Malware MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major malware, and anti-malware topics in Domain 7, to understand how they interrelate, and to guide your studies and help you pass the CISSP exam.
This is the third of six videos for domain 7. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass.
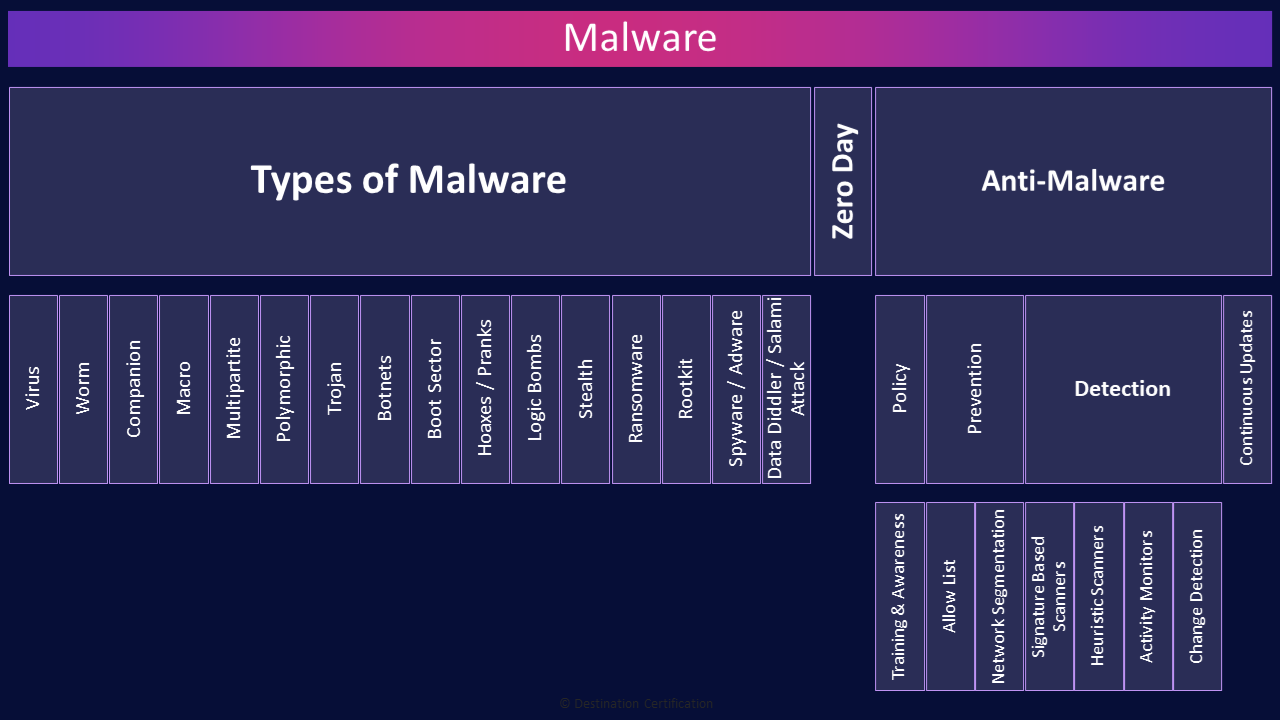
Malware
Let’s start by defining Malware. Malware is any software that is intentionally written to do something malicious or harmful to a system, network, device, etc.
Types of malware
Malware is the encompassing term for all the different types of malicious software we are about to talk about. I am going to provide very concise definitions of the characteristics of each type malware and keep in mind that it is not uncommon for a piece of malicious software to exhibit one or more of these characteristics.
Virus
A virus, is a piece of malware that must be triggered by the user.
Worm
Worms are self-propagating as they can discover a vulnerable system, exploit the vulnerability, infect the system and begin the process again of discovering new vulnerable systems. This allows worms to potentially spread extremely rapidly because they can self prorogate.
Companion
A companion does not modify a file. Rather it creates a new file with a similar name to a commonly executed file and relies on the user accidentally executing this new malicious file.
Macro
Macro malware are malicious code written in a macro language like VBA for Microsoft Excel. The macro code runs within an application, like Excel, which is why you get such dire warnings about opening a macro enabled spreadsheet from an email.
Multipartite
Multipartite is a piece of malware that spreads in multiple different ways. Think Stuxnet. It first infected via a USB stick using a USB vulnerability and then Stuxnet spread over the local area network using a network based vulnerability.
Polymorphic
Polymorphic malware can change or morph characteristics about itself to evade detection, primarily by a signature based anti-malware scanner
Trojan
Trojans mislead users of their true intent. They are disguised as legitimate software the user would want, but they actually contain malicious code.
Botnets
A botnet is not a piece of malicious software, but rather multiple systems that have been infected allowing the systems to be remotely commanded and controlled. When harnessed together botnets of hundreds, thousands, and even millions of machines can send vast amounts of spam, perform Distributed Denial of Service attacks, or mine for crypto currency.
