Domain 1 - Privacy & Intellectual Property MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to Privacy and Intellectual Property in Domain 1, to understand how they interrelate, and to guide your studies.
This is the second of three videos for domain 1. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass.
Definition of Privacy
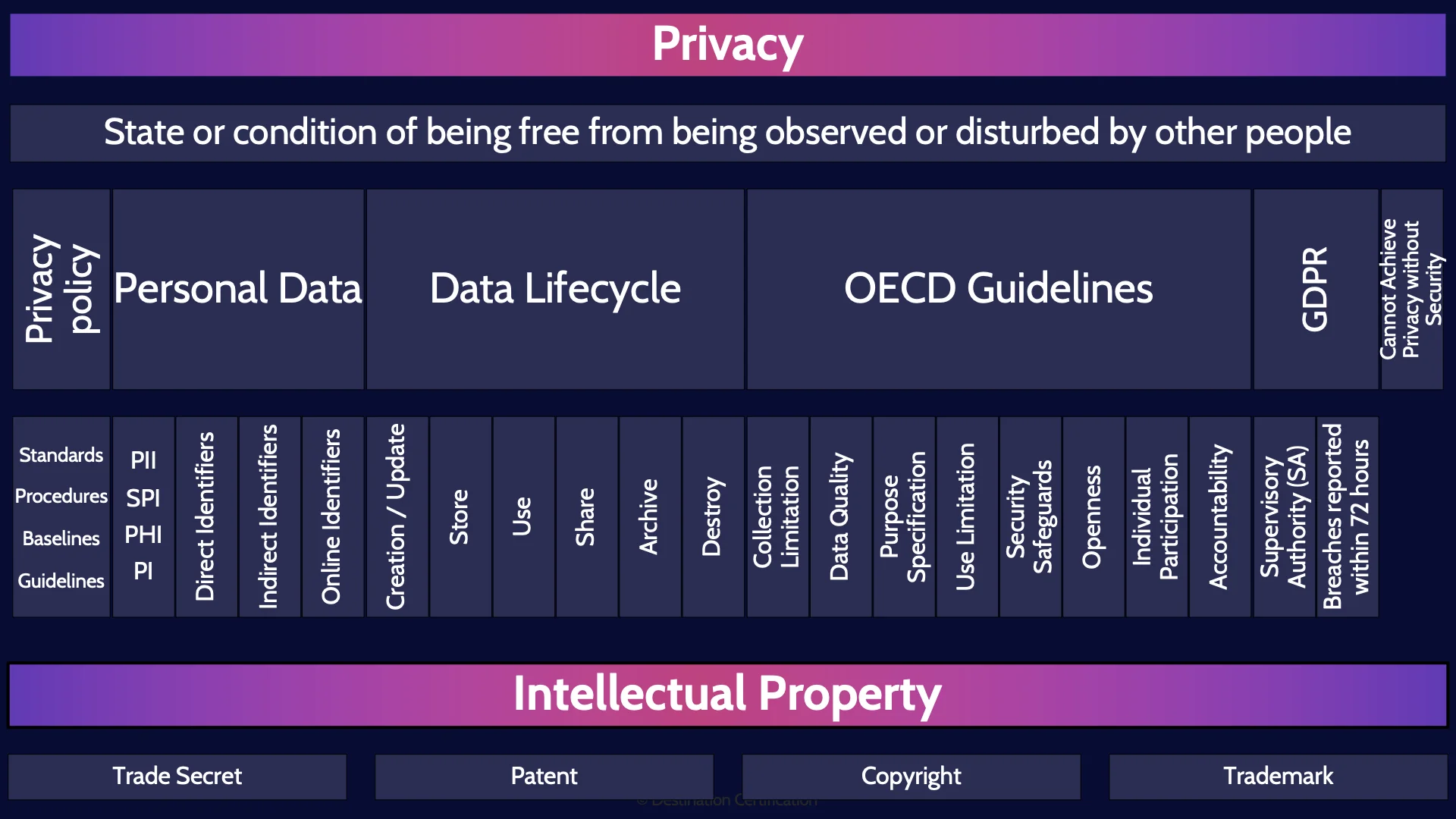
Let’s begin with a definition of privacy. It is the State or condition of being free from being observed or disturbed by other people. And you should remember that exact definition for the exam. But what does it mean? Being free from being observed and disturbed. Essentially privacy is the idea that an individual can withhold parts of their personal information from wider society. To control what personal information others know about them, as their personal information can potentially be used against them in ways that would disturb them: limit what jobs they can get, where they can travel, whether they can get health insurance, etc.
