Diving into CISSP Cryptography: A MindMap Guide
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to cryptography in Domain 3, to understand how they interrelate, and to guide your studies.
This is the sixth of 9 videos for domain 3. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass.

All right it's finally time for a seriously fun MindMap video on…. Cryptography!
No seriously, cryptography is super cool and fascinating. It's amazing the number of services and capabilities that cryptography enables that we use every single day and probably don’t even realize it.
Want to purchase something online and not have your credit card details and personal information stolen by some sketchy character on the internet: cryptography
Want to know if the update you just download for your iPhone actually came from Apple and that it wasn’t modified in transit: cryptography
Are you a criminal and you want to hide your communications from law enforcement: cryptography has you covered
Are you a large corporation that sells movies or music online and you want to protect your content with digital rights management and massively irritate your customers: cryptography can do that for you
Secure electronic voting, digitally signing documents, defensible data destruction in the cloud, crypto currencies, all of them… you guessed it, rely on cryptography.
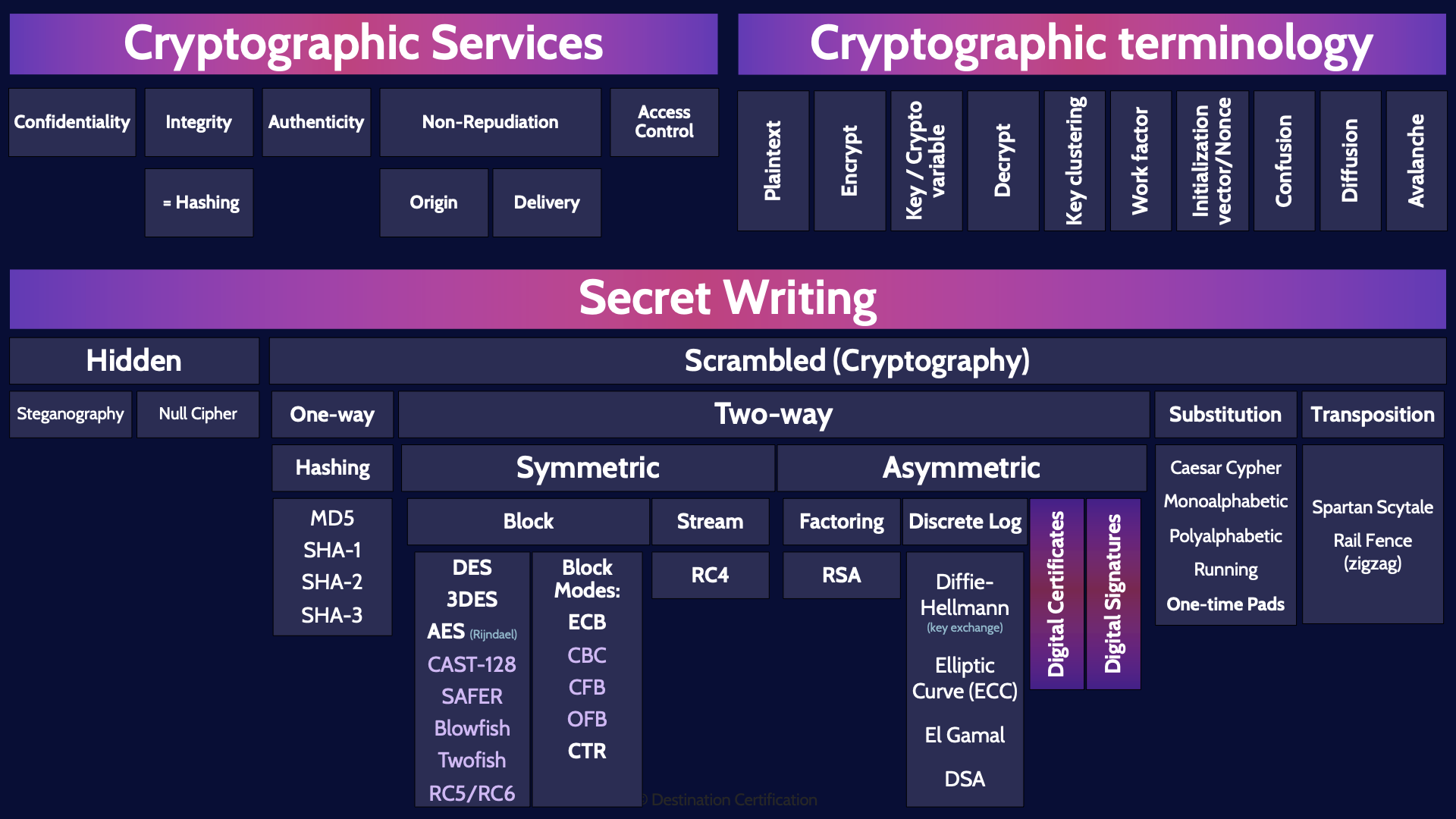
Cryptographic Services
So, let's begin our whirlwind tour of cryptography by talking about the 5 major services that cryptography provides
Confidentiality
First up confidentiality which allows us to make data available to only those that are authorized to view it – confidentiality helps us to prevent unauthorized disclosure of information
Integrity
Integrity ensures that information has not been manipulated or changed by unauthorized individuals. Integrity helps us to prevent unauthorized or unexpected changes to data
= Hashing
And to achieve integrity we use Hashing. So, equate those two in your mind – hashing = integrity | integrity = hashing
Authenticity
Authenticity means we can confirm who something came from, we can for instance verify that a message came from a particular sender
Non-Repudiation
Non-Repudiation prevents someone from denying prior actions. There are two flavors of non-repudiation
Origin
Non-repudiation of origin means the sender cannot deny that they sent a specific message – they cannot deny the exact message originated from them
Delivery
And Non-repudiation of delivery means the receiver cannot deny that they received a specific message
Access Control
And finally, cryptography enables a form of access control; by controlling who we give ciphertext to, and who we give the decryption key to, we can control who can decrypt and therefore access some data
Cryptographic terminology
Now let’s talk about some important cryptographic terminology
Plaintext
And we will start with plaintext or clear text, which is simply data that is readable by anyone. It is plaintext
Encrypt
To protect plaintext and provide confidentiality, we can encrypt the data. Encryption is the process of turning plaintext into ciphertext using a cryptographic algorithm and a crypto variable.
