Alignment of Security Function to Business Strategy MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to the alignment of the security function to business goals and objectives. This is the first video in our complete set of MindMap videos. This MindMap series is meant to help you review the key topics you need to know to confidently pass the CISSP exam.
There are 2 other MindMap videos for Domain 1 and a total of 30 of these MindMap videos. I have included links to all the other MindMap videos in the description below.

Before I launch into this first MindMap, I’d like to give you a critical bit of advice that will make it massively easier for you to study for and confidently pass the CISSP exam. You need to have the right mindset in your studies and especially on the exam. CISSP is a management level certification, so you need to be really careful not to think too technically. You need to think like a CEO. I’ll explain this critical mindset more at the end of the video.
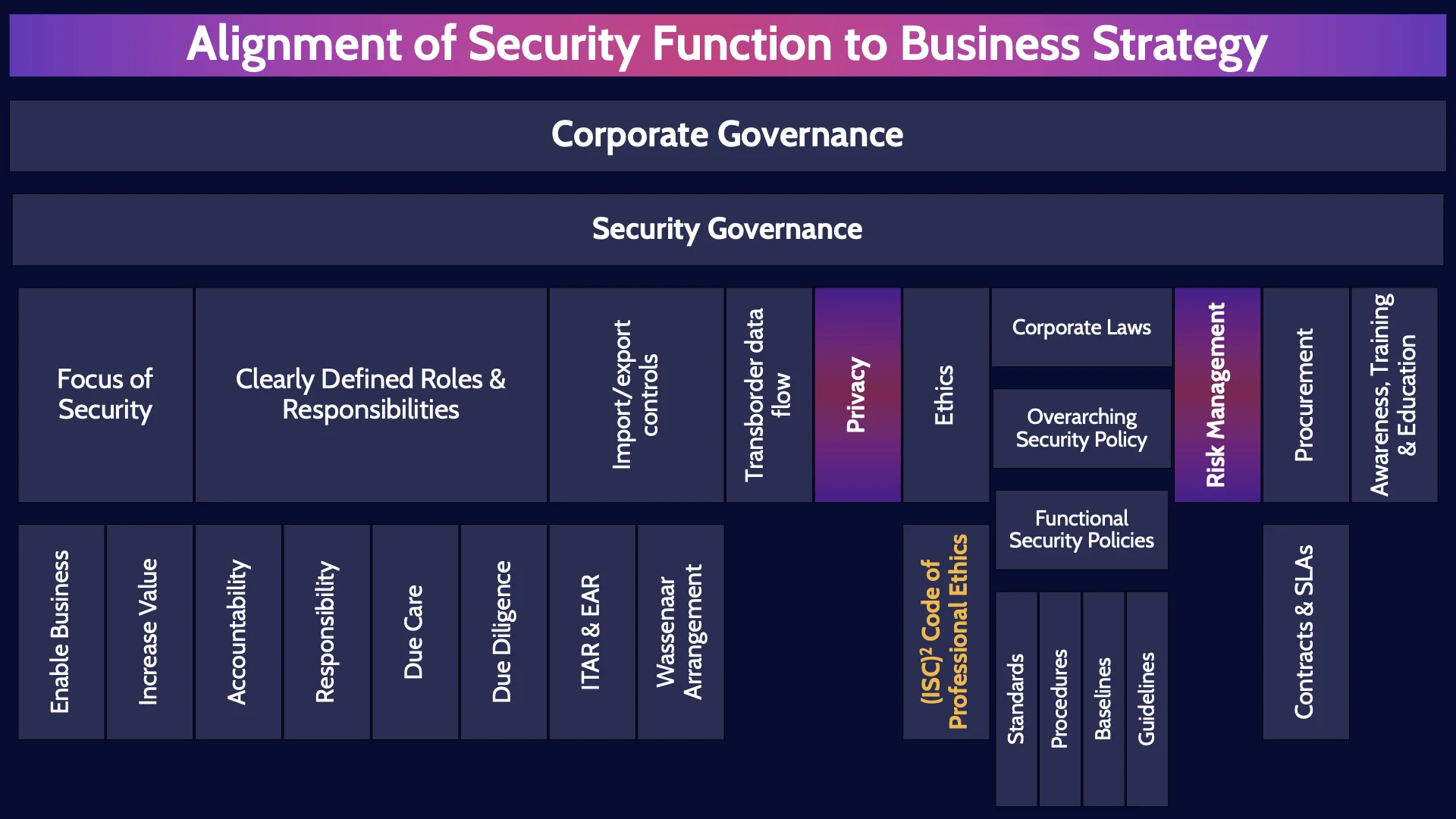
Corporate Governance
Alright, so starting high-level and thinking like a CEO would, lets launch into this first MindMap and define Corporate Governance. Corporate Governance is the system of rules, practices and processes by which an organization is directed and controlled to achieve its goals and objectives that are typically focused on increasing the value of the organization.
