Evaluation Criteria MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to Evaluation Criteria in Domain 3, to understand how they interrelate, and to guide your studies.
This is the second of 9 videos for domain 3. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass.
As part of building a secure environment, every organization is going to need to acquire various products from vendors (firewalls, routers, intrusion detection systems, etc.). As security professionals, advising the acquisition process for such products, we must ensure the products are well designed and provide the security functionality we require.
But here we encounter a challenge. If we ask, say, a firewall vendor: hey how secure is your product? What are they going to say?

They’re going to say: “my firewall is the greatest thing since sliced bread. Grown men literally weep in awe of my products shining brilliance.”
Should we, as security professionals, believe this marketing malarkey? Absolutely not.
So how, then, do we compare different vendor’s products and trust the claims about a product's functionality?
Evaluation Criteria
Evaluation criteria.
Evaluation Criteria are independent objective evaluation systems for products.
Here’s how this works: a vendor will create a product, then the vendor will pay an independent testing lab to evaluate their product using one of the Evaluation Criteria we are going to talk about in a moment. The independent lab will test the product, give it a rating, and produce a report that the vendor can then hand out to their customers. And customers are going to trust the rating in the report because it was provided by an independent testing lab, not the vendor.
Certification
There are two major steps involved with Evaluation Criteria. The first is certification, and the second is Accreditation. We’ll start with certification, which is the comprehensive technical analysis of a solution or a product to ensure it meets our needs. In other words, the certification step is where the independent testing lab evaluates a product and gives it a rating.
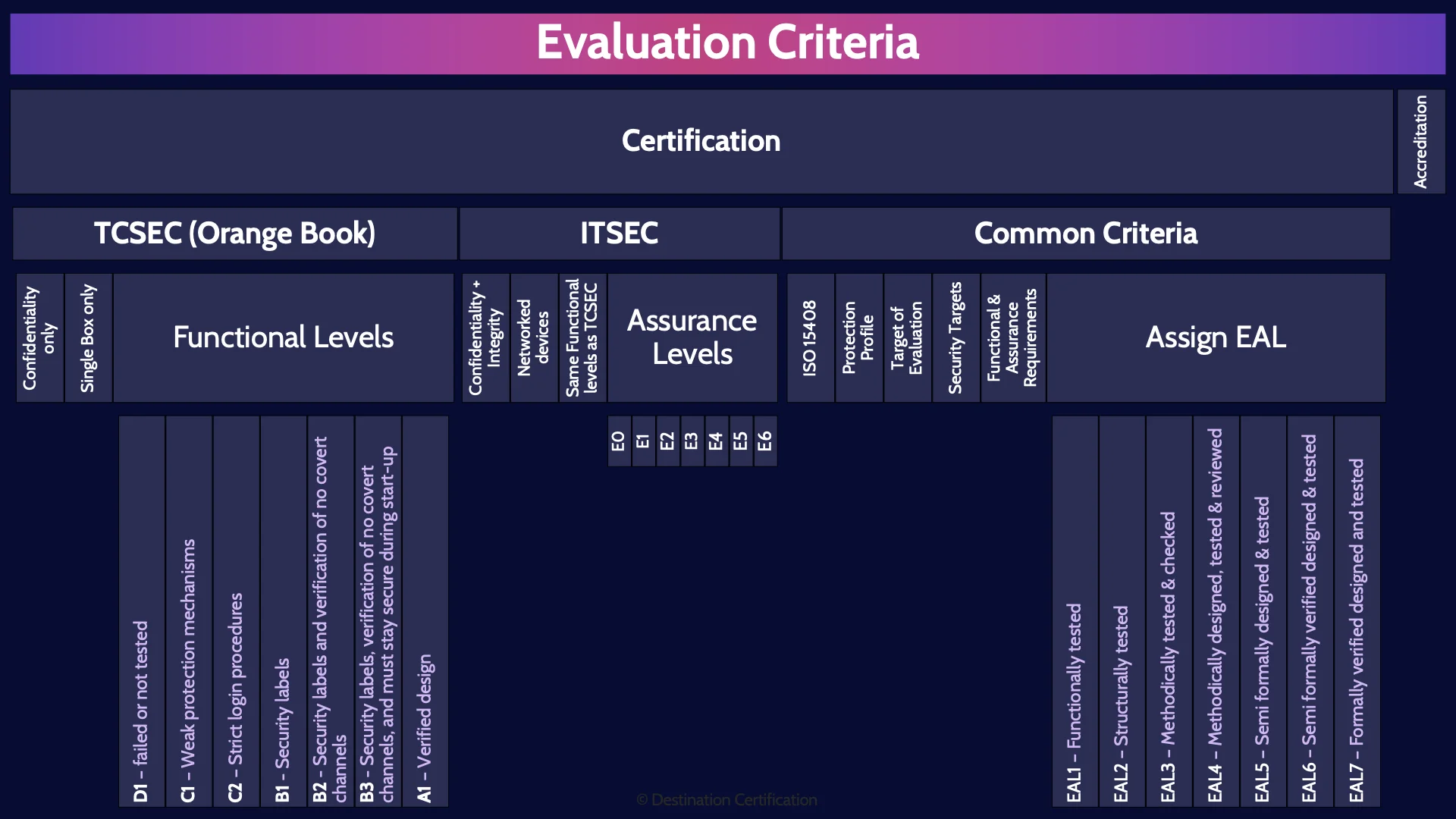
TCSEC (Orange Book)

Let’s look at the different evaluation criteria systems that have been developed starting with one of the oldest. TCSEC, the Trusted Computer System Evaluation Criteria, otherwise known as the Orange Book… because the book cover for TCSEC was pink..