Key / Crypto variable
What then is a crypto variable – more commonly referred to as a key? A crypto variable is a string of bits that must be kept secret. This string of bits essentially programs the cryptographic algorithm – the key determines the specific steps that the cryptographic algorithm will perform to encrypt or decrypt - to transform plaintext into ciphertext (encryption) or ciphertext back into plaintext (decryption)
Decrypt
And that then is the definition of decryption: turning ciphertext back into plaintext using a cryptographic algorithm and a key
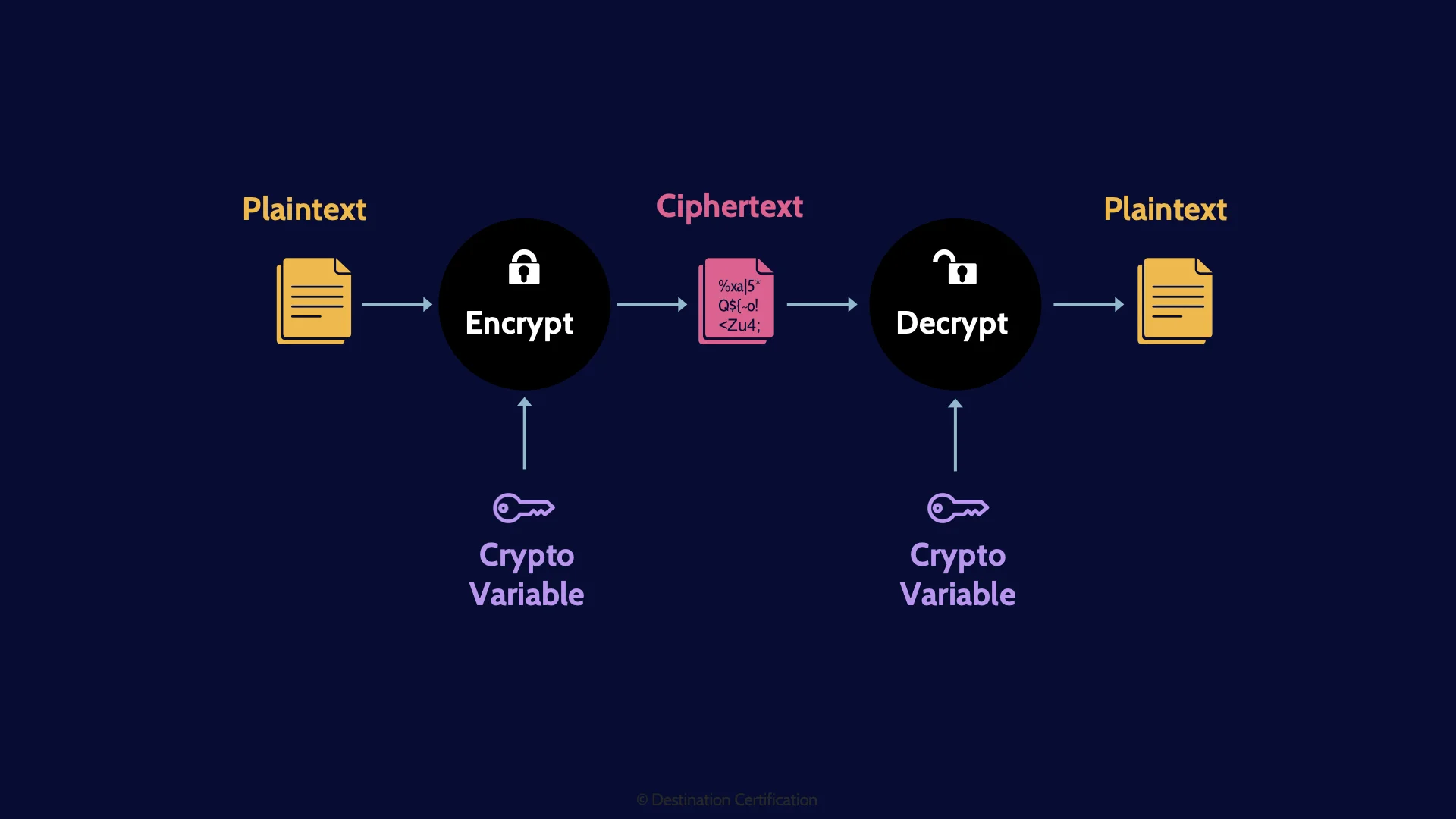
And here is a diagram showing the terminology we just discussed
Key clustering
Key clustering is where two different keys generate the same ciphertext from the same plaintext – this is something that we definitely want to avoid and good cryptographic algorithms are designed to minimize or ideally eliminate key clustering. Key clustering is bad because if two keys will decrypt some cypher text, that suddenly makes it twice as easy to try to perform a brute force attack
Work factor
The work factor is an estimated amount of time or effort required by an attacker to break a cryptosystem. The higher the work factor the more secure the cryptosystem.
Initialization vector / Nonce
An Initialization vector or a Nonce is a random number that is used along with the key and fed into a cryptographic algorithm when encrypting some plain text. IVs should only be used once in any session and are meant to help prevent patterns in the ciphertext that is generated. You can feed the same plaintext into a cryptographic algorithm and use the same key, and so long as you use a different IV, then it avoids producing the same ciphertext and thus avoids patterns.
Confusion
Good cryptographic algorithms should demonstrate a couple of properties, the first is confusion which is focused on hiding the relationship between the key and the resultant ciphertext. The confusion property means that if one bit of the key is changed, then about half of the bits in the ciphertext should change.
Diffusion
Diffusion is the same idea but focused on the plaintext. If a single bit of the plaintext is changed, then about half of the bits in the ciphertext should change. The confusion property is all about hiding the relationship between plain text and the ciphertext.
Avalanche
To determine the security of an algorithm, we can look at the avalanche effect. The avalanche effect looks at the degree of confusion and diffusion that an algorithm provides. The ideal case is that a single bit change to either the key (confusion) or the plaintext (diffusion) will result in at least a 50% change in the ciphertext.
