Asset security and protection are a fundamental part of cybersecurity, and it's the second domain of the CISSP exam, which covers approximately 10% of the questions of the test. It includes the concepts, structures, and controls aimed at protecting the organization's assets—anything that it's important or valuable.
What is the CISSP domain 2?
The ISC2 CISSP certification exam outline includes topics closely related to data protection and security controls throughout its lifecycle with compliance requirements, as seen in domain 2. As per the official ISC2 guide, a security professional must understand data management, longevity and use, addressing end-of-life (EOL) or end-of-support (EOS), and determining data security controls.
Why is asset security important?
Asset protection requires security professionals to be vigilant about protecting assets. A single minor vulnerability can cause a whole system to be exposed to a potential attack, resulting in loss of funds and data and potentially compromising the entire company. A good security professional protects their assets by knowing what they have, classifying them, and protecting them based on their importance to the organization. If you don't understand its significance, you won't be able to protect it.
CISSP Domain 2: Asset Security overview
Asset security is easy to understand but hard to implement, especially for larger companies with considerable assets to protect. Domain 2 provides an overview of the steps involved in asset security to address some issues that security professionals often encounter while implementing them. The following is an overview of every critical point of CISSP domain 2.
2.1. Identify and classify information and assets
Asset Classification
Asset classification can be defined as assigning assets the level of protection they require based on their value to the organization. The protection should always be found in the asset value, and the owners of the asset are always in the best position to understand the actual value that the asset represents to the organization.
Expect to be tested on: Value of asset classification
Classification Process
Data classification ensures that data receive an appropriate level of protection. It sounds simple, but it's a complex process. It requires the right tools, procedures, education, and training to be effective. As a result, many organizations struggle with optimizing their data classification.
Expect to be tested on: Asset classification steps
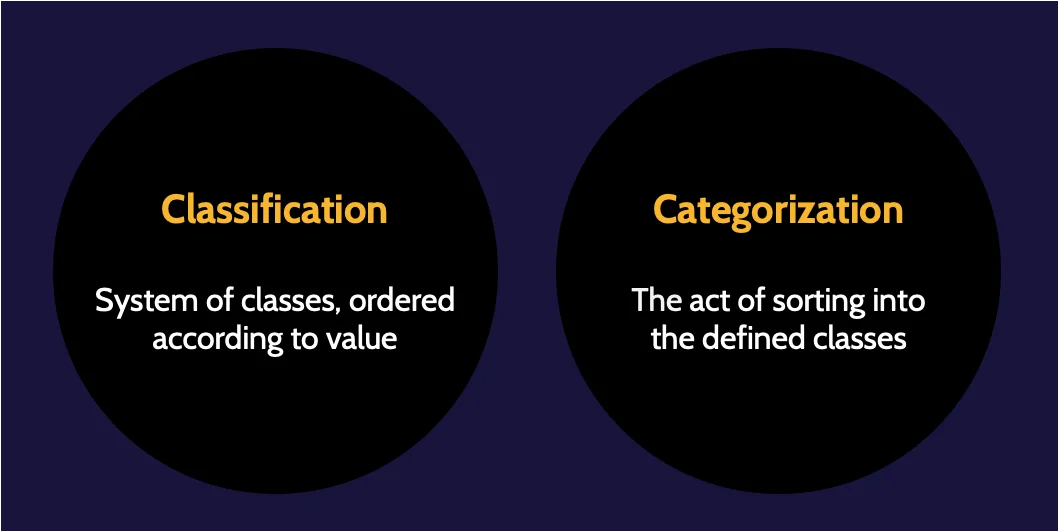
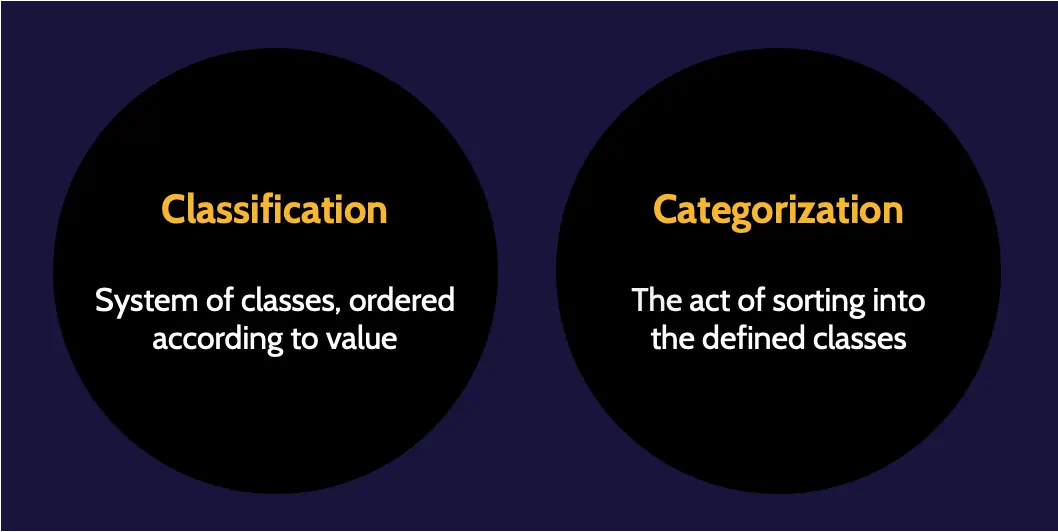
Classification versus Categorization
Classification by itself is simply a system of classes set up by an organization to differentiate asset values and, therefore, protection levels. The act of assigning a classification level to an asset is called categorization. Ideally, all assets should be categorized into a classification system to allow them to be protected based on value.
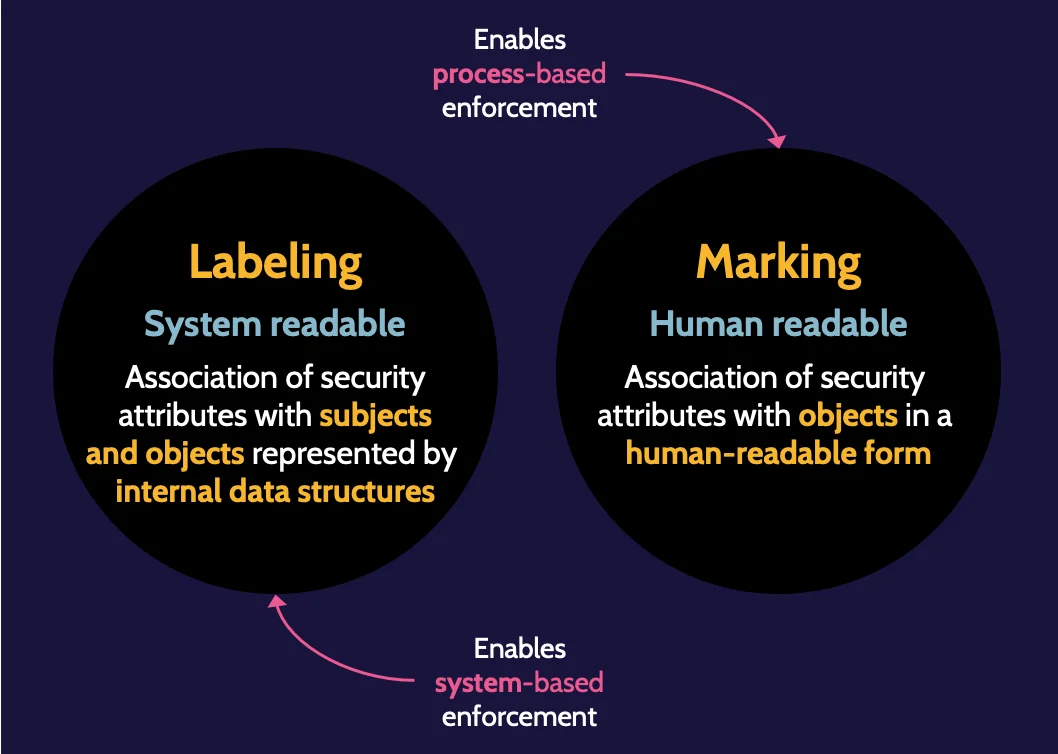
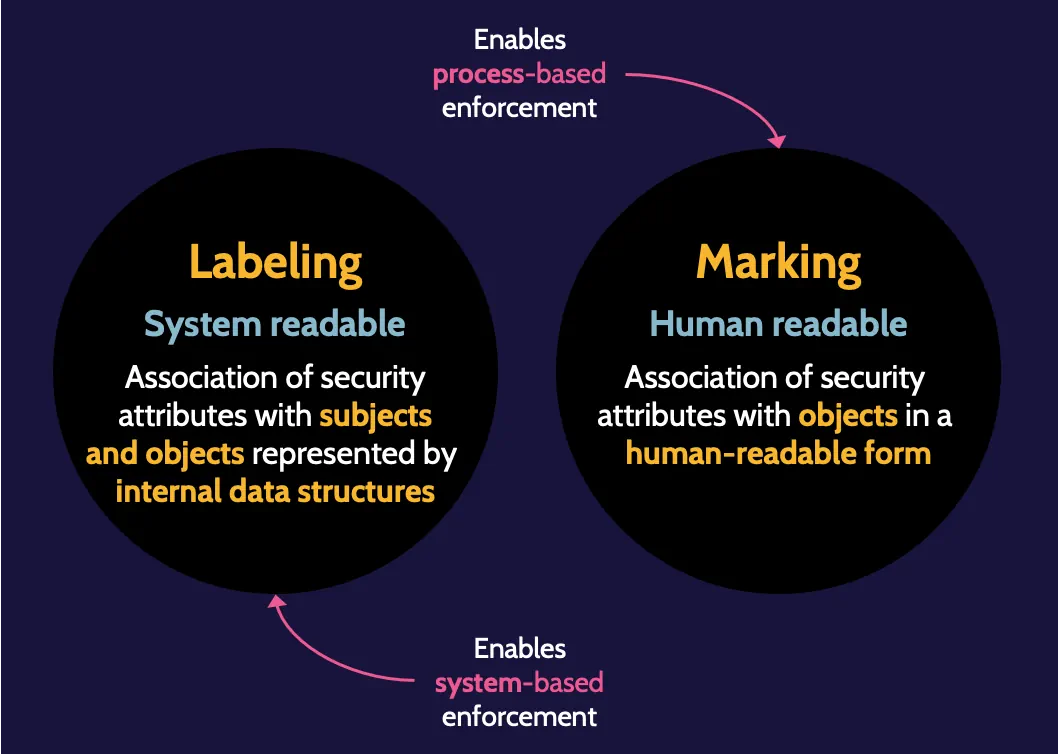
Labeling and Marking
Labeling refers to the classification of the asset and is system readable, whereas marking refers to the handling instructions of the asset and is human readable. It should be consistently applied to all assets within an organization.
Expect to be tested on:
- Main differences between labeling and marking
- Cost-effectiveness of different labeling approaches
2.2 Establish information and asset handling requirements
Media Handling
Information and handling requirements are other essential elements to consider when classifying assets. The more valuable the asset, the more controls are needed to restrict who can handle that asset. Handling requirements are based on the classification of the asset, not the type of media.
2.3 Provision resources securely
Data Classification Roles and Responsibilities
- Data Owner/Controller: the person who directly interacts with the asset the most and is accountable for the protection of data.
- Data Processor: responsible for processing data on behalf of the owner/controller.
- Data Custodian: they hold technical responsibility for data and are responsible for the custody of systems/databases
- Data Steward:they hold business responsibility for data.
- Data Subject:individual to whom personal data pertains.
Expect to be tested on:
- The classification process begins with identifying the owners
- Owners are ultimately accountable for an asset
- Understand different roles and responsibilities
Data Classification Policy
Data classification policy is concerned with managing information to ensure that sensitive and valuable information is protected and handled accordingly, and considers laws, regulations, privacy requirements, customer requirements, cost of creation, operational impact, liability, and reputation.