Privacy policy
Implementing strong privacy controls within an organization begins with a good privacy policy. And the most important part of a privacy policy is well defined roles with clear accountabilities and responsibilities. Many regulations around the world require that a company have a Data Controller, essentially an owner for the privacy program that is accountable for the privacy controls within an organization. For an overview of other roles see the domain 2 MindMap video which I’ve linked to.
The privacy policy should also clearly articulate what types of personal data the organization collects, how the data is used, stored, opt-out procedures, and the relevant security policies to protect the data.
Standards
Procedures
Baselines
Guidelines
Further there should be well defined standards, procedures, baselines and guidelines that are based on the privacy policy.
Personal Data
The major thing that we are protecting from a privacy perspective is Personal data which can be defined as Information that can be used on its own or in combination to identify an individual.
PII
SPI
PHI
PI
Different laws and regulations refer to personal data in different ways:
· Personally Identifiable Information (PII)
· Sensitive Personal Information (SPI)
· Personal Health Information (PHI)
· Personal Information (PI)
Direct Identifiers
There is also the concept of what data can identify an individual and to what degree. Direct Identifiers identify an individual on their own. So direct identifiers are things like Government IDs (social insurance numbers, social security numbers, drivers license numbers, passport numbers), as well as bank account numbers, certificate numbers, names and biometric data. These are all direct identifiers.
Indirect Identifiers
Indirect identifiers, do not on their own, directly identify an individual, but if you have enough indirect identifiers you can uniquely identify an individual. Indirect identifiers are things like age, gender, ethnicity, city, state, zip or postal code.
Online Identifiers
You can also group identifiers used online together, things like email address, ip address, cookies, etc.
Data Lifecycle
Now let’s talk about the data lifecycle. The idea of an data lifecycle is to identify all the stages that data goes through from when it is first created all the way to when it is destroyed. As security professionals we can then determine what controls we should put in place to protect data in each of these stages.
We ultimately want to protect the data that powers an organization's processes, systems, and applications.
Creation / Update
The first stage in the data lifecycle is Creation / update: where new data is generated, or existing data is altered, updated, or modified in some way.
Store
As soon as data is created or updated, we immediately need to store it somewhere. The storage stage is therefore where data is committed to some sort of storage repository: to memory, or a hard drive.
Use
Next, the data will be used by people or processes from across the organization. The use stage covers viewing, processing, or otherwise using the data in some way, but not modifying the data as that fits up in the first creation / update stage.
Share
Data needs to be shared with, made accessible, to others across the organization, and to customers, business partners, regulators, etc. The sharing stage is where we think about who the data can be shared with, under what circumstances and with what controls in place.
Archive
Eventually some data is no longer being actively used by the organization and so to free up storage space on the system and save costs, this data can be archived in a long-term storage solution. The data should be retained for as long as necessary based on the data retention policy.
Destroy
And the final stage of the data lifecycle is when data is no longer needed by the organization. This data should be permanently destroyed using physical or logical means. Depending on requirements, data may need to be defensibly destroyed. Checkout the link to the first domain 2 video where I go through the different data destruction methods.