Secret Writing
Okay now that we have some basic understanding of the services that cryptography can provide and some terminology under our belts let's get into how we can write secrets and hide our messages
Hidden
The first two methods we can use simply hide plaintext so that it cannot be easily seen or recognized and thus cannot be easily read.
Steganography
Steganography is the technique of hiding secret data within an ordinary, non-secret, file to avoid detection. For example, plaintext is hidden within a picture file, like a JPEG image
Null Cipher
A null cipher is where a secret message is hidden in plain sight by mixing the characters of the secret message with non-ciphertext (plaintext). For example, the secret message could be the first letter of each word in a paragraph.

Here is an example of a simple and rather politically charged Null Cipher - this example is getting a bit old, but I think it’s still pretty relevant and it amuses me. Let me know in the comments if you see the message hidden in this resignation letter.
Scrambled (Cryptography)
Okay now let’s move on to using machines and or algorithms which encrypt plaintext and turn it into ciphertext.
One-way
There are two ways that we can go about scrambling the letters and turning plaintext in cipher text. One-way encryption and two-way encryption. One-way encryption means that we turn plaintext into ciphertext, but then we cannot go back in the other direction. We can’t determine what the plaintext was from the ciphertext. Why would we ever want to do such a thing? We use one-way encryption for integrity.
Hashing
And we typically call this hashing. Hashing uses one-way mathematical functions which transform an arbitrary length input to a fixed length output – a fixed length message digest. Hashing algorithms need to be deterministic which means the same input will always result in the same output, the same digest – this is how we use hashing for integrity. If you hash the same file over and over again you will always get the same message digest. But if even a single bit in a massive file is changed, then the message digest will be completely different. By hashing a file at different times and comparing the hash values, you can easily see if a file has changed – integrity.
MD5, SHA-1, SHA-2, SHA-3
Hashing algorithms that you should be able to recognize as hashing algorithms include: MD5, SHA-1, SHA-2 and SHA-3
Two-way
Now let’s talk about two-way encryption which means we can encrypt some plaintext with a key turning it into ciphertext and then as long as we have the right key we can decrypt the cipher text and turn it back into plaintext. We can encrypt and then later decrypt – we can go in both directions. Two-way.
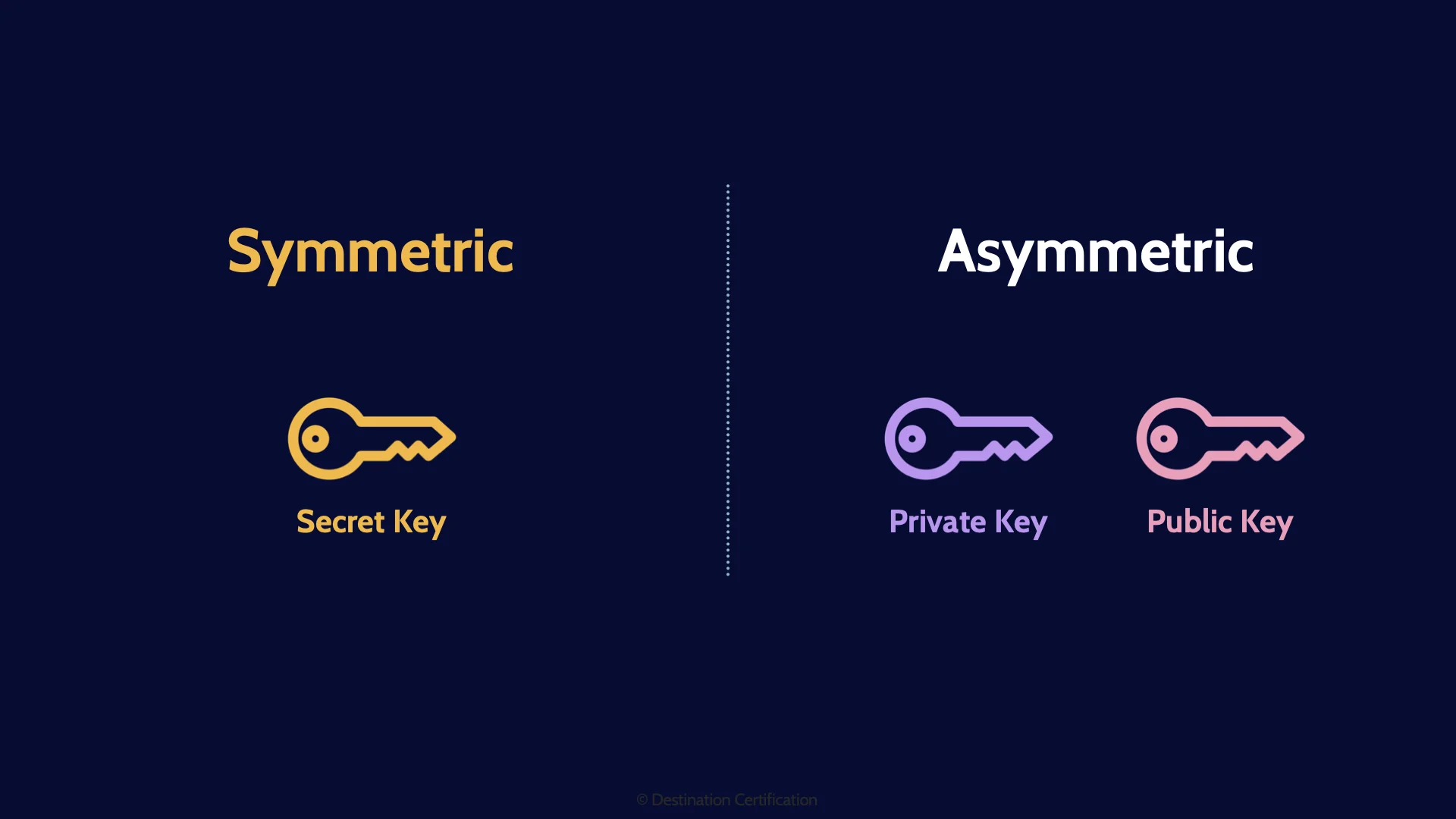
There are two major types of algorithms that we can use to perform two-way encryption: Symmetric algorithms and asymmetric algorithms. The major difference between the two is the number of keys needed to encrypt and decrypt. Symmetric algorithms use just one key to encrypt and the same key to decrypt. Asymmetric algorithms use a key-pair. Two keys. One key to encrypt and the other to decrypt – more on asymmetric in a bit.