So fundamentally, corporate governance is about ensuring an organization has clear goals and objectives and everyone in the company is aligned towards achieving those goals and objectives.
Security Governance
Security Governance then is the system of rules, practices and processes by which the security function is directed and controlled. A crucial part of security governance is aligning the security function to the overall organizational goals and objectives. So that security can HELP the business achieve it’s goals and objectives. So that security is an enabler for the business. This is something crucial that we always need to keep in mind as security professionals - our job is to help the business achieve it’s goals and objectives - to be an enabler for the business.
We don’t want to be the shop of no - we shouldn’t always be telling the business: no you can’t do that it’s too risky. We should ideally be saying something more like: here’s the risks, and here’s how we can help to mitigate those risks so that the organization can achieve it’s goals and objectives.
Focus of Security
So now you know the focus of security: to help the organization achieve it’s goals and objectives.
Enable Business
To be an enabler to the business.
Increase Value
To help increase the value of the organization and not just be a cost center.
Clearly Defined Roles & Responsibilities
A critical part of governance is having clearly defined roles and responsibilities. So people know exactly what they're supposed to be doing - what they are accountable for and what they responsible for.
Accountability
Lets spend a minute here on these terms: Accountability and Responsibility. There terms are often used interchangeably, but there is actually a massive difference between them that is very important to understand from a security perspective. Lets start by defining Accountability. Accountability means the ownership of something. Accountability means the ultimate answerability, blameworthiness, and liability. Put simply accountability is - where the buck stops. The throat that gets choked if something goes wrong.
And really crucially - accountability can NEVER be delegated. The owner of an asset is accountable for the security of their asset, and they can never delegate that accountability to a subordinate, contractor or service provider - they can’t delegate their accountability to anyone.
Responsibility
What can be delegated is responsibility. The responsible party will implement and enforce controls based on the direction of those that are accountable. A perfect example is a Public Cloud Service Provider. The CSP will be responsible for storing, processing and securing a customer’s data. But ultimately the customer remains accountable for the security of their data. The customer cannot outsounce the accountability for protecting their data, but they can delegate the responsibility. The concept of accountability vs. responsibility is going to come up again and again - it’s crucial to understand the difference.

Here’s a handy table that summarizes the differences between accountability and responsibility.
Due Care
Due care is the responsible protection of assets based on the goals and objectives of the organization
Due Diligence
Due diligence is the demonstrated ability to prove due care to stakeholders (upper management, regulators, customers, shareholders, etc.)
Import/export controls
There is an interesting bit of security history related to import/export controls. I’m wildly oversimplifying here, but essentially during the 1970s and 80s some amazing advancements were happening in cryptography. Super secure new algorithms like DES were being created and whole new amazing techniques like asymmetric cryptography were invented. These new algorithms and techniques essentially allowed data to be encrypted such that no one in the world could decrypt it - including organizations like the NSA. This was very upsetting for certain organizations, like the NSA, who wanted to be able to decrypt and read anyone’s data. I need to stop picking on the NSA here… they might be listening…
So laws were put in place to restrict the export of certain cryptographic algorithms and systems - to make sure they didn’t get into the hands of say the evil soviets. These are serious laws and violations could see you thrown in federal prison.
