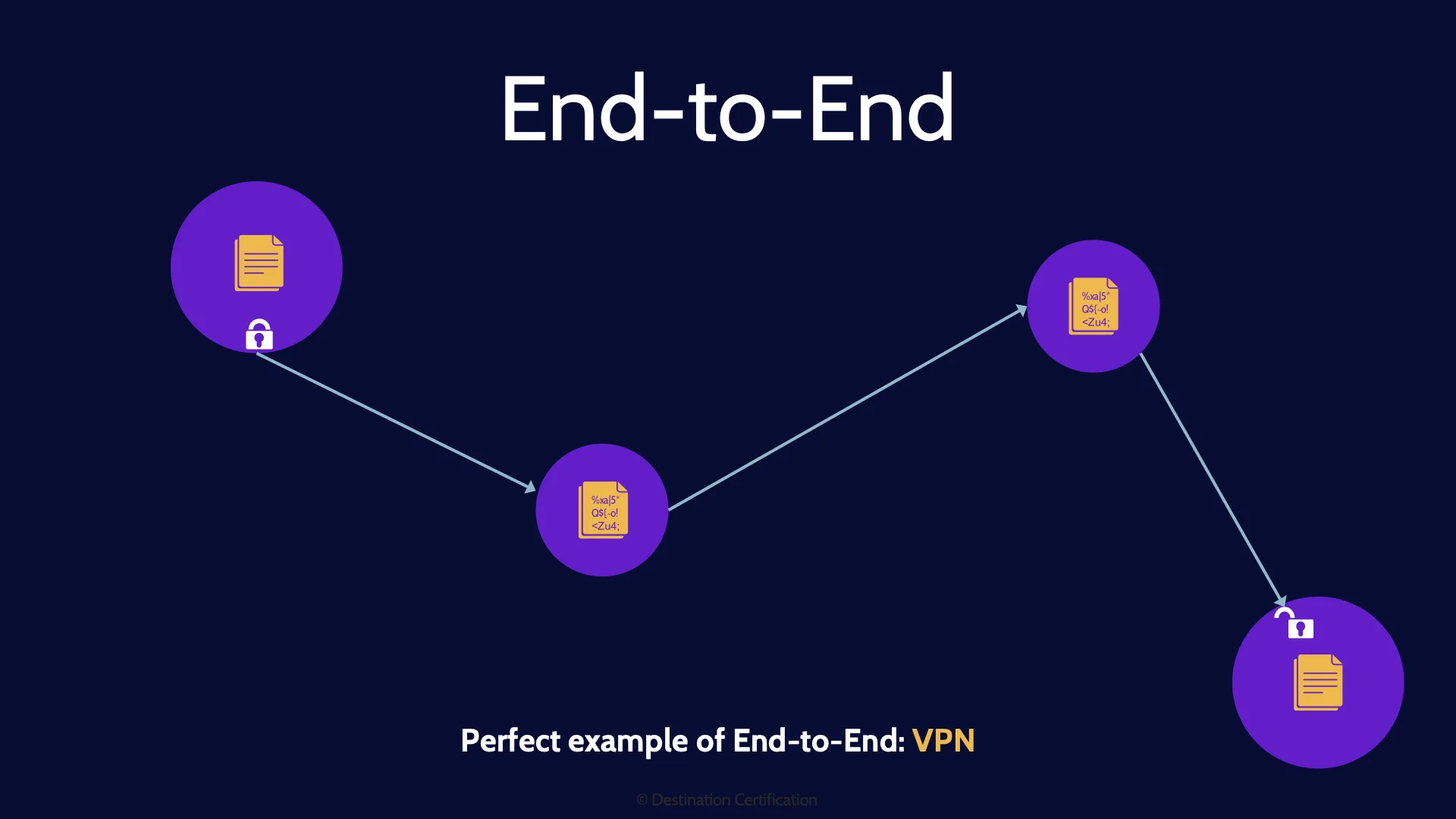
End-to-end encryption means that we encrypt the data portion of a packet right from the sender, and the data remains encrypted through all the nodes (the switches, routers, firewalls, etc.) that it passes through on the way to its intended recipient. The data is then only decrypted once it has reached the recipient. The data is never in plaintext while in transit – it is encrypted and decrypted only at the endpoints.
A perfect example of end-to-end encryption is a VPN, a Virtual Private Network, which I’ll discuss domain 4. The downside of end-to-end encryption, is that the routing information, the source and destination IP addresses for example, must be in plaintext, and visible to anyone – so end-to-end does not provide anonymity.
Link
Directive controls are measures that provide guidance and instruction to personnel on how to handle risks. Directive controls direct behavior. How do we tell someone to do something within an organization? Policies. Policies are a perfect example of a directive control.
