Databases MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcrip
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to databases in Domain 8, to understand how they interrelate, and to guide your studies.
This is the second of two videos for domain 8. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass.
Databases
Databases provide a means to store an organized collection of structured data in a table with nice neat rows and columns – making it easy to add, access, modify, and analyze the data.
Relational databases, which is what we’ll be discussing in this video, allow data in different tables to be related, connected, with data in other tables based on a relational model.
A Database Management System is the collection of components that allow the database to be controlled. To be used by people and processes.
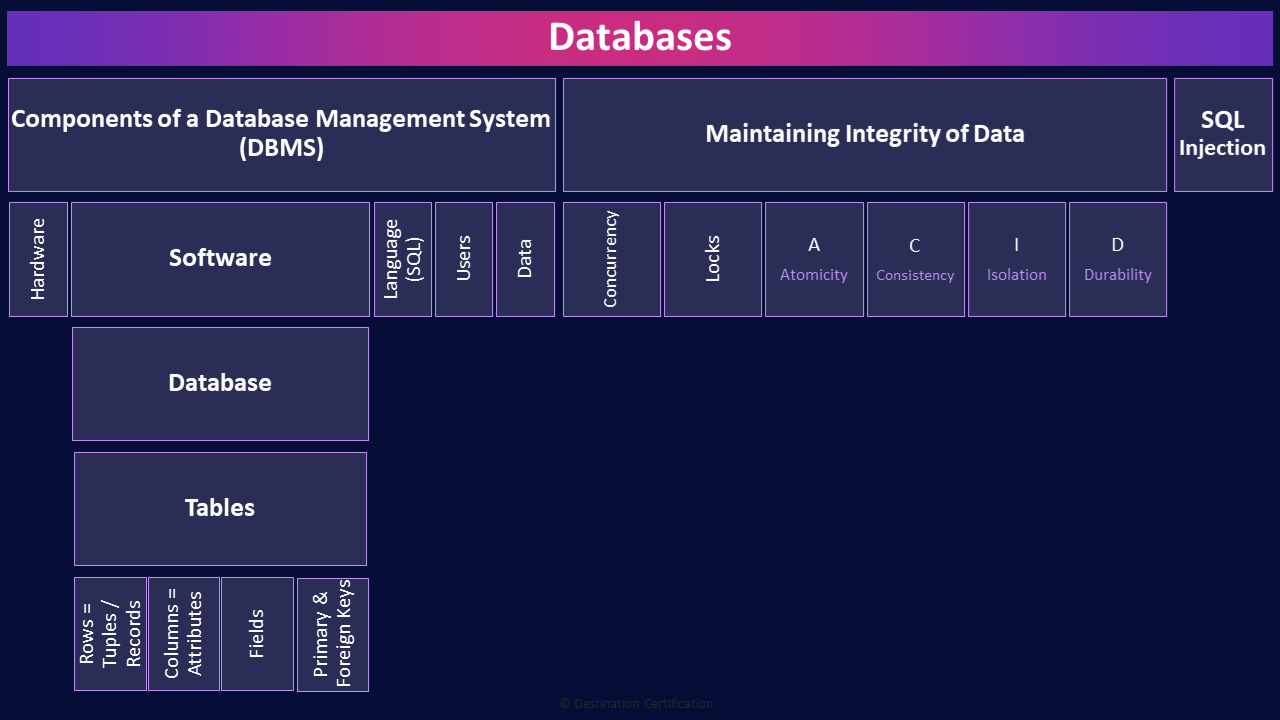
Components of a Database Management System (DBMS)
We’ll start by looking at the components of a Database Management System, and then we’ll get into the relational components of a database.
Hardware
The first component of a DMBS is hardware. The DBMS needs to run on a server that provides sufficient processing power and storage space.
Software
The next component is the software, we first need an operating system, and then DBMS software itself that will run on the operating system. Examples of Database Management Systems include MySQL, Oracle RDBMS, IBM DB2, Microsoft SQL Server, Amazon RDS, among many others.
Database
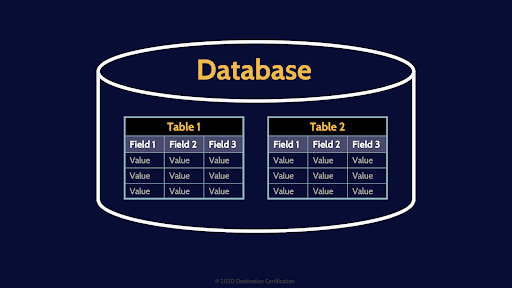
The DBMS software enables the control of the database. A database can contain 1 or more Tables
Tables
These tables contain rows and columns of data.