ITAR & EAR
The two major export laws you need to know about are ITAR & EAR. They both restrict the manufacturing, sales and distribution of specific technologies, products, software, and services. These laws restrict the export of certain cryptographic systems.
ITAR - the International Traffic In Arms - focuses on the export of defense articles (things like missiles, and satellites), technical data and defense services. Keyword there related to ITAR is that it focuses on defense related items.
EAR - the Export Administration Regulations - Regulates dual-use items not covered by ITAR, but also still applies to some defense-related items.
Wassenaar Arrangement
The Wassenaar Arrangement is very different from ITAR and EAR - importantly, the Wassenaar Arrangement is voluntary - not a strict law - and it’s also a multinational agreement between 42 signing members / 42 countries. The Wassenaar Arrangement is a voluntary export control regime where signatories exchange information on transfers of conventional weapons and dual-use goods and technologies.
Transborder data flow
Now another type of law that is very relevant today - transborder data flow laws. Also commonly referred to as data residency laws, or data localization laws. These laws are focused on restricting or preventing the flow of data across physical borders. For example, many countries require that the personal data collected from their citizens be stored on systems within the country.
Privacy
Privacy is not a massive topic on the CISSP exam, but it is large enough to warrant it’s only MindMap. So for now I’ll simply say you cannot achieve privacy without security and we’ll talk more about privacy in the next MindMap video.
Ethics
Ethics are very important to address as part of your security program. Organizations want their employees to act ethically and consistently - the challenge is that each of us have different ethical values. So for an organization to have consistent ethics across all their employees, they must codify their ethics - write them down in a policy. Policies are essentially coporate laws. We’ll talk about that in a moment.
What are ethics based on? A good answer is that ethics are based on doing nothing that is harmful to anyone else.
ISC2 Code of Professional Ethics

Now this part is critical to memorize for the exam: The ISC2 Code of Professional Ethics. ISC2 takes this very seriously. It is a requirement of you becoming a CISSP that you agree to abide by this code of ethics. (ISC)² wants to make sure you know this code of ethics and how to interpret them - so you are going to see at least a question or two about these on the CISSP exam. I’m going to read them out here, memorize the wording and the order. These are meant to be acted upon in order:
- Protect society, the common good, necessary public trust and confidence, and the infrastructure.
- Act honorably, honestly, justly, responsibly, and legally.
- Provide diligent and competent service to principals.
- Advance and protect the profession.
Corporate Laws
Lets now get into an important discussion of Policies. And as I mentioned earlier, Policies are essentially corporate laws. Policies are how we direct behavior within an organization. Policies tell people what they MUST do.
Overarching Security Policy
The Overarching Security Policy defines an organization's overall approach to security. The Overarching Security Policy is provided and supported by the Board of Directors and senior management. The policy defines the goals & objectives for the security function and ensures security is aligned with the overall business goals and objectives.
Functional Security Policies
Functional security policies, on the other hand, are more detailed policies that address specific security requirements and practices, such as access control, encryption, incident response, and data backups. An organization will have a functional policy for each of these, and many more.
Good policies are simple easy to read documents that state simple rules, such as: every laptop must have malware protection.
Policies are corporate laws. Policies tell people what they must do.
Standards
Standards define specific mandatory hardware and software mechanisms - for example an organization's standard might state that Norton Antivirus is the required anti-malware solution for all Windows laptops.
Procedures
Procedures are step by step mandatory actions - for example an organization could have a procedure for how to install Norton Antivirus on windows laptops.
The exact steps that must be followed to correctly install and configure the anti-malware software. Procedures are essentially a step-by-step set of instructions / actions for how to do something.