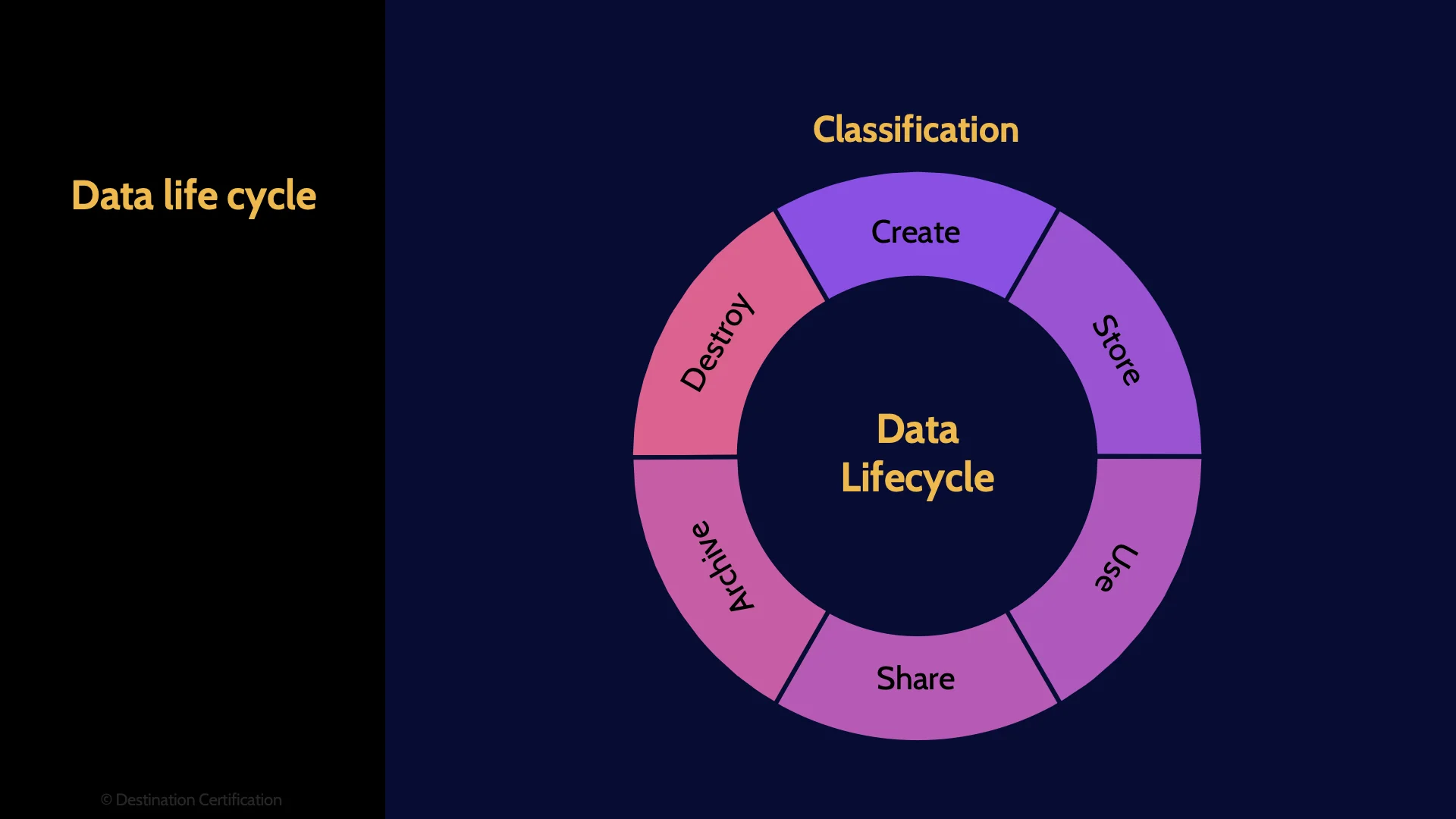
What is the most important thing to do right at the very start of the data lifecycle? Classify the data. The classification indicates how valuable the data is to the organization and therefore drives the controls that should be in place in each stage of the data lifecycle:
· Where the data can be stored, and with what level of encryption and access controls
· Who can use the data and for what purposes?
· Who can the data be shared with, and with what security controls in place?
· How long data needs to be retained?
· And the requirements for how securely the data needs to be destroyed. Are we melting hard drives or selling them on craigslist without even formatting them?
OECD Guidelines
The Organisation for Economic Co-operation and Development, the OECD, have come up with a set of privacy guidelines or principles. I’m emphasizing that word guidelines, because guidelines are not mandatory, they are best practices. This is very much true of the OECD Privacy Principles; they are not mandatory requirements that an organization must meet, but rather they provide the most internationally recognized privacy framework and the basis for the creation of leading privacy programs within an organization. They help organizations structure their privacy program and consider what the program should cover. Eight principles are defined.
Collection Limitation
Beginning with collection limitation which means that organizations should limit the collection of PII, obtain it lawfully, and where appropriate, with the knowledge or consent of the data subject. The data subject being the individual for who the data is about.