Symmetric
Symmetric algorithms can be orders of magnitude faster than asymmetric algorithms. So, whenever you need to encrypt lots of data, and encrypt quickly and efficiently you need to use symmetric algorithms.

So symmetric algorithms are relatively very fast, efficient, and strong, but they have a couple of huge downsides: key distribution and scalability.
We’ll start with key distribution: Symmetric cryptography uses the same key to encrypt and the same key to decrypt, which means that if you want to send some data securely you need to encrypt it and send that ciphertext to someone and the key they need to decrypt it. I think you can see the problem here. Anyone could intercept the message and get the ciphertext and the key necessary to decrypt it.
To solve this key distribution problem, you could send the key out-of-band which is often not convenient or efficient – or you can use hybrid cryptography which we’ll talk about when we get to asymmetric cryptography.
The other problem is scalability. If you want to talk to one other person securely you need just one key. Two other people, you need 3 keys. 3 other people: 6 keys. 4 other people: 10 keys. The formula is N*N-1/2 and the problem is the number of keys you need grows exponentially. At only 1000 other people you need over half a million keys.

Delving deeper into symmetric algorithms. There are two major types of symmetric algorithms: block ciphers and stream ciphers.
Block
Block ciphers encrypt or decrypt blocks of data once. 16 bits of data, 32, 64 or 128 bit blocks.
DES 3DES AES (Rijndael) CAST-128 SAFER Blowfish Twofish RC5/RC6
Here are the major symmetric block ciphers that you need to know about. And for the top three: DES, Triple DES and AES you need to know some specifics
DES, the Data Encryption Standard, uses 56-bit keys, and 64-bit blocks, and does 16 rounds of substitution and transposition. A 56-bit key is nowhere near good enough anymore as 56-bit keys can be easily brute forced. So, DES should not be used.
Triple DES is using the DES algorithms 3 times and essentially uses 3 56-bit keys (although there are various ways triple DES can be configured which is beyond the scope of the exam). This gives triple DES a key length of 168 bits. 3 x 56. However, due to an attack known as the meet-in-the-middle attack, the effective key length of DES is only 112-bits.
When the US government saw that DES was becoming obsolete, they ran a competition to find a replacement and the winner was an algorithm called Rijndael. Rijndael was subsequently renamed to AES, the Advanced Encryption Standard. AES is an excellent and pervasively used encryption algorithm. It has a variable key length which can be: 128 bits, 192 or 256 bits. And it uses 128-bit blocks.
You should be able to recognize the rest of these algorithms as symmetric block ciphers: CAST-128, SAFER, Blowfish, Twofish, RC5 and RC6
Block Modes: ECB CBC CBC CFB OFB CTR
All those algorithms, including DES & AES, are block ciphers and there are different block modes. Different ways of encrypting blocks of plaintext or decrypting blocks of ciphertext. The various block modes have advantages and disadvantages.
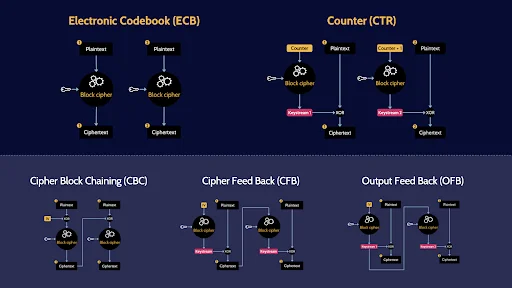
There are two block modes that you need to know some specifics about for the exam. ECB and CTR.
ECB, Electronic Codebook is the LEAST secure of the block modes because it does not use an initialization vector. It is also the fastest because of this. Therefore, ECB Should only be used for short bits of random text that do not repeat.
CTR, Counter mode, is considered the best balance of speed and security. It’s not the most secure and it’s slower than ECB, but is the best compromise of speed and security.
The other three modes have a big advantage over ECB, they all use an initialization vector, so they are all much more secure than ECB.

Taking a step back we talked about how there are two major types of symmetric algorithms: block ciphers and stream ciphers. We’ll now talk about stream ciphers.
Stream
In stream ciphers, a single bit of plaintext is combined with a single bit from a pseudorandom cipher digit stream (a keystream) using exclusive OR (XOR) math to produce a single bit of ciphertext.
That’s a mouthful.
