Risk Management MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to Risk Management in Domain 1, to understand how they interrelate, and to guide your studies.
This is the third of three videos for domain 1. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass.
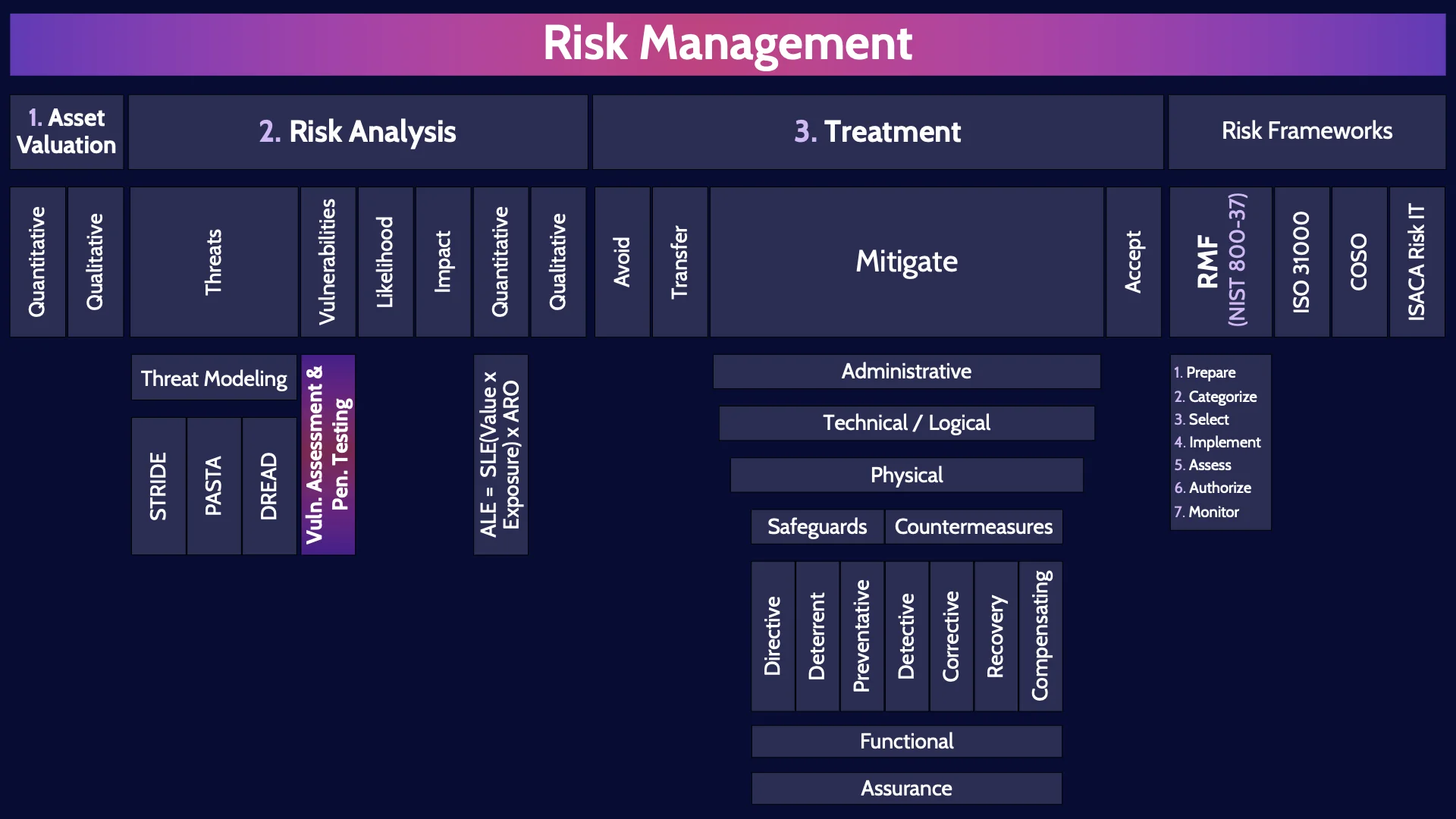
Risk Management
Risk Management. This is a super important topic in security. We as security professionals have a colossal challenge: how do we best protect all the assets across an entire organization.
We never have unlimited budgets, or an unlimited amount of time available to perfectly protect everything.