Onion
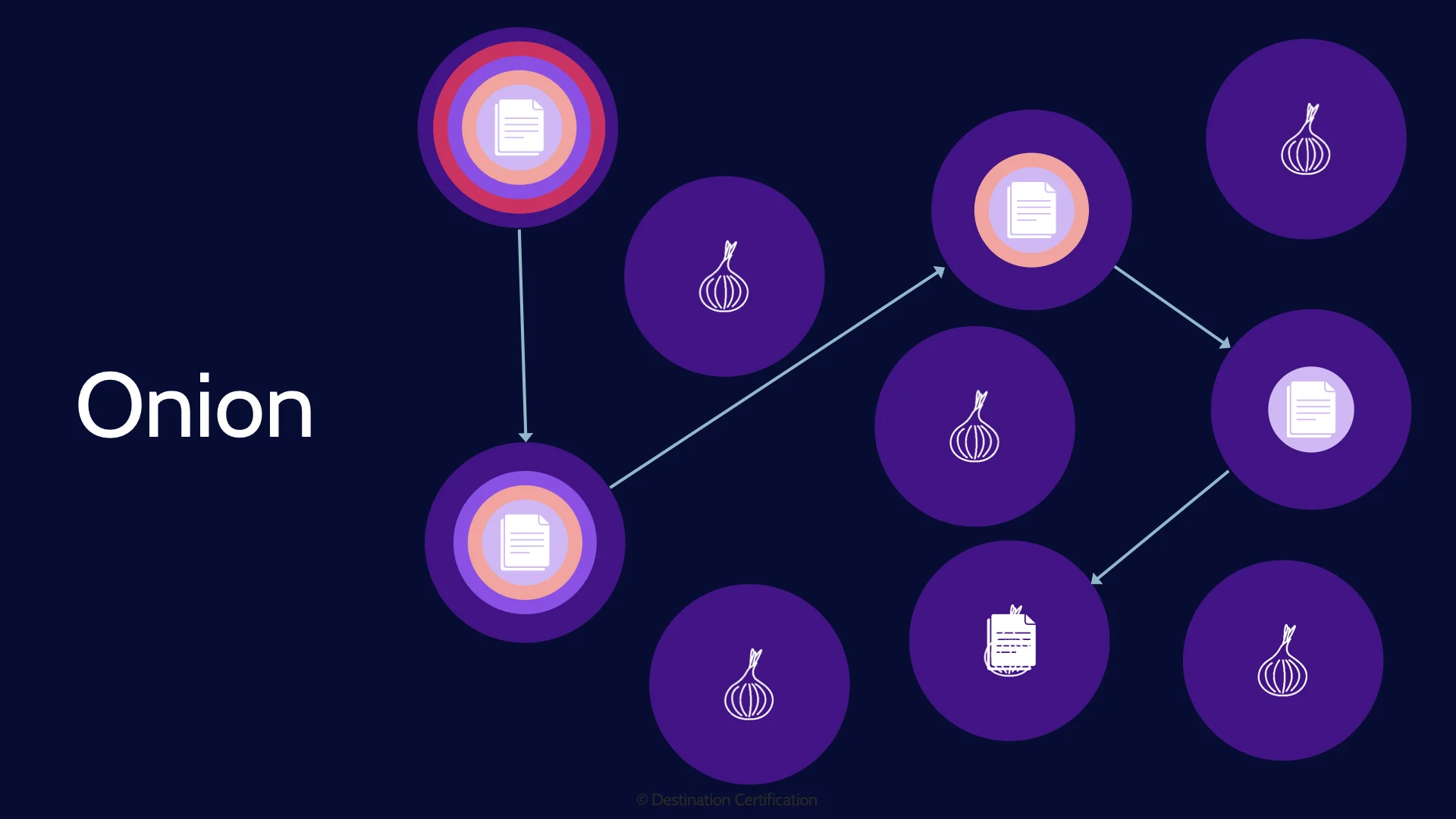
And now let’s talk about Onion Networks. This is a cool idea to provide confidentiality of the data, and anonymity – to make it very difficult to determine who the sender and receiver are while the data is in transit. Here’s how onion networks work: The sender will pre-determine a series of nodes that a packet is going to pass through on its way to the destination. The sender will then encrypt the entire packet multiple times. Each layer of encryption will use the encryption key of a specific node. And thus, when the sender sends the packet, the first node will decrypt the outermost layer of encryption which will reveal the next node to send the packet to. The next node receives the packet, strips off the next layer of encryption which again reveals the next node to send the packet to. And so on until the packet finally reaches the destination which can finally decrypt the data stored within the packet. The big advantage here is that each node along the way only knows which node the packet came from and the next node, but not the ultimate source and destination. And each node has zero access to the encrypted data within the innermost layer. A perfect example of an onion network is TOR – The Onion Router. The big downside of course is performance.