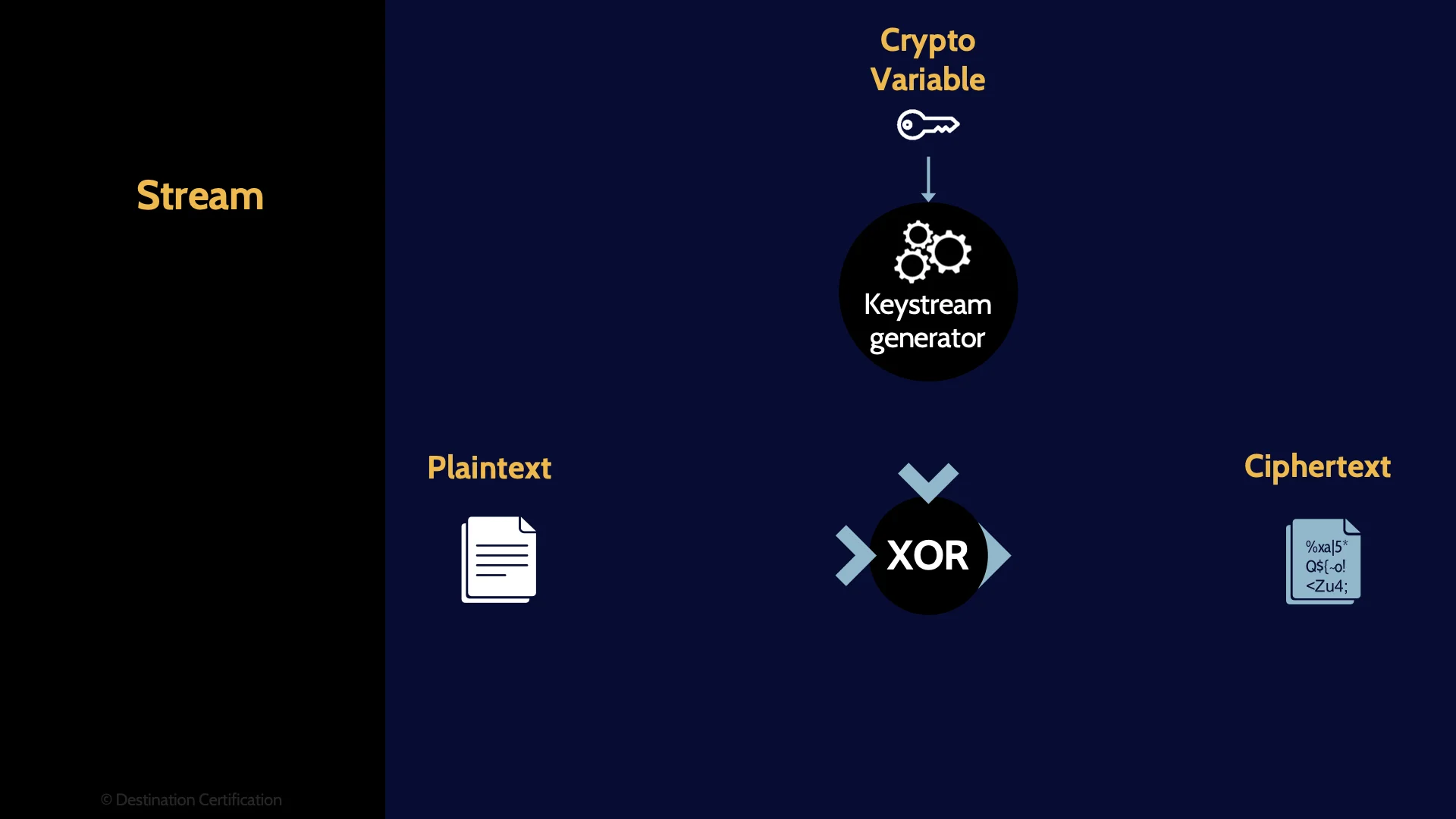
Here’s a picture of how this works. I think this is a good example of how a picture is worth a thousand words
RC4
The only major stream cipher algorithm that you need to know about is RC4. If you get any questions about symmetric stream ciphers, think RC4.

Okay, now an even bigger step back. We talked about how there are two major types of algorithms that we can use to perform two-way encryption: Symmetric algorithms and asymmetric algorithms.
Let’s venture into asymmetric algorithms now. The major, seriously cool, and useful, characteristic of asymmetric algorithms is that they use a mathematically related key-par. Two keys.
We give the two keys in the key pair special names and treat them accordingly. We call one key the private key which we must keep absolutely private and not share with anyone ever, under any circumstances. Ever!
And the other key in the key pair, we call the public key, and we give it to anyone and everyone!
Asymmetric
Having this mathematically related key pair enables us to do some seriously useful things. Asymmetric cryptography solves the two major issues discussed related to symmetric cryptography: key distribution, and scalability.
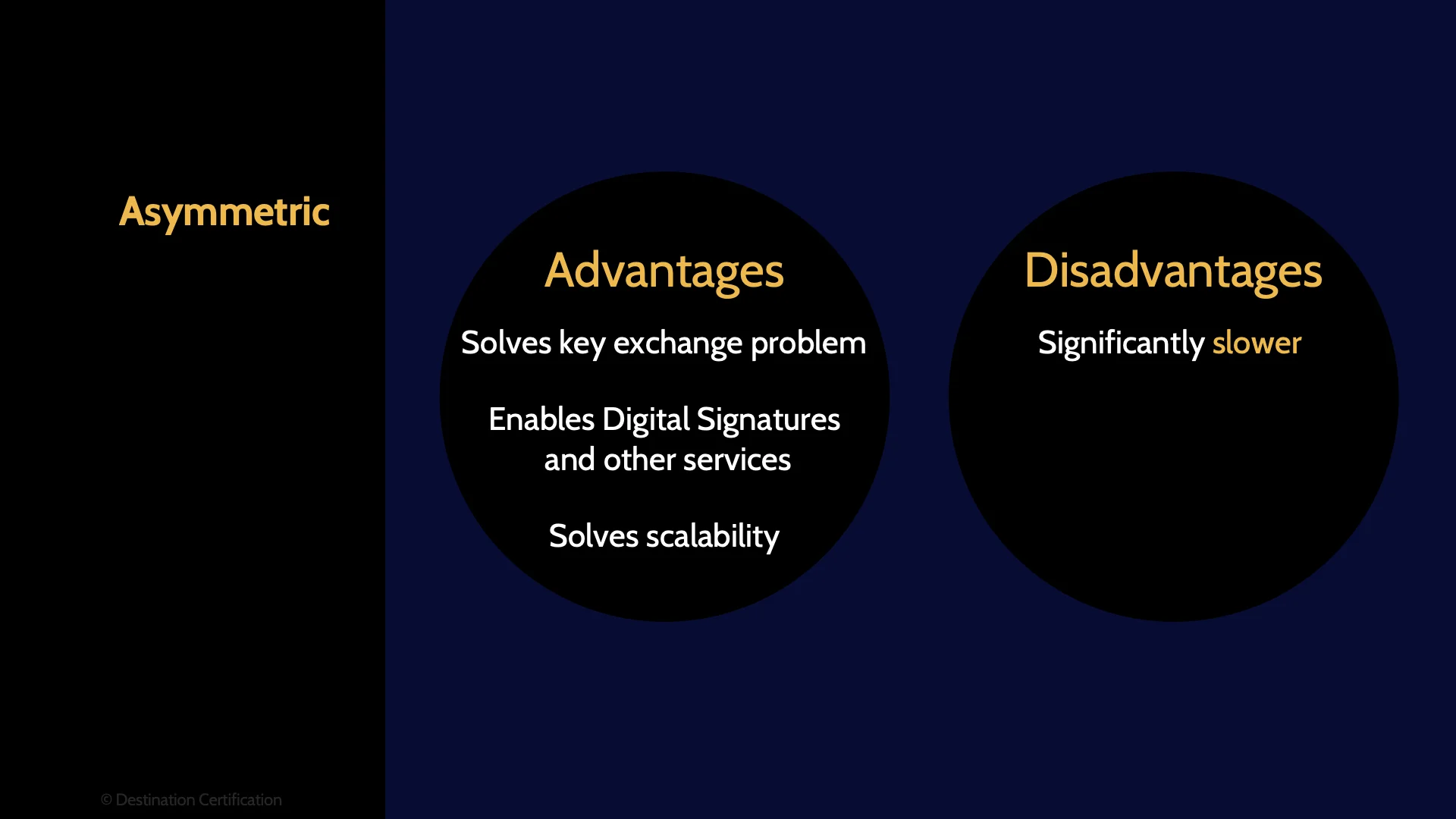
We can use asymmetric cryptography to securely and efficiently distribute symmetric keys - solving the key distribution problem. And the number of asymmetric keys we need only grows linearly and not exponentially – solving the scalability problem.
