Investigations MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to investigations in Domain 7, to understand how they interrelate, and to guide your studies and help you pass the CISSP exam.
This is the first of six videos for domain 7. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass.
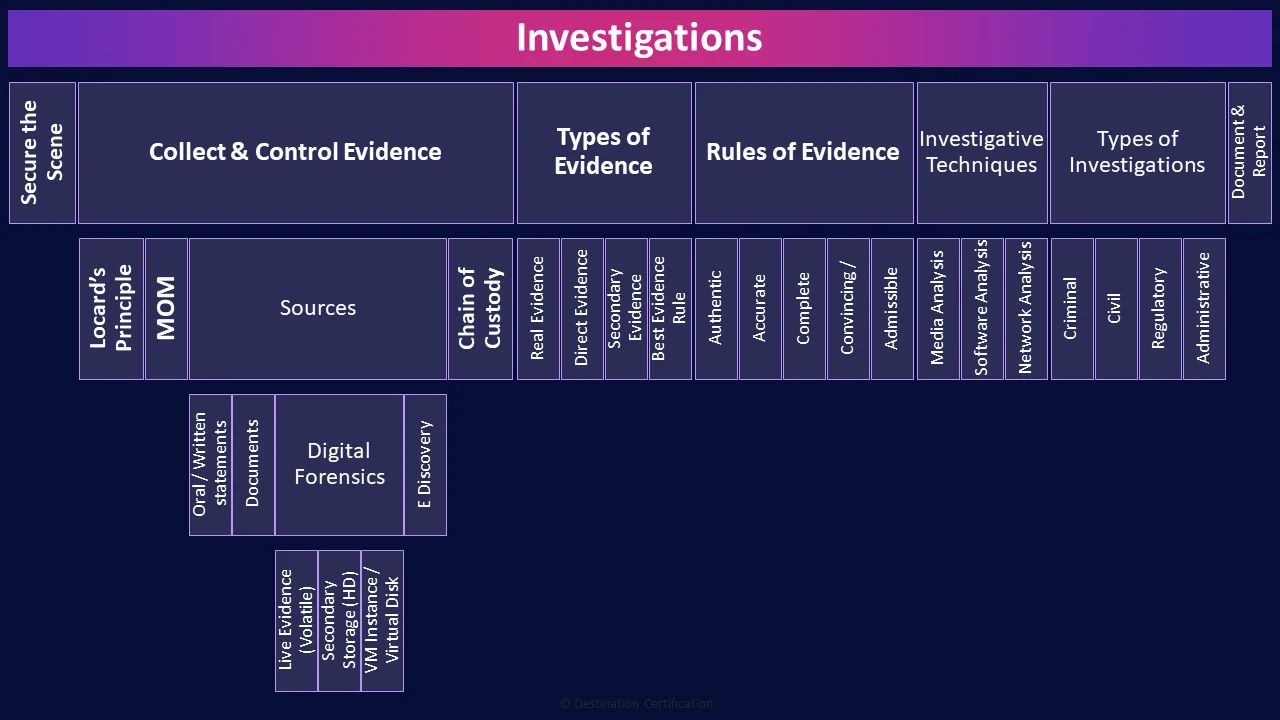
Investigations
Alright, let’s talk about how we apply the principles and methods of forensic science to investigations. This is all about what an organization needs to do if for example they have detected a breach, or had a whistleblower report something, or VISA has called asking why our systems are leaking millions of customer credit card numbers.
Secure the Scene
One of the most important first steps is securing the scene. Establishing a perimeter to prevent unauthorized persons from entering the scene in order to avoid the loss, or contamination of
evidence. Securing the scene is paramount as once evidence is contaminated it cannot be decontaminated. Securing a digital crime scene is particularly challenging as we want to preserve as much evidence as possible but balance that against things like stopping an ongoing breach. Should a computer system be unplugged from the network or even shut down? Doing so too quickly could compromise the investigation but doing so too slowly could allow additional data to be leaked.
Collect & Control Evidence
Once we begin collecting evidence there are a few principles, techniques and sources we should be aware of.
Locard’s Principle
Locard’s principle often comes up on the exam. Put simply it states that When a crime is committed, the perpetrator will leave something behind and take something with them. Locard’s principle helps investigators think through where they may be able to find evidence.
MOM
Investigators also need to find MOM: Motive Opportunity and Means. This is an investigative technique used to determine if a suspect has the Motive (for example financial gain), the opportunity (where they at the crime scene), and means (the tools and technical expertise necessary)
Sources
There are a few sources of evidence for an investigator.
Oral / Written statements
Oral or Written statements are when witnesses tell an investigator what they witnessed or write it down.
Documents
Documents are any notes, files, and the like that an investigator can find.
Digital Forensics
Digital forensics is the scientific examination & analysis of data from storage media in such a way that the information can be used as evidence in a court of law.
Live Evidence (Volatile)
One of the most challenging and important types of digital evidence is known as Live Evidence. This is any data stored in volatile memory within a system: places like RAM, and the CPU cache. Recovering live evidence requires specialized tools and any live evidence is lost when a system is powered down.
Secondary Storage (HD)
Where most digital evidence is going to be found is secondary storage, primarily hard drives, but also USB drives, memory sticks, CD & DVDs, tapes, zip disks, etc. An important point to remember is that when an investigator obtains a hard drive, they do not conduct any of their investigations on the original drive, rather they make two bit-for-bit copies, which they verify via hashing, and any investigations are conducted only on one of the copies. This helps to ensure that any evidence collected will be admissible.
VM Instance / Virtual Disk
Cloud-based systems make investigations both easier and more difficult. In Infrastructure as a Service for instance, it is possible to make an exact copy of a Virtual Machine or VM Instance including any of the live evidence on the system – this is often referred to as snapshotting – and it makes collecting evidence easier. More challenging is requesting and conducting investigations of physical hard drives. In the public cloud, the cloud provider is unlikely to provide physical hard drives as other client data will also be stored on those drives, but investigators can request virtual disks or volumes.
E Discovery
E Discovery or Electronic Discovery is the process of identifying, collecting and producing electronically stored information for legal proceedings.
Chain of Custody
The Chain of Custody. You should associate chain of custody with one word: Control. Chain of custody is the process of documenting the complete journey of evidence during the life of the case. Demonstrating that you had control of the evidence, from the moment it was collected to potentially years later when it is presented in a court of law, and thus the evidence has integrity.
Types of Evidence
Of the different types of evidence, we just spoke of, we can categorize them in a few different ways.
Real Evidence
Real evidence is tangible and physical objects like hard drives. Crucially, data is not considered to be real evidence as we can’t see data on a hard drive. And even if we could see the bits we don’t have the algorithms necessary on our heads to turn those bits into an image, video, or audio. Data is not a tangible / physical object.
Direct Evidence
Direct evidence is evidence that speaks for itself and requires no inference. Examples of direct include eyewitness accounts and confessions.
There are three other types of evidence that I am intentionally skipping over here as they are important to know for the exam: Circumstantial Evidence, Collaborative Evidence & Hearsay Evidence.
Secondary Evidence
Ok, back to the types of evidence I would suggest you know: Secondary evidence is a reproduction of, or substitute for an original document or item of proof – very importantly here, data IS considered to be Secondary Evidence, because we can’t see data directly – we have to reproduce it through say a JPEG algorithm to turn the bits into a picture we can see.
Best Evidence Rule
And the final one: The best evidence rule is a legal principle that applies to any of the evidence we have discussed, and it simply means the courts view original, unaltered evidence, as superior evidence, or the best evidence.
Types of Evidence