Use
Data in use is inherently more vulnerable than data at rest because, by definition, data in use must be accessible to people and processes to view and edit the data. The major controls we can put in place to protect data in use are good access controls, potentially data loss prevention (DLP) controls to monitor and control what a user is doing with data, and it you want to get really fancy you could potentially use homomorphic encryption, but you don’t need to know about that for the CISSP exam.
Archive
Data Archiving is moving data that is no longer being actively used into a cheaper storage solution for long-term retention. From a security perspective, we need to ensure we retain archived data for a sufficient period of time to meet requirements as defined by the data classification policy, and continue to protect the data based on its classification. Just because the data has been archived on a tape somewhere, does not mean that we get to forget about protecting it.
Retention Period
It’s worth emphasizing here how long data should be retained. We need to ensure data is retained as long as necessary based on compliance, regulatory and contractual requirements – but we also want to ensure we don’t retain data any longer than necessary. I love the expression: you don’t have to worry about a data breach if you don’t have the data. So, retain the data as long as required based on the policy, and then dispose of it. Which leads us to data destruction.
Defensible Destruction
The final way that we protect data, is actually related to how we destroy data when we no longer require it. There are laws, regulations, and contracts that may require us to defensibly destroy data, which means we must securely destroy the data and render it unrecoverable in a manner that will stand-up as reasonable and consistent – we can prove the data is unrecoverable. There are many ways to destroy data and some are much better than others. So let’s first go through three main categories, and then specific techniques.
Destruction
The first and very best category is destruction, which means we physically destroy the media that the data is stored on.
Purging
The next best category is known as purging which means using logical or physical techniques to sanitize data – thus making it so that the data cannot be reconstructed.
Clearing
And finally, the worst category is known as clearing, which means using logical techniques to sanitize the data – thus making it so that the data may not be reconstructed. That’s not super reassuring “may not be reconstructed”
Media Destruction
Ok, now let’s look at the techniques starting from best to worst. The best is of course to physically destroy the media. Ideally melt it. Burn it to the point that all that is left is some smoke and maybe a puddle of metal. There is no way you are getting that data back.
Shred / Disintegrate / Incinerate / Drill
The next best method is to shred, disintegrate or drill a hole in the media. These techniques are not nearly as good, because with the right tools it is possible to read data even off of little shredded pieces of a hard drive or tape.
Crypto shredding
Crypto shredding is the idea that to destroy the data, we encrypt the data with an excellent algorithm like AES 256, and then we destroy every single copy of the encryption key. With the encryption key destroyed, we have effectively crypto shredded the data and made it unrecoverable. Crypto shredding fits between purging and clearing. So long as the key is never recovered, or brute forced or a flaw is not found in the algorithm, then the data cannot be recovered. It has been purged. But if any of those were true the data may be recoverable and has thus just been cleared.
Overwrite / Wipe
Overwriting, wiping or erasure all refer to writing all zeroes or all ones or some combination to all sectors of a storage device replacing the original data with this overwritten data. This process can be done multiple times, but even so, research has shown that pretty much no matter how many times you overwrite the data, some of the original data may be recoverable. Thus, this is a clearing technique.
Format
And the worst method for destroying data is to format the drive. This is the worst technique because formatting by default leaves most if not all existing data on the disk. Meaning the data can easily be recovered with the right tool.