Not only that, but asymmetric cryptography also enables digital signatures, digital certificates, and the whole root of trust. More on all that in the next video.
Now it’s not all sunshine, rainbows and butterflies with asymmetric cryptography.
It has a major downside. It is slow. Like REALLY slow. It can be orders of magnitude slower than symmetric cryptography. So, whenever we need to encrypt a lot of data, or we need to encrypt as fast as possible we need to use symmetric cryptography.
Factoring
There are a few different hard math problems that Asymmetric cryptographic algorithms rely on. One of those hard math problems is factoring. It is very easy to multiply two large prime numbers together and very hard to go backwards and factor the two original prime numbers.
RSA
The one asymmetric algorithm that you need to know about that relies on factoring as the hard math problem is RSA
Discrete Log
The next hard math problem is discrete logs: it is easy to exponentiate, and again much more difficult to go backwards and find the original integers.
Diffie-Hellman (key exchange), Elliptic Curve (ECC), El Gamal, DSA
There are a few asymmetric algorithms that rely on discrete logs as the hard math problem that you need to know about:
The Diffie-Hellmann key exchange protocol is used to securely exchange symmetric cryptographic keys over an insecure channel – for example the Internet
Elliptic Curve (ECC) can provide the same strength encryption as RSA, but with a much shorter key, thus ECC is more efficient. And that’s the main thing you need to remember about it – ECC is very efficient a far as asymmetric algorithms go
Just be able to recognize El Gamal as an asymmetric algorithm which uses discrete logs as the hard math problem.
And last but not least: DSA, the Digital Signature Algorithm, as the name implies, is used for creating digital signatures.
A final bit on the hard math problems used in asymmetric cryptography. There is another hard math problem that you may have heard that is intentionally not on this MindMap: Knapsack. Significant issues have been found with using the knapsack problem as the hard math problem and therefore it should not be used.
Digital Certificates
An extremely useful tool that asymmetric cryptography enables are Digital Certificates which allow us to verify the owner of a public key
Digital Signatures
And Digital Signatures which provide integrity, authenticity and non-repudiation of both origin and delivery – we delve into much more detail on both Digital Certificates and Digital Signatures in the next video.
Substitution
How do cryptographic algorithms convert plaintext into ciphertext? There are two major and quite simple methods. Substitution and Transposition.

Substitution is simply substituting / replacing one character with another one. So, substituting a C for a D, an A for an O, and a T for a G and suddenly a cat has turned into a dog.
Caesar Cypher
Monoalphabetic
Polyalphabetic
Running
One of the earliest known examples of a substitution cypher is the Caesar Cypher aptly named after its inventor Julius Caesar. In the Caesar cipher letters are substituted for the letter three places to the right in the alphabet.
One-time Pads
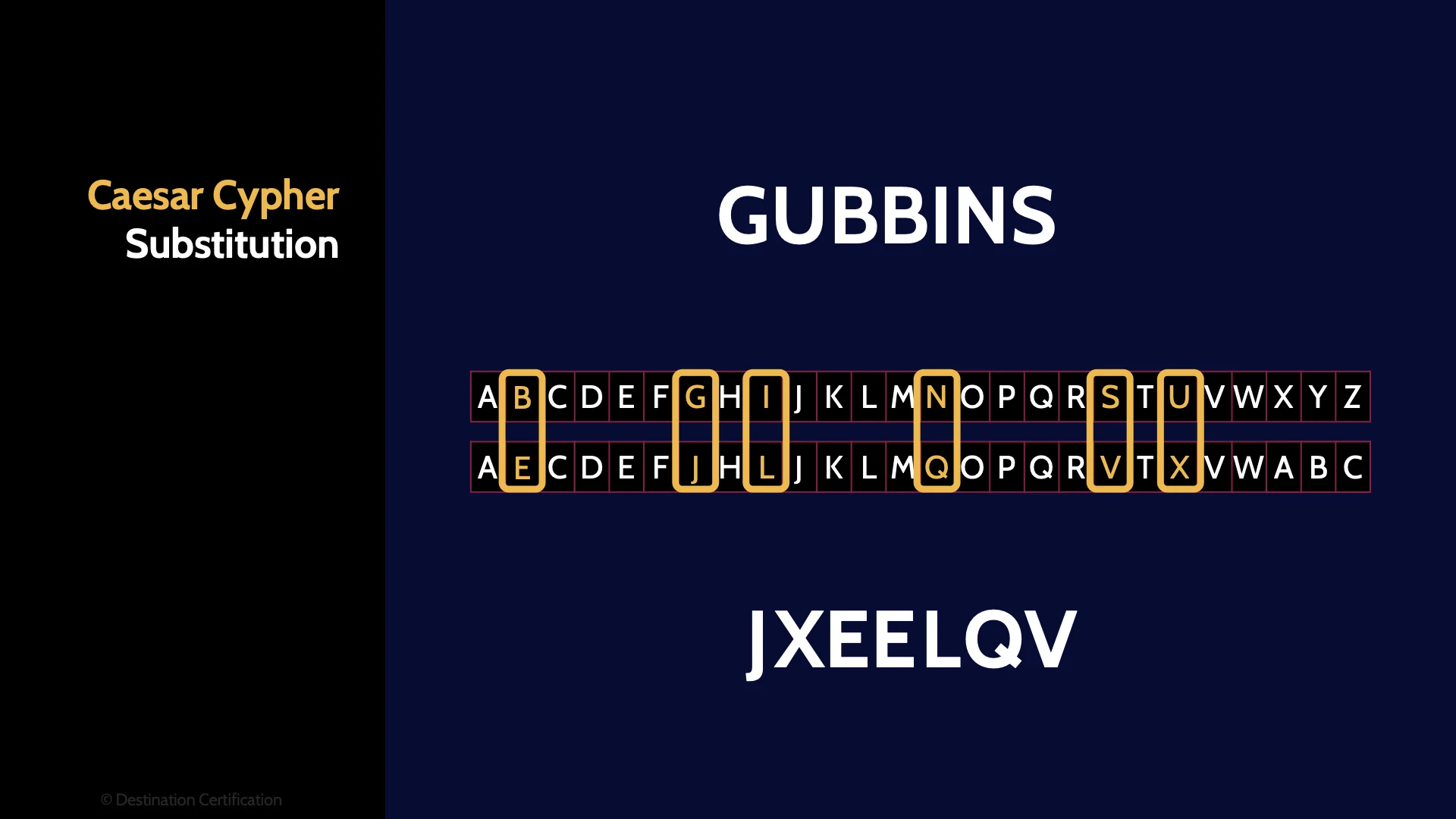
Here’s what that looks like. Notice the alphabet that is being used for substitution has been shifted to the right by three characters. A G for a J, a U for an X and so on.