Data Quality
The data quality principle means PII should be relevant, accurate, complete and kept up-to-date. In other words if an organization collects PII they are now accountable for the integrity and accuracy of the data.
Purpose Specification
The purpose specification principle means the purposes for which PII is collected should be specified when collected. Organizations should clearly articulate what the PII they collect will be used for.
Use Limitation
The Use Limitation Principle means PII should only be used / disclosed based on the purposes for which it was collected with consent of the data subject or by authority of law.
Security Safeguards
Security Safeguards means PII should be protected by reasonable security controls against loss, unauthorized access, destruction, use, modification, etc. Basically, that good security controls need to be in place to protect the PII.
Openness
The Openness Principle relates to an organization's culture. There should be a general policy of openness about developments, practices and policies with respect to PII. Organizations should not hide or be sketchy about what they are collecting and using PII for.
Individual Participation
The Individual Participation Principle means an individual, a data subject, should have the right to obtain their data from the controller, and have their data removed. Under GDPR this is often referred to as the right be forgotten.
Accountability
And the last principle, Accountability, means a data controller should be accountable for complying with the other principles. In other words, there must be an owner, a data controller, who has clear accountability to the protection of PII.
GDPR
There are loads of different privacy laws and regulations around the world, and I’m happy to report that you do not need to be an expert on all of them for the CISSP exam. You should, however, know a wee bit about GDPR, the General Data Protection Regulation, which is the core of the European Union’s digital privacy legislation. GDPR is an extremely important regulation as it is one of the most stringent in the world, and many countries around the world model their privacy regulations on GDPR. It is very much the global bellwether for privacy.
Supervisory Authority (SA)
An important piece from this extensive legislation: GDPR defines what are known as Supervisory Authorities who are independent public authorities that need to be created in each member state of the EU. The Supervisory Authorities in each state are responsible for monitoring and enforcing compliance with GDPR, helping organizations become compliant, and conducting investigations.
Data subjects have the right to lodge a complaint with a Supervisory Authority.
Breaches reported within 72 hours
One more important piece of information to remember related to GDPR: privacy breaches must be reported within…. 72 hours.
Cannot Achieve Privacy without Security
The final piece that I’ll cover here related to privacy is that you cannot achieve privacy without security. Privacy requires that we as security professionals implement the myriad of security controls to provide confidentiality, integrity, and availability of personal data.
Intellectual Property
Lets now talk briefly about intellectual property. Intellectual property refers to the legal rights that are granted to creators and owners of intangible assets, such as inventions, works or art, symbols, designs, and so forth. These rights allow the owners to have exclusive control over the use, distribution, and commercialization of their creations, and to prevent others from using or exploiting them without permission. You need to know at a super high-level what each of the following four intellectual property laws are focused on protecting.
Trade Secret
Trade secrets refer to confidential information that provides a business with a competitive advantage over its competitors. A perfect example of a trade secret is the formula for coke. Coca Cola have never shared their formula with anyone, and nor will they ever. Companies can take legal action against anyone that steals or discloses their trade secrets without authorization.
Patent
Patents are granted to inventors and provide their owners with exclusive ownership on an invention for a set period of time. Essentially so that an inventor can profit from their invention - this encourages innovation. The amount of time a patent is valid for varies widely around the world so don’t bother memorizing anything related to how long a patent is valid for.
Copyright
Copyright protects the creative expression of an idea (not the idea itself) embodied in a fixed medium such as books, movies, songs, etc. for a set period of time. You can copyright a book, movie, or song for instance, and the point of the copyright is to prevent someone from making an exact copy of your book, movie, or song and selling it. Remember that copyright protects the expression of an idea.
Trademark
And finally, trademarks are symbols, words, phrases, or designs that distinguish and identify a brand or product from others in the marketplace. Think the Nike swoosh or McDonalds arches. Companies trademark their logo, for example, so that another company can’t use the same logo on their products and create confusion in the marketplace.

And that is an overview of Privacy and Intellectual Property within Domain 1, covering the most critical concepts you need to know for the exam.
Something really cool we are providing with these MindMap videos is a completely FREE downloadable version of all the MindMaps in PDF format. We even include a blank version of each MindMap in case you want to print them out and take notes as you listen along. Link to download the MindMaps is in the description below.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