2.4 Manage data life cycle
Information Life Cycle
The concept of the information life cycle is founded on the principle that proper controls should be in place at the time of creation and throughout the life cycle. Data must be protected at each stage:
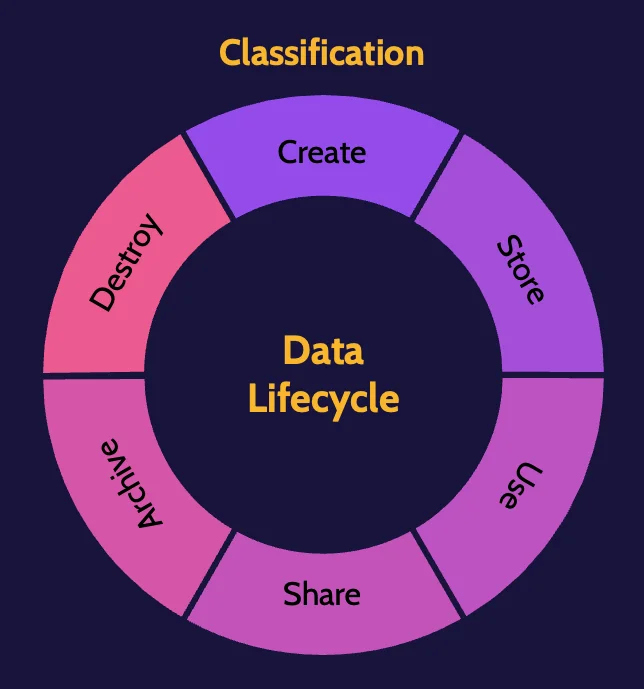
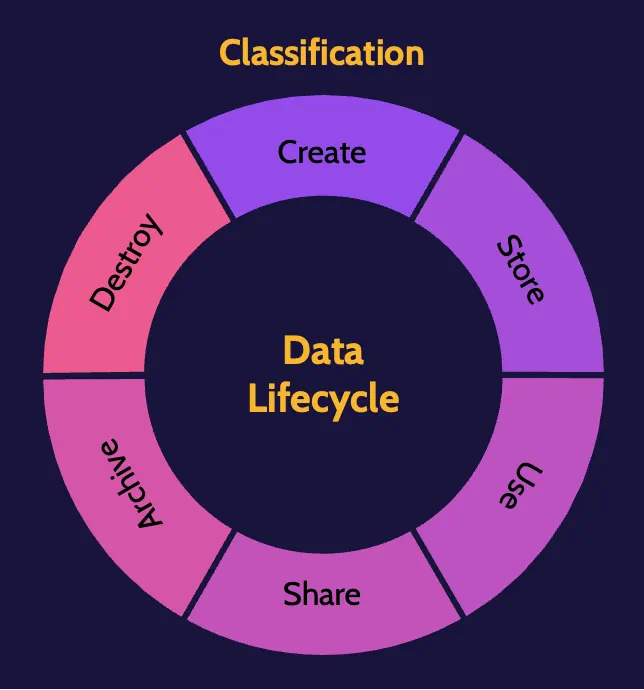
Data Destruction
Depending upon how data is removed from media, remnants of that data typically remain. This means that a significant amount of that data may be recovered by a determined individual. Various methods exist to ensure data removal, and the focus these days is on what is known as defensible destruction—or proving that there's no possible way for anyone to recover destroyed data.
