Physical Security MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to physical security in Domain 3, to understand how they interrelate, and to guide your studies.
This is the final ninth of 9 videos for domain 3. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass.
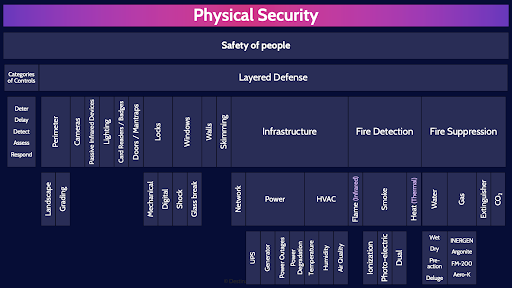
Physical Security
Physical security is critical in achieving confidentiality, integrity and availability.
There is an expression I like: if you can touch the box, you own the box.
In other words, if an attacker can gain physical access to a device like a firewall or a server they can easily gain control of the device. This is because our equipment has all sorts of bypass controls built in, like factory reset buttons.
We need to carefully control who can gain access to our facilities, specific rooms, and certain equipment.
Physical security is also critical in achieving integrity and availability as physical security controls like UPSs & generators provide a good clean supply of power / electricity,
HVAC systems provide cooling air at the right temperature and humidity
and fire detection and suppression systems help to ensure our facilities don’t burn to the ground.
All very important things in achieving confidentiality, integrity and availability.
Safety of people
There is one overarching / primary goal of physical security, and that is… safety of people. People are the most valuable, the most important asset of any organization and physical security controls must prioritize the safety of people above all else.
Categories of Controls
There are five categories of controls used in physical security.
Deter Delay Detect Assess Respond
Deter, delay, detect, assess and respond.
· Deterrent Controls discourage things like trespassing, property damage, theft and intrusion through signage and the environmental design of a building and the land around it
· Delay Controls delay a risk from occurring, for example locks delay an attacker from gaining unauthorized access
· Detective Controls detect if a risk has occurred. CCTV cameras are a perfect example of a detective control
· Assess Controls are used to determine the method of attack and the target
· And finally, Respond Controls take appropriate actions to remediate the risk
Layered Defense
When we are implementing the aforementioned controls, we never want to implement a control in isolation. If there is only one control protecting an asset and that control fails then… bad stuff will happen.
This is why we want to have multiple layers of controls, and at each layer have a combination of preventive, detective and corrective controls or in physical security terms deterrent, detective and assess & respond controls. The is the concept of defense in depth.
Perimeter
The first layer of defense protecting a facility is often an outside perimeter like a fence. Another perimeter will be the exterior walls of the building.
What is the best way to secure the perimeter? Minimize the number of entrances and exits, the number of doors.
Landscape
Landscaping refers to the foliage around a building, the trees and plants. You want to ensure the foliage is maintained to provide clear sight lines for cameras and that a would-be attacker can’t just climb up a tree and into the building.
Grading
Grading refers to how the land is sloped around a building. You want the ground to slope down and away from the building so that in the event of a flood you're nice and dry on an island and not at the bottom of a lake.
Cameras
CCTV - Closed Circuit Television – Camera systems are an important part of physical security as a deterrent, detective control, and can also be used for monitoring and auditing. Cameras are primarily detective controls.
Passive Infrared Devices
Passive Infrared Devices are motion sensors. They are essentially really low-resolution cameras that detect infrared light – the heat that is emitted by objects in its field of view. If you as a homeothermic mammal walk into a room then the amount of infrared light in the room is going to increase and thus your movement will be detected.
These devices must automatically recalibrate themselves if the ambient air temperature changes.
Lighting
Lighting is an important physical security control. A well-lit building helps deter crime and good lightning is important for the safety of people.
Card Readers / Badges
Card readers are electronic systems used to control who is authorized to pass through a door into the building or into different rooms within the building. There are two major types of card reader systems. Contact & Contactless. In contact systems an employee must swipe their card through the reader for older magnetic readers. In newer contactless systems an employee only needs to hold their card near the RFID (Radio Frequency ID) systems.
Badges are simply an employee name and photo on a card.
Doors / Mantraps
Doors are the primary way that we control who can gain access to a building and specific parts of the building.
A social engineering attack on doors is tailgating or piggybacking – an intruder follows an authorized person through a door after they have unlocked it. This is a super common and successful attack that can be prevented by using specialized doors: mantraps or turnstiles.
Mantraps are two doors, one after another. You must unlock the first door, enter a small space, close the first door behind you and only then can you unlock the second door. Mantraps prevent someone from tailgating or piggybacking.
Locks
Locks are a perfect example of a DELAY control in physical security. It is just a matter of time before an attacker picks, forces, or breaks a lock and gains entry – checkout the lock picking lawyer if you don’t believe me. Because locks are DELAY controls they should never be implemented in isolation. Remember layered security or defense in depth.
There are loads of different types of locks out there.
Mechanical
A couple of broad categories are mechanical locks - for example keyed locks, mechanical combination locks, and magnetic locks.