Rows = Tuples / Records
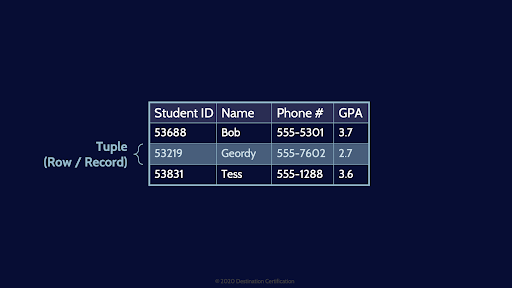
If you want to roll with the cool database kids you can refer to rows as Tuples or Records. I think I have demonstrated how uncool I am but uttering that last sentence.
Columns = Attributes
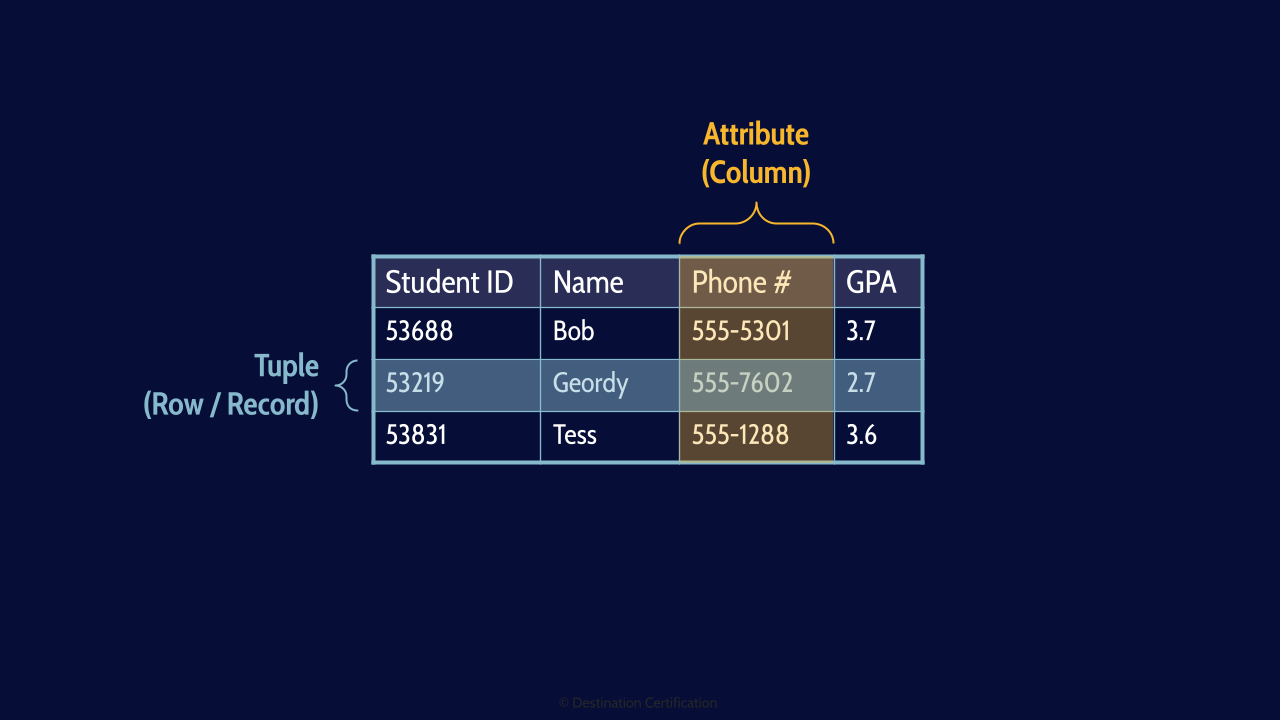
Columns can also be referred to as Attributes
Fields
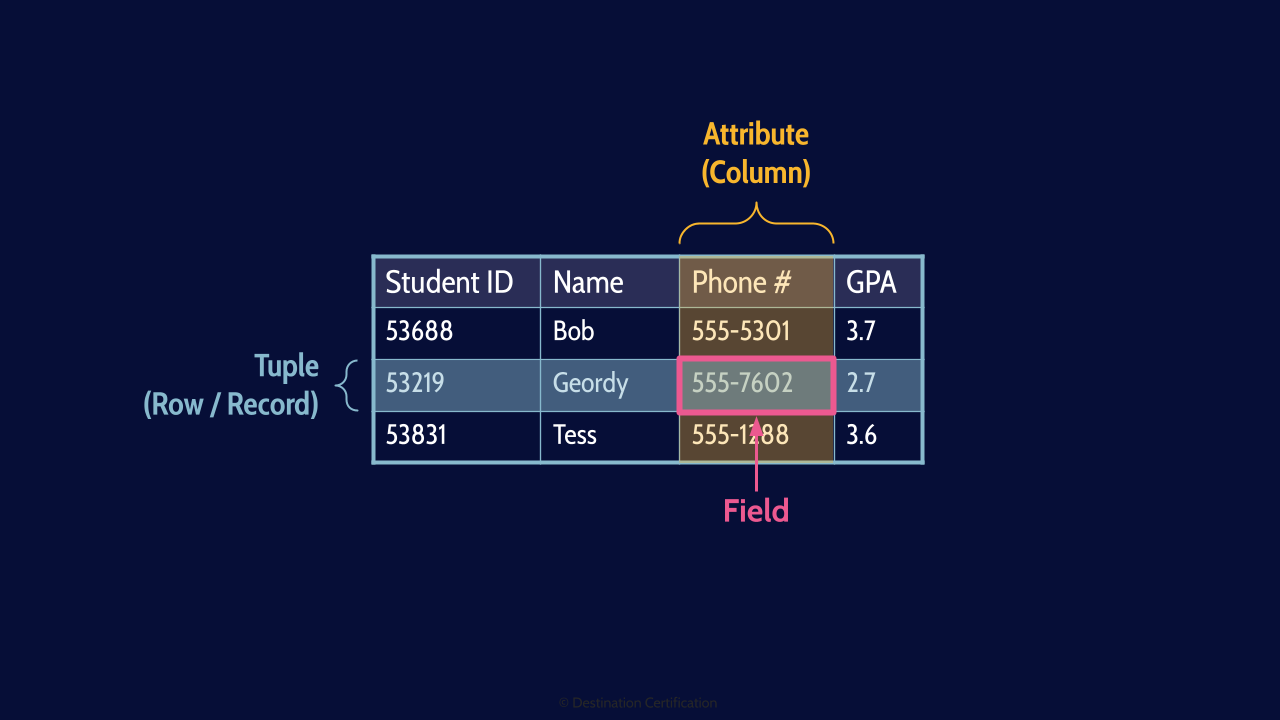
And the intersection of a Tuple and an Attribute is a Field. A cell of data in the table.
Primary & Foreign Keys
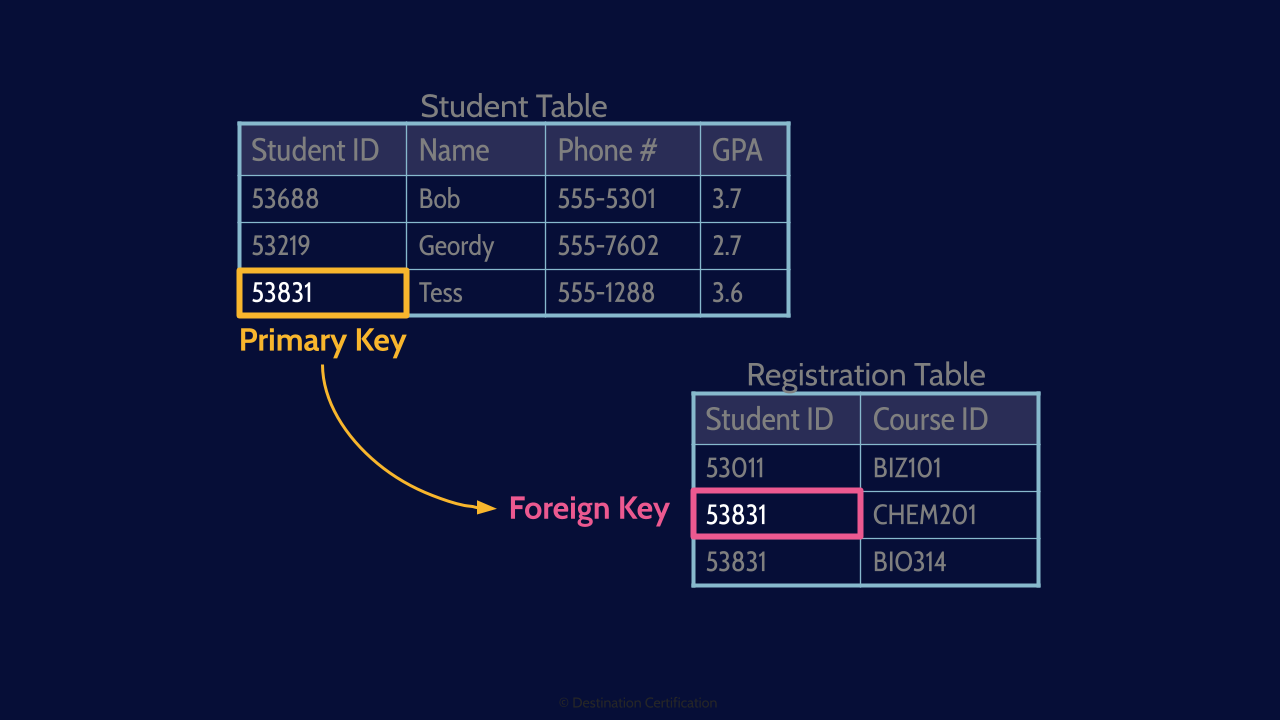
As I mentioned with a relational database, you can relate data in one table to data in another table. This is done through the use of Primary and Foreign Keys.
A Primary key is a unique identifier for a specific record or row of data. A Primary key for a person could be something like their Social Insurance Number, Passport Number, or in this case their Student ID.
A Foreign Key is how we link, how we form a relationship to another table. The foreign key is a column in a table whose values correspond to primary keys in another table. In this case we have a course registration table, and there is a row for each course that a student is registered in, and that row contains their student ID as the foreign key. We can therefore link which courses a student is registered in by using their student ID.
Language (SQL)
The language we use to communicate with, to control, our relational Database Management System, is known as Structured Query Language. SQL.
Users