It’s orange.
Confidentiality only
TCSEC was only designed to evaluate the confidentiality that a system provides.
Single Box only
And TCSEC was only designed to evaluate a product that is not connected to a network. Single stand-alone boxes only.
Functional Levels
TCSEC defines 7 functional levels that a product could be rated based on the evaluation.
D1 – failed or not tested
Starting with the lowest possible rating which is D1, which means the product failed or wasn’t tested. Not a reassuring rating for a product.
C1 – Weak protection mechanisms
Next up is C1 which means the product provides weak protection mechanisms.
C2 – Strict login procedures
Next is C2, and each level builds on the previous, so C2 adds that products provide strict login procedures. C2 is the most common rating for products.
B1 - Security labels
B1 is where labeling becomes a requirement for products. Remember that. B1 labeling.
B2 - Security labels and verification of no covert channels
B2 means products provide security labels and verification of no covert channels.
B3 - Security labels, verification of no covert channels, and must stay secure during start-up
B3 means products provide security labels, verification of no covert channels, and must stay secure during start-up
A1 – Verified design
And finally the highest possible functional rating that a product can achieve is A1 – verified design. So secure, it is virtually unusable.
ITSEC
ITSEC, the Information Technology Security Evaluation Criteria, is a big improvement on the older TCSEC.
Confidentiality + Integrity
ITSEC can be used to evaluate not just the confidentiality that a product provides, and but also the integrity
Networked devices
ITSEC can be used to evaluate devices that are connected to a network
Same Functional levels as TCSEC
And ITSEC uses exactly the same functional levels as TCSEC that we just went through, D1, C1, C2, B1, etc…
Assurance Levels
The final major improvement that ITSEC provides is that it can be used to evaluate not just the functionality that a product provides, but also the assurance. Remember functional means what a system should do, and assurance means how do we verify / test that it is working correctly. So ITSEC can be used to evaluate the level of assurance that a product can provide. These levels are referred to as the Evaluation levels. Or E Levels, and there are seven of them
E0
E0
E1
And ITSEC uses exactly the same functional levels as TCSEC that we just went through, D1, C1, C2, B1, etc…
E2
And ITSEC uses exactly the same functional levels as TCSEC that we just went through, D1, C1, C2, B1, etc…
E3
to
E4
E5
E6
E6. I don’t think you need to memorize the specifics of these levels
Common Criteria
Okay, now the latest and greatest evaluation criteria: The Common Criteria for Information Technology Security Evaluation – everyone just calls it Common Criteria.
ISO 15408
Common Criteria has been adopted as an international standard. Specifically, ISO 15408
Protection Profile
The Common Criteria evaluation process begins with defining a Protection Profile (PP) which identifies the security requirements for a class of security devices (e.g. firewalls, smart cards, etc.)
Target of Evaluation
The Target of Evaluation (TOE), defines the specific product or system that will be evaluated. This is the specific product provided by the vendor to be evaluated. For example, a Cisco ASA 5515-X Firewall could be the TOE. The Target of Evaluation.
Security Targets
The Security Target (ST) is a document prepared by the product vendor which defines the specific functional and assurance security properties and capabilities that the vendor claims are built into the Target of Evaluation.
Functional & Assurance Requirements
The independent testing lab will then test the functional and assurance aspects of the Target of Evaluation
Assign EAL
And the end result will be an EAL rating. An Evaluation Assurance Level rating.