Baselines
Baselines are minimum levels of security, and define mandatory configurations for security mechanisms and products - for example an organization could have a configuration baseline for window laptops. The configuration baseline is essentially a checklist of all the things that need to be done to correctly configure and lock down a laptop before it starts being used - for example the configuration baseline would require that at a minimum, the host based-firewall be enabled, certain patches installed, that Norton Antivirus be installed and configured correctly - btw, I keep mentioning Norton here in the hopes of getting sponsored, so if you’re listening Norton.. eh-hem.
Guidelines
Guidelines are recommended actions - listen carefully here, guidelines are NOT mandatory - they define what someone should do - NOT what someone MUST do. Guidelines are useful when an organization knows they should be doing something but they haven’t fully implemented it yet. So for example, the organization might want to have multi-factor authentication for all administrative accounts, but if there are systems that don’t support that yet, the organization is setting itself up for failure if they create a mandatory requirement of MFA for admin access on all systems. Instead, the organization can create a guideline - it would be good to have MFA for admin access to all systems, but it’s not a requirement. Yet.
Risk Management
Risk Management is a super important topic. Risk management is a critically important tool that we as security professionals can use to figure out how to best protect the assets of the organization with the limited resources that we have. There is a MindMap dedicated to Risk management, and I’m mentioning it here as risk management is a critical part of security governance.
Procurement
Procurement. Security must be involved in the procurement process - right from the start of the process. This starts with understanding and validating the business requirements for whatever is being procured. If it’s a service being procured, then the security requirements are documented in the SLR - the Service Level Requirements document. The requirements documented in SLR will be used in the procurement process to evaluate how well each service meets the security requirements.
Contracts & SLAs
Once a particular service provider is selected, then the requirements listed in the SLR will be translated to a new document, the SLA - the Service Level Agreement. The SLA is an addendum to the legal binding contract - making the SLA legal binding as well. The SLA describes the service to be provided, the service targets, specifies responsibilities, etc. Critically, the SLA is used to clearly communicate requirements to a service provider - to say: hey, service provider, I need you to make sure you are doing this, that and the other thing.
Going back to what I mentioned earlier, accountability can never be outsourced, but responsibilities can. So the SLA is a crucial document that the owner of an asset uses to make sure the service provider clearly understands their responsibilities.
Awareness, Training & Education
Who is responsible for security? Everyone! This is true. Everyone is responsible for security, but it’s not good enough to just say: everyone is responsible for security. Everyone needs to know what specifically they are responsible for from a security perspective and how they are supposed to do whatever they are responsible for. And that’s why the last piece we’ll talk about here is Awareness, Training & Education.
I’m going to give you succinct definitions of each.
Awareness is an informal process of communications (such as emails, posters, etc.) with the goal of changing cultural sensitivity to a given topic or issue - for example, making employees aware of this thing called phishing and they should be careful about what links they click on in emails.
Training is semi-formal and provides specific skills necessary to perform something related to security. For example if a company buys a bunch of Cisco firewalls, then some employees are going to need to be trained on how to deploy and manage Cisco firewalls.
Finally, education is about teaching fundamental concepts. Our CISSP MasterClass is a perfect example of education. We teach folks the fundamental concepts of security so they can be a better security professional and pass the CISSP exam.

And that is an overview of Security Governance within Domain 1, covering the most critical concepts you need to know for the exam.
As an added bonus in this first MindMap video I want to share with you the most important advice I can give you for passing the CISSP exam. You need to approach your studies and especially the exam with the right mindset.
As I said, the CISSP exam is a management-level certification. If you answer the questions on the exam with a technical mindset you will very likely fail – unfortunately.
So how should you approach your studies and the exam? By thinking like a CEO. I made a video on this mindset of thinking like a CEO, which you can watch - for free - by clicking on this link here [point]. I would highly recommend you take a few minutes to watch the video. We’ve trained and guided thousands of people to confidently passing the CISSP exam over the last 20 plus years, and we’ve received hundreds of emails over the years from folks saying: thinking like a CEO worked. It was the single biggest factor in me passing the exam.
So, that’s why I’m sharing this with you. I know it works, and it will help you pass the CISSP exam.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies.