User’s or processes can send SQL commands to the DBMS to store new data, modify data, delete data, and so forth
Data
And rather obviously, the final major component of our DBMS is all the data that we store in it.
Maintaining Integrity of Data
A database will be of little use to an organization if the data it contains is inaccurate. Thus, we must have controls in place to ensure the integrity of data.
Concurrency
In a modern, high-performance database, we typically allow multiple transactions to run concurrently, in parallel. A transaction is a unit of work, typically encapsulating several operations including reads, writes, acquiring locks, etc.
It makes it significantly more difficult to maintain the integrity of the data in a database when multiple users or processes are executing multiple transactions concurrently.
Locks
One of the major controls we use to Prevent data corruption when multiple transactions are running concurrently is: locks. A record (a tuple) can be locked meaning that only one user or process may update the record until the lock is released by either committing the update or rolling back.
A - Atomicity
To further ensure the integrity of the data, we should also enforce a standard set of properties, known as ACID, that guarantee database transactions are processed reliably.
The A in ACID is Atomicity which means that all changes being made as part of a transaction take affect or None.
C - Consistency
The C in ACID is Consistency which means updates to the database are consistent with the rules. The rules are enforced
I - Isolation
The I in ACID is for Isolation which means transactions are Invisible to other users until complete.
D - Durability
And the D in ACID is durability which means Completed transactions will not be Lost – they are durable.
SQL Injection
A major type of attack against databases, that you definitely need to understand for the exam, is SQL injection. An attacker can inject SQL code through a web application to control the database behind. Something that we as security professionals should always work to prevent. I talk about SQL injection attacks in detail in Domain 3, video 4. The link to that video is in the description below.

And that is an overview of Databases within Domain 8, covering the most critical concepts you need to know for the exam.
And this is also the final MindMap in the series.
My business Partner, John Berti, has been teaching CISSP classes for over 20 years. I’m nearing 10 years myself. We love helping folks like yourself learn and become better security professionals. Truly what drives us to continue teaching and spending so much time creating the best CISSP study materials is we find it incredibly personally rewarding to guide people to achieving thier CISSP certification. We get emails all the time from our students saying: I passed! Thank you!
We love these emails.
So I truly hope these MindMap videos have helped you in your studies and help you achieve your CISSP certification.
Thanks very much for watching! And all the best in your studies!

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