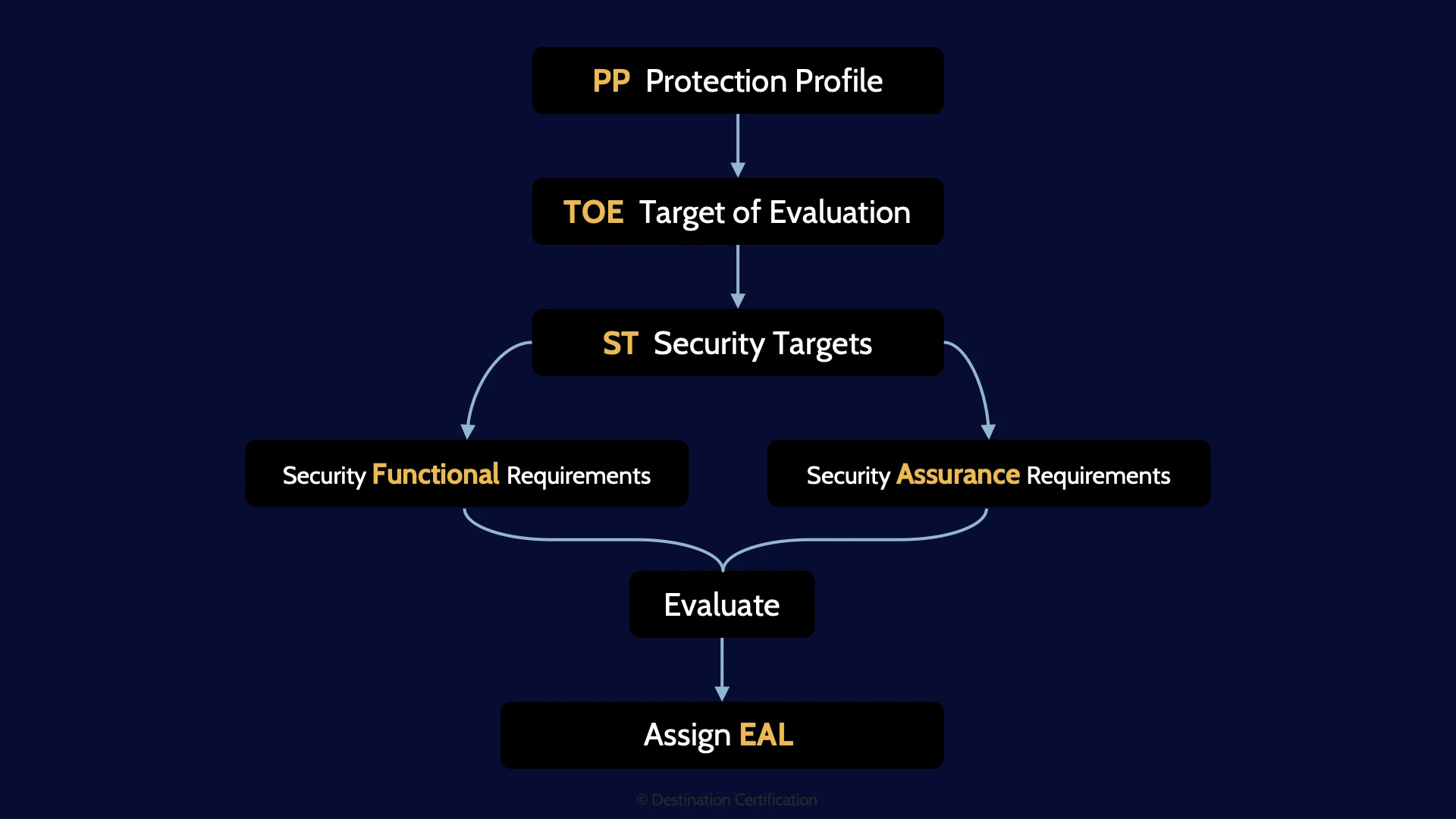
Before we get into the EAL ratings, here is a visual summary of the common criteria process.
Now onto the EAL ratings, of which there are 7.