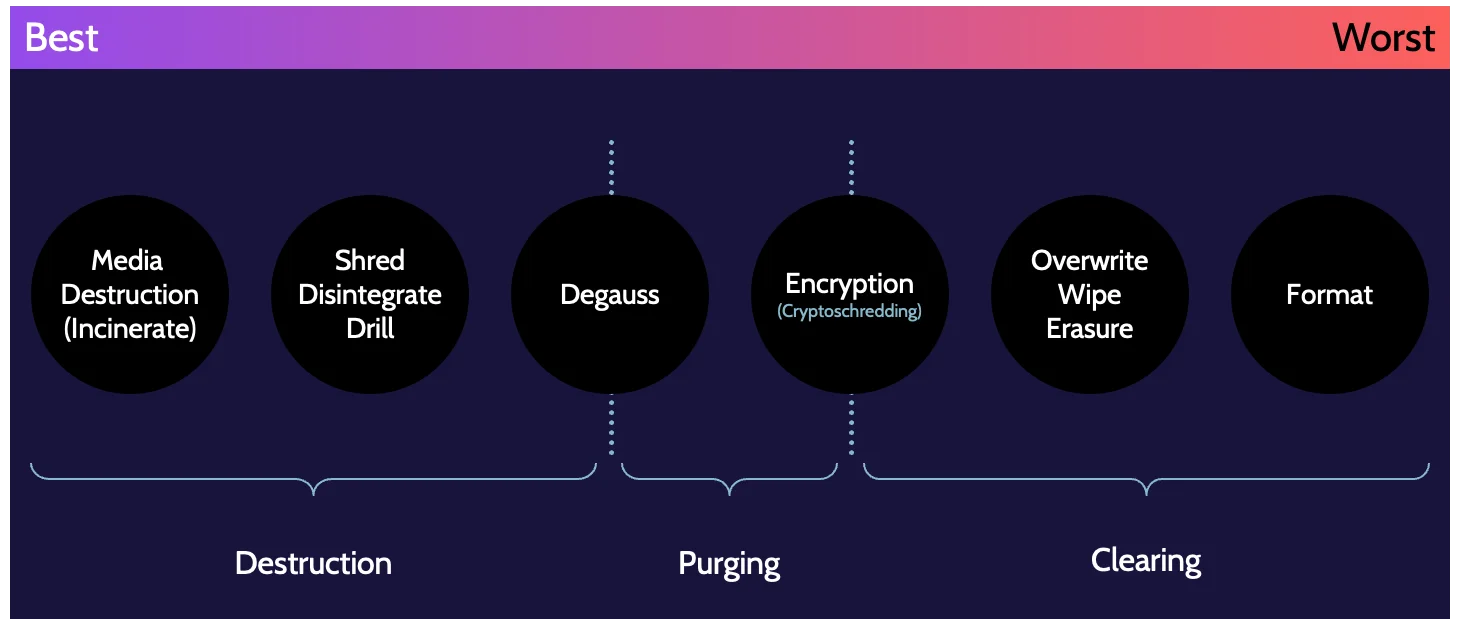
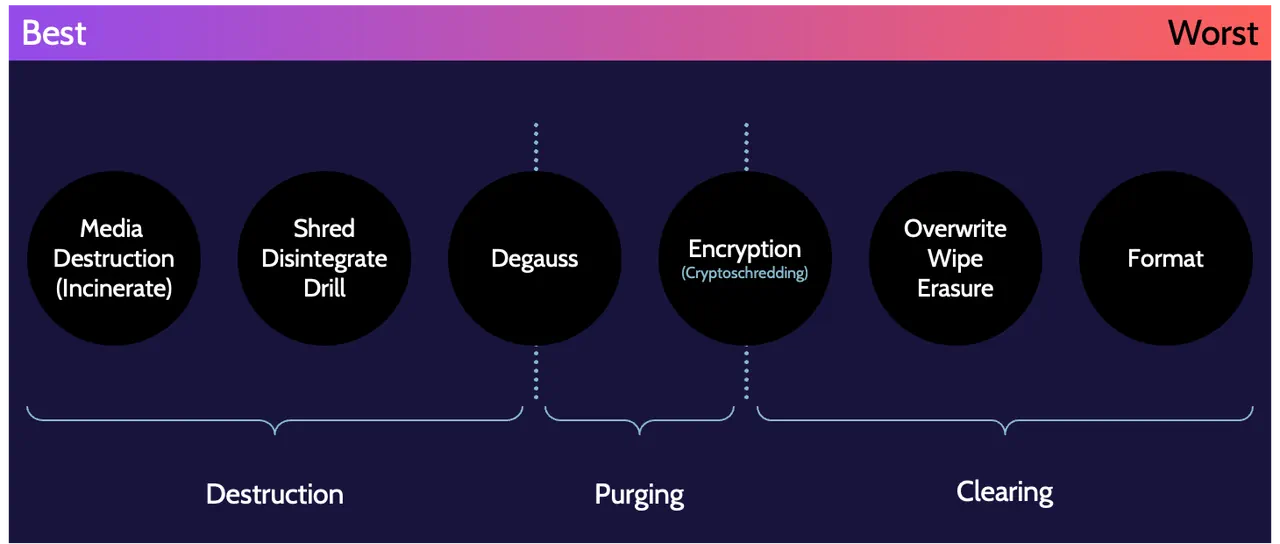
Expect to be tested on:
- Categories of sanitization
- Most effective/secure method of sanitization
- The best method for dealing with data remanence in the cloud
2.5 Ensure appropriate asset retention
Data Archiving
Data archiving is part of the asset life cycle and includes requirements for protecting archived data. An appropriate retention policy should drive it. Laws, regulations, industry standards, and similar guidelines can all play a role in determining retention requirements and how data is archived.