The Caesar cipher is an example of a Monoalphabetic Substitution Cipher. Monoalphabetic Ciphers use just one alphabet for the substitution. There is a fixed substitution / replacement structure where if an B is replaced with an X it will always be replaced with an X - this leads to patterns. And patterns must always be avoided in cryptography.
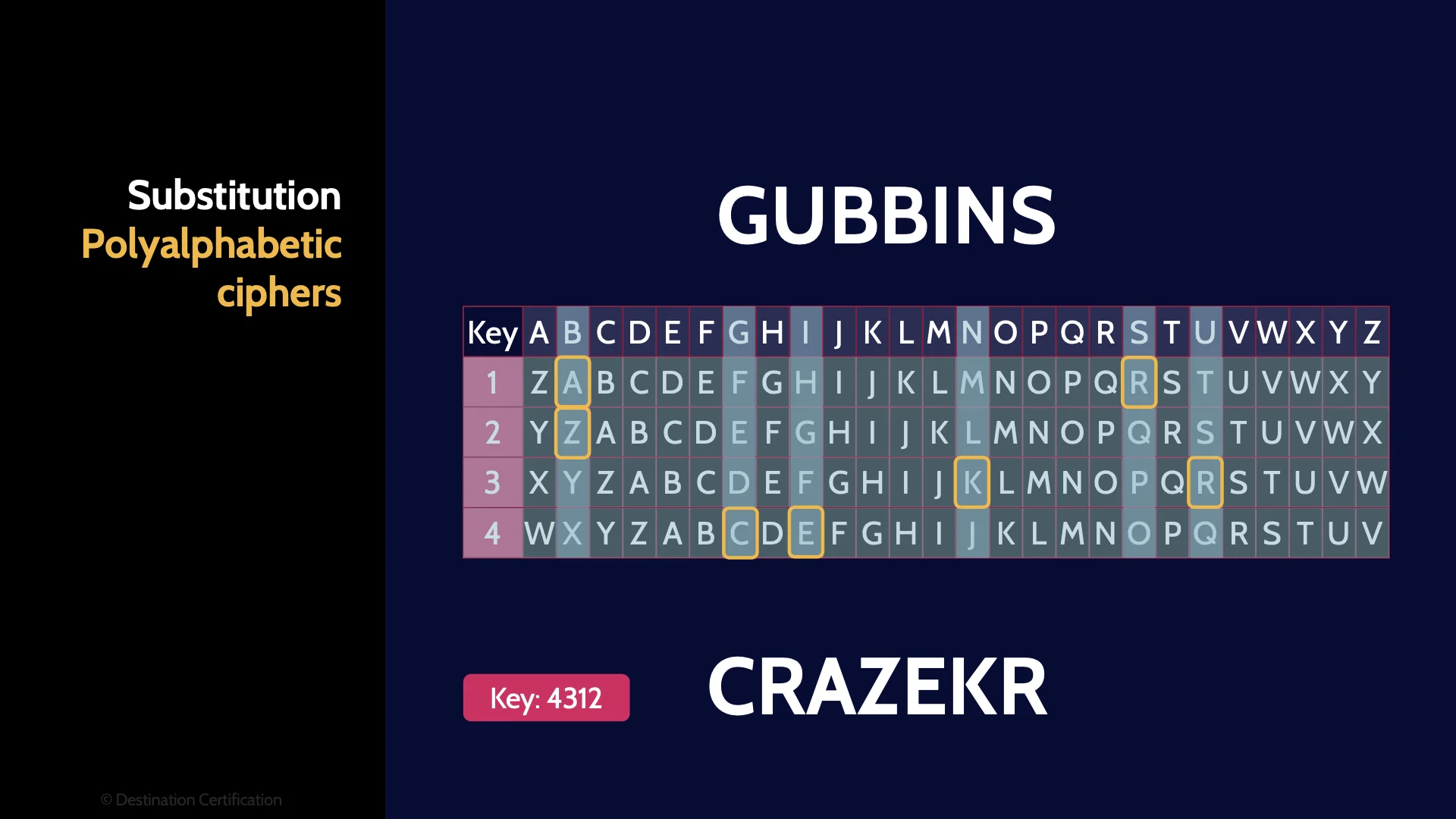
To combat patterns using substitution ciphers, we can use Polyalphabetic Substitution Ciphers which use multiple substitution alphabets and thus helps to reduce patterns.