Digital
And a second broad category are electronic locks - proximity or RFID locks., electronic combination locks, and biometric locks.
One of the most important factors that determines the security of combination locks is the complexity of the combination.
Windows
We love the natural light that streams in through windows but windows are often the weak link in the perimeter of a building. There are various types of glass that a window can be made out of (plate, tempered, laminated, wired & polycarbonate to name a few) but I don’t suggest you memorize the different types of glass.
Instead understand a couple of types of sensors that can be used to detect if the glass in a window has been broken.
Shock
Shock sensors are attached directly to a pane of glass and they are designed to detect the small shockwave that is generated when a window breaks.
Glass break
Timing attacks measure how long certain operations take.
Walls
Walls are also obviously rather critical to physical security. It is tough to secure a building that doesn’t have exterior and interior walls.
Skimming
I’ve thrown skimming in here for lack of a better place to put it. Skimming is where crooks use an electronic device to steal card information from a valid transaction. So, for instance, install a little electronic device on a bank machine which records your debit card number or on a Point of Sale machine to skim your credit card details when you pay for something or an attacker stands near a secure door and wirelessly records the RFID communications from your employee card.
Infrastructure
Lets now talk about the three major infrastructure services that are critical to the operation of a facility: Network, Power, and HVAC.
Network
Network – a reliable connection to the largest distributed network in the world – the internet and/or to other locations of the organization.
Power
It’s tough to find equipment nowadays that doesn’t require electricity and harder yet to imagine a business that could continue to function without electronic systems of some sort. Accordingly, security is very concerned with providing a consistent supply of clean power.
And by clean power I don’t mean from renewable sources like wind or solar – which is an awesome source of power.
But rather, by clean power, I mean Alternating Current (AC) power that oscillates at a perfect 60 Hz with no noise or distortion in the line – it’s a perfect sine wave.
UPS
A couple of important devices used to provide a consistent supply of clean power. UPS & Generators.
UPS – Uninterruptible Power Supplies, are basically giant batteries that provide instantaneous but short term power. Until…
Generator
The generator has time to start up and come online. Generators are typically large diesel engines connected to an alternator and generators can provide long-term backup power – for hours or even days depending on how much fuel is onsite.
Power Outages
There are various types of power outages that physical security is concerned with: A Blackout is no power for a long period of time. And Faults are a momentary loss of power.
Power Degradation
Power degradation means there is too little or too much power. Brownouts are an intentional reduction of voltage by the utility company. Sags & Dips are a short period of low voltage.
And Surges are a momentary spike of too much voltage. Think lightning strike.
HVAC
HVAC stands for Heating Ventilation and Air Conditioning. These are the systems that provide air to a building at the correct temperature & humidity and filter the air.
Temperature
The primary reason for bringing cool air into a data center is to cool the equipment and ensure the equipment is operating within a desired temperature range.
Humidity
HVAC systems will also provide air at the right humidity. Too dry and you get static electricity, too humid and you get condensation. Both are bad.
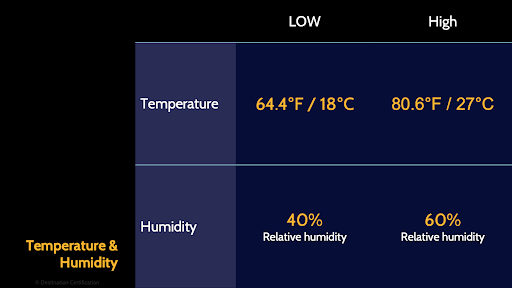
This, here is the ideal temperature and humidity ranges as defined by ASHRAE - the The American Society of Heating, Refrigerating and Air-Conditioning Engineers. The HVAC systems in most office buildings, data centers, etc. are built to provide air within this these ideal ranges:
Temperature between 18 to 27 degrees celsius - and yes, if you’re in the US and prefer Freedomhieght you can memorize those temperatures instead. Any exam questions will list both celsius and freedomheight.
Ideal relative humidity between 40 to 60 percent.
Air Quality
The final major function of HVAC systems is to filter the air to remove dust and other contaminants. In a datacenter the air is being sucked into and through servers and other equipment and if there were contaminants in the air they could clog up the equipment causing shorts or for the equipment to overheat and fail.
Related to air quality, you should know a term: positive pressurization. The idea is that this nice clean filtered air will be blown into the datacenter at slightly above ambient pressure, thus positively pressurizing the datacenter. Why would we want to do this? If there are any cracks in the walls, or someone opens a door, then nice clean air is being forced out preventing any dirty air and contaminants from infiltrating.
Fire Detection
Ok, now for a favorite topic of mine. Fire!
Fire is a significant risk. And like any other risk we need to put controls in place to mitigate the risk of fire. Whenever we implement controls, we want a combination of preventative, detective and corrective controls.
What’s the best way to prevent a fire? Limit or eliminate any combustible materials
You can never entirely prevent the risk of fire though, so if a fire does occur you want to detect it as quickly as possible – so we’ll talk about different fire detection methods.