EAL1 – Functionally tested
Starting from the lowest rating EAL1 – which means only the functionality of the product was tested
EAL2 – Structurally tested
EAL2 – means only the structure of a product was tested
EAL3 – Methodically tested & checked
EAL3 - Methodically tested & checked
EAL4 – Methodically designed, tested & reviewed
You will see that these levels build on each other
EAL4 - Methodically designed, tested & reviewed
EAL5 – Semi formally designed & tested
EAL5 - Semi formally designed & tested
EAL6 – Semi formally verified designed & tested
EAL6 - Semi formally verified designed & tested
EAL7 – Formally verified designed and tested
And the best possible rating:
EAL7 - Formally verified designed & tested
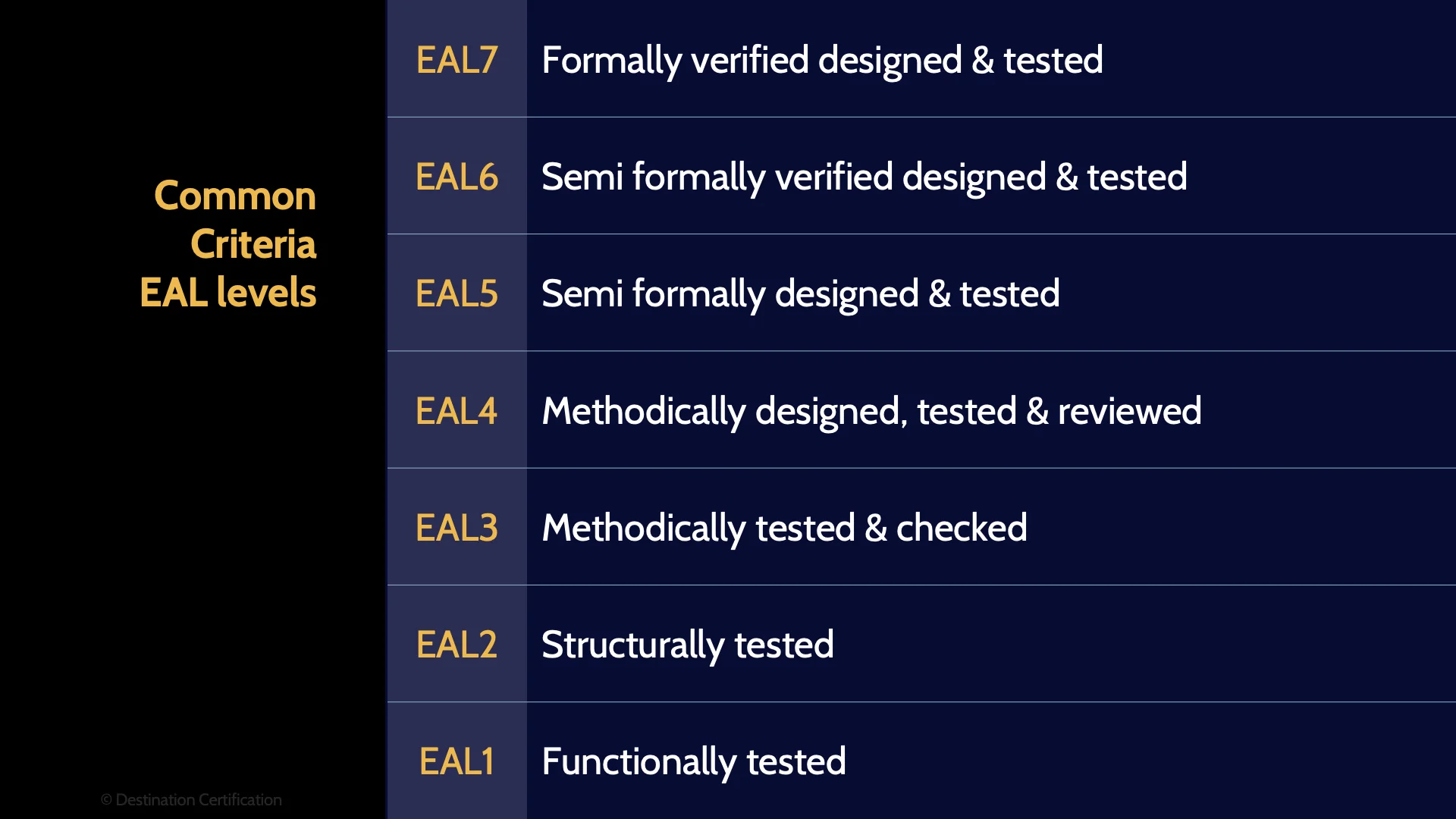
I would highly recommend that you memorize these EAL levels and the order of them
Accreditation
And now last, but certainly not least the final major piece of Evaluation Criteria: Accreditation.
As I discussed at the beginning, the whole point of evaluation criteria is to help an organization evaluate and compare different products and choose the best solution for their organization.
The final step in selecting a product is management’s approval and sign off. This is accreditation: official management signoff for a set period-of-time to purchase and deploy a product in the organization.

And that is an overview of Evaluation Criteria within Domain 3, covering the most critical concepts you need to know for the exam.
Are you looking for the easiest way to get your CISSP certification? You should check out our CISSP MasterClass at: destcert.com/CISSP
Link in the description below as well.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