Boot Sector
A boot sector infector is a type of malware that copies itself into the boot sector or master boot record of a hard drive. The malware can then run when the system is booted or started, long before any anti-malware software or other security measures are running. Making boot sector infectors difficult to detect and remove.
Hoaxes / Pranks
Hoaxes and pranks are forms of social engineering, not code. Hoaxes are meant to be harmful whereas pranks are just for fun.
Logic Bombs
Logic bombs are malware that are triggered by a certain logic or condition being met. The time of day. The day of the year. If an employee is still in the HR database. Etc.
Stealth
Stealth is malware that is specifically designed to actively disable the security tools on a system and therefore not be detected - for example: disable the anti malware software, or the host-based IDS.
Ransomware
Ransomware is malware that is designed to deny access to system or files – usually by encrypting them – until a ransom is paid – typically via bitcoin.
Rootkit
Rootkits are malware that infect the operating system of a computer. The most nefarious rootkits are known as kernel mode rootkits, which as the name implies allows the malware to compromise the system kernel and gain privileged access making rootkits exceedingly difficult to detect and remove.
Spyware / Adware
Spyware is malware that allows an attacker to gain information about a computer system – to spy on it. And adware causes all sorts of pop-up advertisements.
Data Diddler / Salami Attack
Finally, data-diddlers. This is malware specifically designed to diddle with data, to make small changes to data over a long period of time to evade detection. A type of data diddler is a salami attack which specifically target financial transactions. For example, shaving fractions of a penny off of many transactions.
Zero Day
A zero-day is a vulnerability in a system that is at first unknown to the defenders, those that would patch or configure the system to protect it. Zero-days are particularly dangerous because they are flaws that are being exploited before anyone knows to detect and remediate the vulnerability.
Anti-Malware
Now let’s talk about how we can prevent, detect and defend our systems against these various types of malware.
Policy
We first need a policy, that states that we need anti-malware systems, clearly defines responsibilities for users, and training and awareness for them.
Training & Awareness
Why training and awareness? As I mentioned, a virus must be triggered by a user, so one form of anti-malware is not actually systems or technology, but rather making our users aware of what malware is, and training them not to open those macro enabled excel files that a stranger sends them.
Prevention
Ideally, we want to prevent malware from infecting our systems.
Allow list
One method of doing so is Allow Lists (historically referred to as White Lists). The idea here is we create a list of programs that are allowed to run on the system, an Allow List, and any software that is not on the list, like malware, is not allowed to be installed and executed on the system. Allow Lists are a very good way of locking down a system.
Network Segmentation
Network segmentation is about separating our network into segments and then controlling the flow of traffic between segments potentially preventing the spread of malware like worms.
Detection
Now in the less than ideal situation that we haven’t prevented malware from getting on a system, let’s talk about how we can detect malware.
Signature Based Scanners
The type of malware scanner most commonly used to detect malware are signature-based scanners. Signatures define unique patterns for a piece of malware. Anti-malware vendors are constantly looking for the latest malware and whenever they discover something new, they write a new signature to identify the malware and then when their customers update their scanner they will download the latest and greatest signatures. Signature based scanners are fast and efficient which is why they are so pervasively used, however, they have a significant weakness, they can only detect what they have signatures for, which means they cannot detect zero-day malware.
Heuristic Scanners
That is why we also have Heuristic Scanners. Heuristic Scanners do not use signatures. Rather they evaluate a piece of software to try to determine if it is malicious. They do this in a couple of different ways: static heuristic analysis is where the static source code is analyzed, and dynamic heuristics is where a program is run in a sandbox environment and monitored to see if it does anything suspicious.
Heuristic Scanners are very susceptible to false positives, but they have the very big advantage of potentially being able to identify zero-day malware.
Activity Monitors
Activity monitors look at running processes on a system – running programs. Activity monitors are very much a last line of defense as the malware will need to have installed itself and be currently running for an activity monitor to detect it. But, Defense depth – it may be a good idea to have an activity monitor.
Change Detection
And change detection. A lot of malware will make changes to certain system files, like configuration files. Change detection is about monitoring key system files for changes. So we hash the files we want to monitor for changes, and then re-hash the files periodically to check to see if the hash values differ – if they do it means a change has been made to the file and we might have malware on our system.
Continuous Updates
Finally, as I mentioned, most anti-malware solutions are signature based, which means that it is critically important that we constantly, continuously, update our scanners with the latest signatures so that we can detect the latest malware.

And that is an overview of Malware within Domain 7, covering the most critical concepts you need to know for the exam.
Learn the terminology you need to know for the exam - like all these concise definitions of malware - quickly and efficiently with our currently free app.
Links to download our free app are in the description below.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