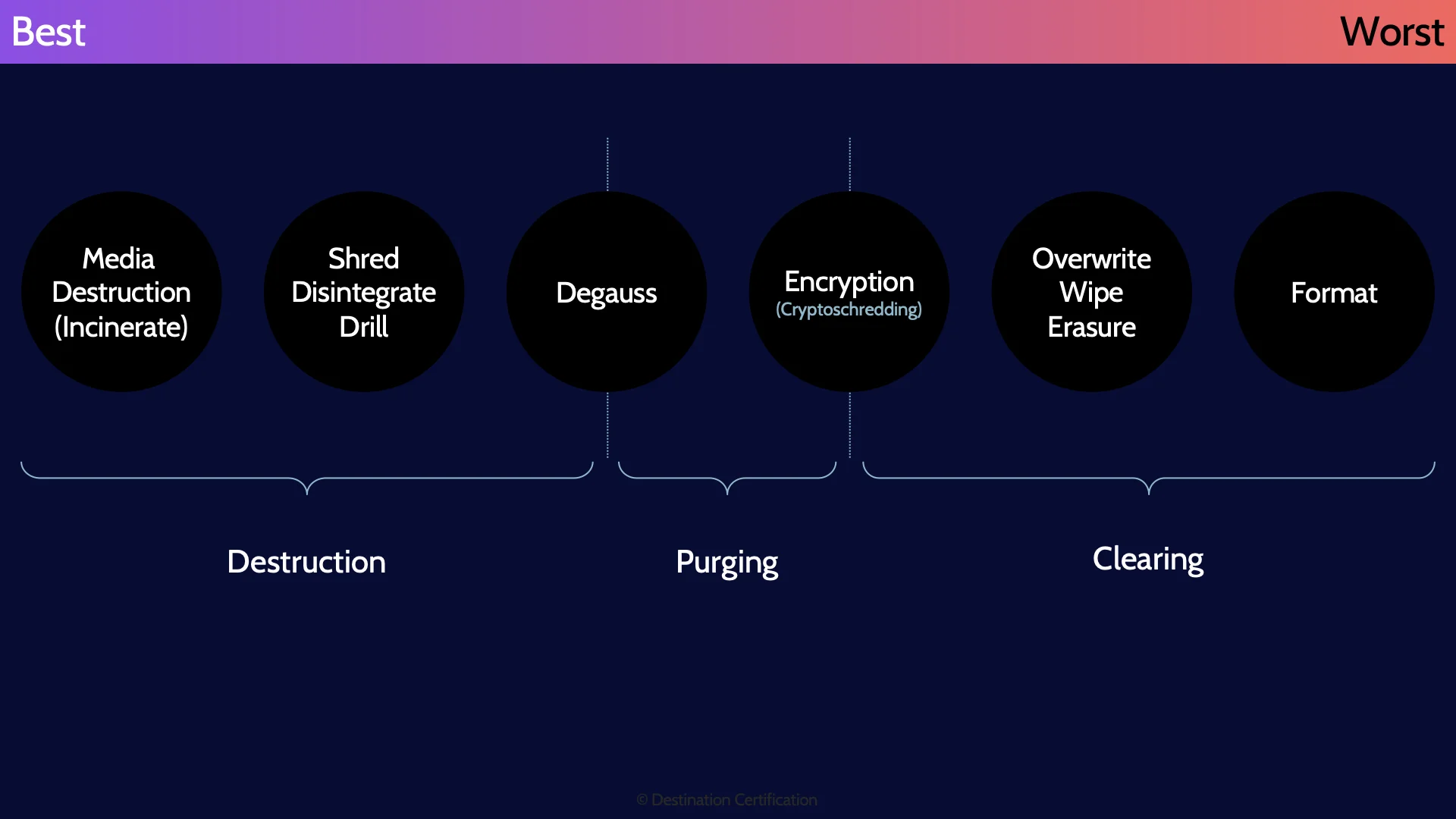
And here is a summary of the different data destruction methods from best to worst.
DRM
Digital Rights Management - DRM - is technology designed to protect the rights of copyrights holders for digital media. Put overly simply DRM technologies encrypt videos, music files, eBooks etc. which then allows the control of who can do what with the media: how many times you can play a movie, what device you can play music on, whether or not you can print an eBook, etc. DRM technologies allow copyright holders to set and enforce rules on how their content is used.
Somewhat related to DRM is Digital Watermarks. Digital Watermarks are way of visibly or invisibly marking the copyright ownership on some digital media. Digital watermarks can be used to trace unauthorized copies back to the source.
One limitation of Digital Watermarks vs. DRM is that digital watermarks can not prevent the unauthorized copying of media. Therefore DRM and digital watermarks are often used together. DRM to encrypt and control access to media, and digital watermarks to provide traceability.
DLP
Data Loss Prevention - DLP solutions are a tools and processes used to ensure that sensitive or critical information is not lost, misused, or accessed by unauthorized individuals.
DLP solutions can help organizations identify, monitor, and protect data in use, data in motion, and data at rest.
A critical requirement for the use of DLP solutions is data classification. DLP solutions can’t prevent every bit of data from leaking out or being misused - so it is critical to know is sensitive data within an organization - hence the need for data classification.
Assess & Review
The final thing we need to think about related to asset classification is that we need to periodically review and assess the classes we have created, and what classification assets have received. Laws, regulations, business requirements all shift over time which may require changing the classes and the classification of assets.

And that is an overview of Risk Management within Domain 1, covering the most critical concepts you need to know for the exam.
Like our MindMap videos? Our CISSP MasterClass provides all of the study materials you need to confidently pass the CISSP exam. We provide over 200 super detailed and engaging MasterClass videos that teach you all of the concepts that we breeze through in these MindMap videos. Additionally, our MasterClass includes over own CISSP guidebook, over 1,100 flashcards, practice questions, our knowledge assessment system, a personalized review guide, a practice exam, and so on.
Put simply, our MasterClass includes everything you need to confidently pass the CISSP exam
Check it out here at destcert.com/CISSP

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