Expect to be tested on:
- Considerations related to data archiving
- Elements of data archiving policies
2.6 Determine data security controls and compliance requirements
Data can be in one of three states at any given time: data at rest, data in transit, and data in use. The data security controls that protect data may be completely different depending on which of these states the data is in. It is therefore important to understand what security controls are required for each state.
Protecting Data at Rest
Data at rest refers to data that is stored somewhere. This section comprises methods to protect data in transit—encryption, access control, backup, and restoration.
Expect to be tested on: The best way to protect the confidentiality of data being migrated to the cloud
Protecting Data in Transit
Data in transit, also sometimes referred to as data in motion, refers to data that is moving across networks, like an organization's internal network or the internet. This section comprises methods to protect data in transit—end-to-end encryption, link encryption, and onion network.
- End-to-end encryption: data portion of a packet is encrypted immediately upon transmission from the source node, and the data remains encrypted through every node
- Link encryption: the packet header and data are encrypted between each node. Encrypting the packet header hides the routing information of packets traversing a network. However, unlike with end-to-end encryption, the header and data are decrypted at each node, so header information and plaintext content are also available at each node.
- Onion Network: a very effective method of protecting data in transit, as it essentially provides complete confidentiality and anonymity through the use of multiple layers of encryption. By providing confidentiality of data as well as anonymity, an onion network makes it very difficult to determine the sender and receiver while data is in transit.
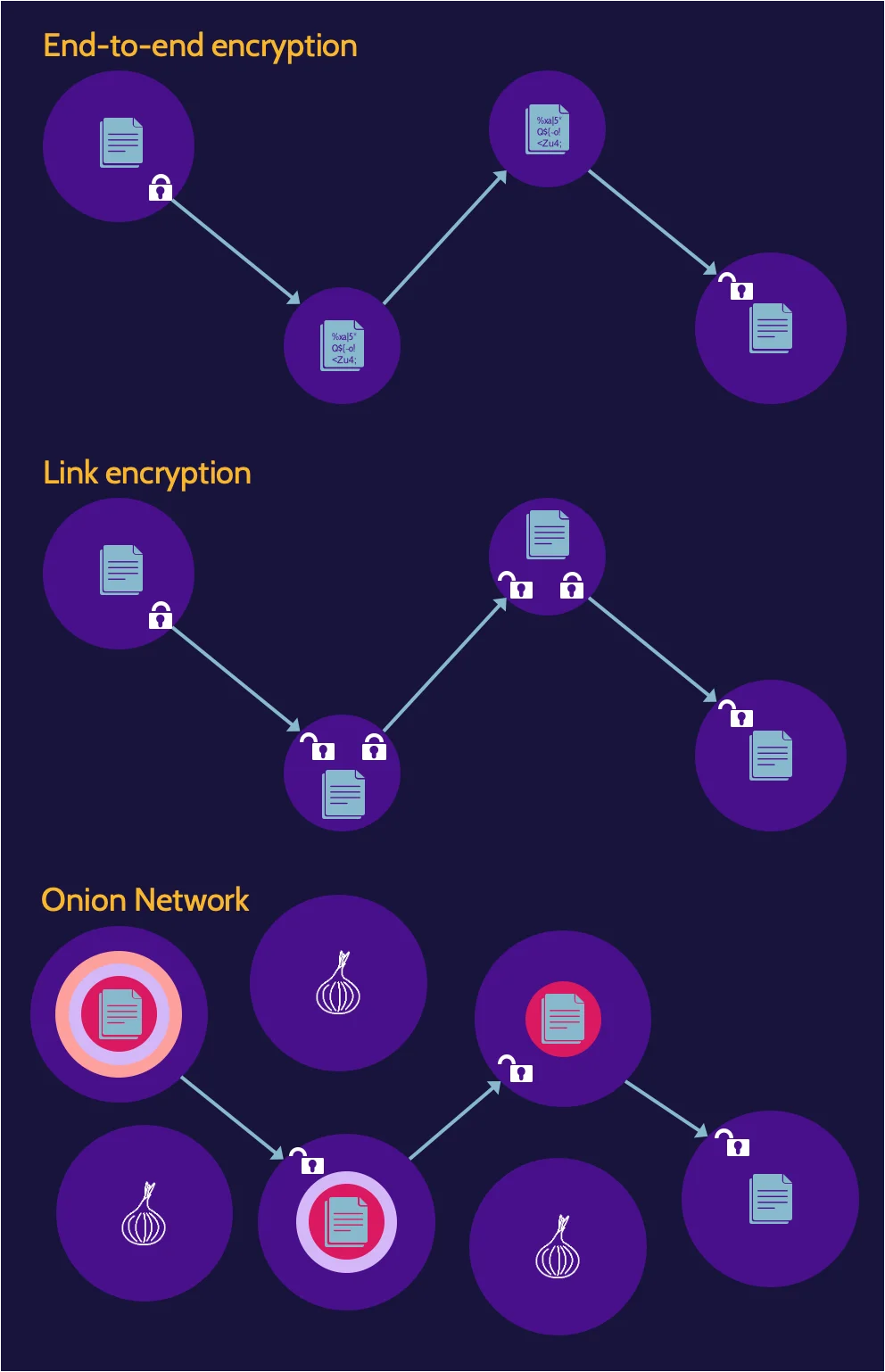
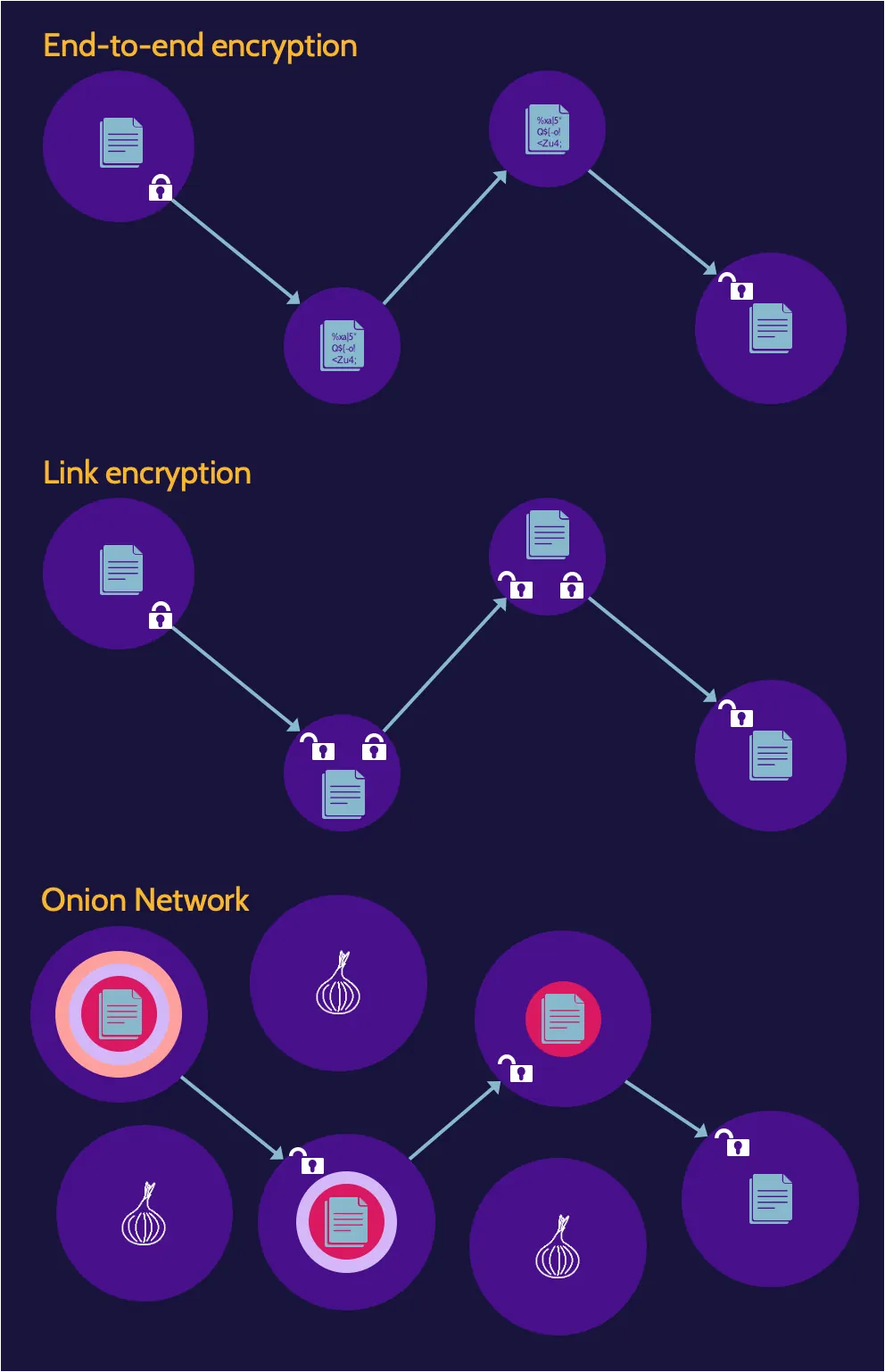
Expect to be tested on:
- The best way to protect the confidentiality of data being migrated to the cloud
- An onion network provides anonymity and protection of data
Protecting Data in Use
Data in use refers to data that is being used in some type of computational activity. Ways to protect data in use are through homomorphic encryption, role-based access control (RBAC), and digital rights protection (DRP) or data loss prevention (DLP).
Information Obfuscation Methods
Obfuscation is the action of making something obscure, unclear, or unintelligible; in other words, hiding it. It makes something harder to understand. Security professionals need to know different obfuscation methods for the CISSP domain 2.
- Concealing data: it completely removes access to sensitive data.
- Information Pruning/Pruning Data:primarily takes place in nonproduction environments and involves the removal of sensitive data from attributes.
- Fabricating data:creating fake data to replace real data or sensitive data
- Trimming dataremoves part of an attribute's value and is typically used for identification purposes.
- Encrypting data:creates ciphertext of a value and can be done at the attribute, table, or database levels.
Expect to be tested on: Why obfuscation is used
Digital Rights Management (DRM)
DRM protects intellectual property (IP) assets and the rights of asset owners. Security awareness must take DRM techniques into account and know that it is the legal basis for protection in the United States through the Digital Millennium Copyright Act (DMCA).
To achieve these ends, DRM techniques include:
- Licensing agreements that restrict access
- Encryption
- Embedding of digital tags that tie content to specific license holders, theoretically preventing sharing with others
- Use of related technologies that restrict copying or viewing of certain content
Data Loss Prevention (DLP)
Data loss prevention focuses on identifying, monitoring, and protecting data. It takes place in three contexts: data in use, data in motion, and data at rest. In each context, DLP tools attempt to detect and prevent data breaches and potential data exfiltration.
DLP system can be used to protect:
- Data in use
- Data in motion
- Data at rest