Here’s what a simple Polyalphabetic Substitution Cipher looks like using the key 4312. As you can see the two B’s in the plaintext get encrypted into two different letters, A and Z, in the ciphertext.
A running key cipher is a substitution cipher in which text, typically from a book, is used to provide a very long keystream to draw the substituted letters from.
And finally, one-time pads. A one-time pre-shared key is required – basically a big long string of truly random characters that is at least as long as the text to be encrypted. Each character of the message, the plaintext, is encrypted by combining it with the corresponding character from the one time pad using modular addition. When done properly, using a truly random one-time pad and never reusing, it provides unbreakable encryption.
Transposition
The other major way that we can convert plaintext into ciphertext is using transposition which is simply rearranging all the letters in the plaintext.

Like this.
Spartan Scytale
Rail Fence (zigzag)
A Spartan Scytale is one of the earliest known examples of a transposition cipher.

You would take a stick of wood with a very precise diameter and wrap a thin piece of leather around the stick and then write your message on the piece of leather. When you unwrapped the strip of leather your letters would be transposed and your message encrypted. The receiver would have to wrap the strip of leather around the exact same diameter stick to decrypt the message. It worked great back in ancient Greece. It also helped that a lot less people could read…
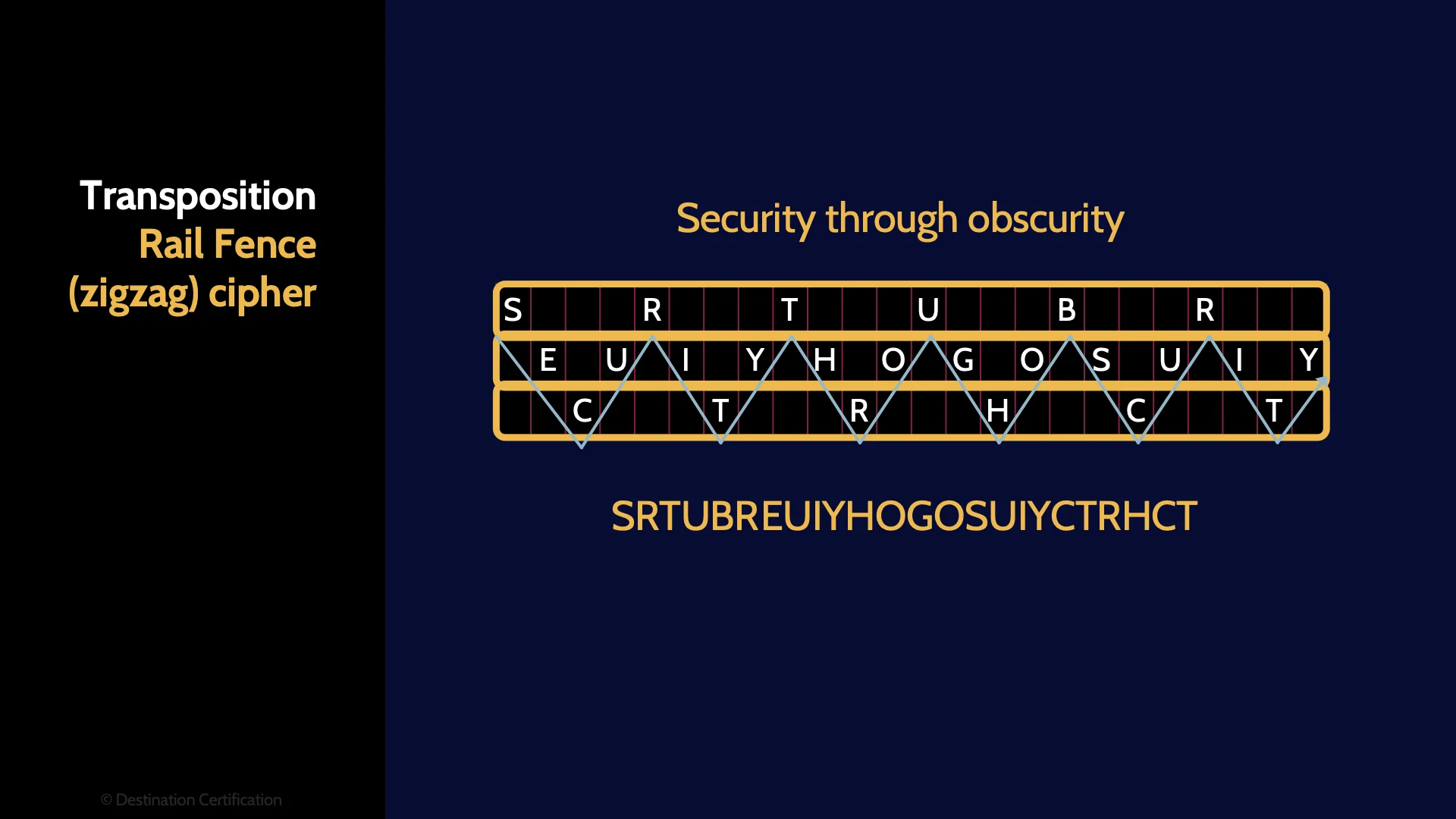
Another method of transposing letters is known as Raid Fence or zigzag. The plaintext is written in a zigzag pattern into a table and then the letters are copied out row by row thus transposing them.

And there we go - that is an introduction to Cryptography. In the next video we’ll delve more deeply into digital certificates, digital signatures, PKIs and key management. And then the video after that we’ll talk about cryptanalysis and how we can try to break all of this cryptography.
Okay I have something super cool - and totally FREE - that you absolutely need to check-out. I created a MiniMasterClass on cryptography that you can take for free right now.
t’s three in-depth videos. In the first video I start with teaching you about the fundamentals of cryptography that I just summarized in this MindMap.
In the second video, I delve into the super important topic of asymmetric cryptography in great detail.
And then in the third video, I dive even deeper into digital signatures: the services they provides, how they work, and what they can be used for.
There is a ton of in-depth information that you will find extremely helpful in your CISSP exam prep.
And did I mention that this Cryptography MiniMasterClass is completely free? It’s free.
Seriously check it out now, you’ll be glad you did. Link is in the description below.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