And as soon as you have detected a fire you want to correct it as quickly as possible, so we’ll finish this MindMap by talking about different fire suppression systems.
Alright fire detection systems. There are three major types: flame detectors, smoke detectors and heat detectors.
Flame (Infrared)
Flame detectors detect the Infrared and Ultraviolet light created by flames. Flame detectors are essentially video cameras that you point at something you are concerned might start on fire.
Smoke
There’s always some before a fire, and one of the best ways of detecting a fire as early as possible is using a smoke detector. There are two major types of smoke detectors, ionization and photo-electric.
Ionization
Ionization detectors respond more quickly to what are known as flaming or fast fires.
Photo-electric
Whereas Photo-electric, often referred to as optical detectors respond more quickly to smoldering fires.
Dual
Most good quality detectors these days are known as dual detectors; they combine ionization and photo-electric detectors into one device.
Heat (Thermal)
And finally heat detectors, often referred to as thermal detectors, or rate of rise detectors, are essentially temperature sensors that are monitoring for a rapid rise in temperature. If the temperature rapidly spikes you probably have a fire.
Which of these systems will detect a fire as early as possible? Remember there is always smoke before a fire, and the type of fire we are most concerned with is flaming or fast fires. So, pick ionization detectors.
Fire Suppression
Lets now talk about how we suppress a fire. There are two major types of systems: water-based, and gas-based.
Water-based systems are cheaper than gas-based systems, but water and expensive electrical equipment in a datacenter is a terrible combination.
So, gas-based fire suppression systems are cost justified in data centers.
Water
Water based systems are common in office buildings, hotels, and other spaces where some water is not going to destroy millions of dollars worth of equipment. There are four types of water-based systems you should know about.
Wet Dry Pre-action Deluge
Wet-pipe systems always have pressurized water in the pipes, just waiting to be released. Wet-pipe systems are the cheapest but have significant downsides: you can’t use them where the pipes might freeze, and because there is pressurized water in the pipes at all times you are inevitably going to get leaks.
Dry-pipe systems look identical to wet-pipe but the key difference is the pipes are dry. They are filled with a pressurized gas, and water only comes flooding into the dry pipes when needed.
There are also pre-action and deluge systems and both of course use water to put out a fire.
Gas
Gas based systems use various types of gas to put out the fire. Some gas-based systems displace the oxygen from a room. No oxygen equals no fire.
But also, no oxygen equals no human life so it is critical to have safety systems in place to allow people to exit the datacenter before the gas is released.
Another method some gas-based systems will use to suppress a fire is to interrupt the chemical exothermic process that is fire.
INERGEN Argonite FM-200 Aero-K
Here are the 4 major types of gasses you need to know about: INERGEN, Argonite, FM-200 and Aero-k.
All of these are gas-based fire suppression agents.
There is one gas I will point out that is very intentionally not listed here: Halon. That gas has traditionally been used in data centers, however, it has been banned globally as it destroys our ozone layer. So don’t pick Halon on the exam - it’s bad for the environment.
Extinguisher
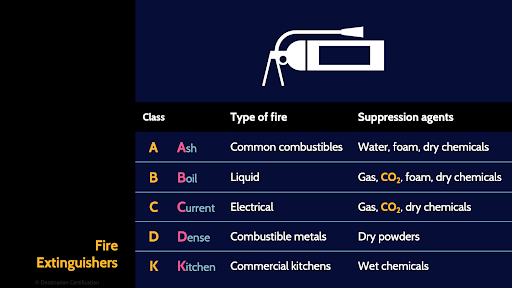
The final tool in your fire suppression arsenal is fire extinguishers. These red things you see all over the place hanging on the wall.
There are five different classes of fire extinguishers: A, B, C, D and K. Each class is meant to put out a different type of fire and will use different suppression agents.
There is only one class that I will highlight, and that is C. Class C fire extinguishers are designed to put out electrical fires – the type of fire you might have in a datacenter. And Class C extinguishers will often use CO2, good old carbon di-oxide as the suppression agent.
CO2
CO2 is an excellent fire suppression agent to use in data centers, because C02 is non-corrosive (it won’t damage the expensive equipment), it doesn’t leave a residue, doesn’t conduct electricity, and provided you don’t use too much, it’s safe for humans.

And that is an overview of Physical Security within Domain 3, covering the most critical concepts you need to know for the exam.
A common challenge when preparing for the CISSP exam is staying on track. There is a huge amount that you need to study before you’re ready for the exam. It’s tough to know exactly how much you need to study each day to be ready for the exam be a certain date. And it’s also tough to keep yourself accountable.
An awesome feature of our CISSP MasterClass is that we create your own personalized schedule for you. We tell you exactly what to study each day and ensure you’re on track and ready to confidently pass the CISSP exam.
You can find all the details on our CISSP MasterClass here at destcert.com/CISSP

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