Here is a summary of the different types of evidence.
CORRECTION: Collaborative should be “Corroborative”
Rules of Evidence
That leads us to the five rules of evidence which are required for evidence to be considered useful in an investigation
Authentic
Authentic means you can tie the evidence back to the scene. You can prove the evidence relates to the incident in a relevant way.
Accurate
Accurate equates to integrity. You can prove the evidence has integrity
Complete
Complete means you collect all evidence, even exculpatory evidence which might help clear a suspect.
Convincing / Reliable
The evidence must be convincing and reliable and explainable to a jury. Your evidence collection and analysis procedures must not cast doubt on the evidence's authenticity and veracity – its degree of truth.
Admissible / Believable
And finally, you want your evidence to be admissible. This is the most basic rule - the evidence must be able to be used in court of law or elsewhere.
Investigative Techniques
Now, what are some of the techniques that we can use to analyze the evidence that we have collected?
Media Analysis
Media analysis, often referred to as computer forensics, is examining physical media for evidence, such as hard drives. Media Analysis includes trying to recover data from a hard drive that someone has drilled a hole in, put in the microwave, or abused with a hammer.
Software Analysis
Software analysis, also referred to as software forensics, is examining software, such as malware, to determine what the software was designed to do. For example: encrypt files for ransomware or exfiltrate credit card numbers. Another important part of Software analysis is attribution: carefully analyzing the code to identify who authored the software.
Network Analysis
Network analysis is examining network traffic and logs files to identify how an attacker initially gained access to the network, how they traversed the network, what they gained access to, and what they compromised.
Types of Investigations
There a few different types of investigations that you need to know about
Criminal
Criminal investigations deal with crimes and the legal punishment of criminal offences. Criminal investigations are driven primarily by Law Enforcement with support from the organization.
Civil
Civil investigations deal with disputes between individuals, organizations, or between the two, in which compensation is awarded to the victim. These investigations can be driven by law enforcement or the organization.
Regulatory
Regulatory investigations deal with violations of regulated activities, such as breaches of Personally Identifiable Information, and will be driven by the Regulator.
Administrative
Administrative investigations deal with an organization investigating its own internal incident. Based on findings it may become a criminal/civil/regulatory investigation.
Document & Report
And the final part of any investigation is the extremely thorough documentation of evidence collected and preparing to present that evidence to the relevant stakeholders: a judge and jury, the opposition, regulators, investors, etc.

And that is an overview of Investigations within Domain 7, covering the most critical concepts you need to know for the exam.
A brilliantly helpful feature of our CISSP MasterClass is that you can have your own personal CISSP mentor who will guide you to confidently passing the CISSP exam.
Get completely personalized guidance on how to create a study plan that will work for you. Have someone there to encourage you and ensure you’re on track, and ready for the exam.
Learn more about our personalized mentoring here at destcert.com/CISSP

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