So how do we best protect the assets within the organization given our limited budgets and time? One super useful method to help us figure this out is Risk Management. Risk Management is an essential component of any comprehensive security program, as it enables organizations to prioritize their security efforts and allocate resources effectively.
Risk management is fundamentally focused on the identification, assessment, and prioritization of risks and the economical application of resources to minimize, monitor, and control the probability and/or impact of those risks.
At the 10,000 foot level, it's helpful to think about Risk Management comprising three major steps: Asset Valuation, Risk Analysis, and Treatment . Let's go through these three steps.
1. Asset Valuation
Starting with Asset Valuation. Asset Valuation is conceptually incredibly simple: assign a value to each asset. In other words, figure out how valuable each asset is to the organization so that we can then rank the assets from most on down to least valuable. Simple idea - super hard to do in practice. There are two major ways that we can rank assets. Quantitative & Qualitative analysis.
Quantitative
Quantitative analysis is where we assign monetary values to each asset.
We say this asset is worth a dollar and this asset is worth $2.7 million dollars.
Quantitative analysis is absolutely the preferred method. We would ideally love to assign a nice dollar value to every asset. Unfortunately, for the vast majority of assets this isn’t possible with any sort of reasonable accuracy. Can you confidently say our organization's reputation is worth $736 million dollars, or this data set is worth exactly 23,849 pesos, or this critical application is worth €13.18 million euro. No. For most assets we absolutely cannot assign a monetary value to them. WE may know something is valuable but assigning an exact dollar value is nigh impossible.
Qualitative
And that is why the vast majority of the time we use qualitative analysis to rank assets. Qualitative analysis is simply a relative ranking system, where you compare assets and say: well this asset is more valuable than that one, which is less valuable than that one. You rank assets relative to each other. And you often create categories like high, medium, and low value and sort assets into these categories.
2. Risk Analysis
Once you have completed asset valuation, you will have a nicely ranked list of assets. And it is now time to move to step two of Risk Management: Risk Analysis. Risk Analysis is where you identify the risks associated with each asset. To identify and understand the risks associated with each asset you need to look at four things: threats, vulnerabilities, impact, and likelihood.
Threats
Threats are any potential danger.
Threats are events, situations, or actions that have the potential to cause harm or damage to an organization's assets, operations, or reputation. Threats can come from a wide range of sources, such as natural disasters, cyber attacks, fraud, theft, or human error.
Threat Modeling
A useful tool we can use to help us systematically identify the threats related to an asset is Threat Modeling Methodologies. There have been many different Threat Modeling Methodologies created over the years, and there are three you should know about in particular.
STRIDE
STRIDE is essentially the quick & easy, but not super thorough methodology you can use to identify threats. For the exam make sure you know that the S in STRIDE stands for Spoofing, and that spoofing is a violation of integrity, and the T in STRIDE stands for Tampering, which is a violation of integrity, and so forth.
PASTA
PASTA - the Process for Attack Simulation and Threat Analysis
is the super time consuming, super in-depth methodology for threat modeling. PASTA is a seven-step, risk-centric methodology. PASTA provides way more useful results and it takes into account the business value of assets, compliance issues, and provides a strategic threat analysis. So STRIDE is the quick and easy way of systematically identifying threats and PASTA is the super time consuming method that produces way more useful and nuanced results.
DREAD
The third methodology you should know about is DREAD - . DREAD is different than STRIDE and PASTA. DREAD is not used to identify threats, rather it is used to prioritize a list of threats that have already been identified. STRIDE and DREAD are often used together. STRIDE is used to identify the threats, and DREAD is used to prioritize the identified threats.
Vulnerabilities
The next major piece that we need to look at as part of Risk Analysis is Vulnarbilites. A vulnerability is a weakness that exists.
Vulnerabilities are weaknesses or gaps in an organization's security or control systems that can be exploited by a threat to cause harm or damage to the organization's assets, operations, or reputation.
Vulnerability Assessment & Pen Testing
Two techniques that can be used to systematically identify vulnerabilities are Vulnerability Assessment and Penetration Testing which I’ll talk about in detail in the second MindMap video of Domain 6 - link in the description below.
Likelihood
Likelihood or probability is simply the chance that a particular risk event will occur. It is a measure of the likelihood of a potential risk turning into an actual event.
Impact
And the final piece we have to look at to fully understand a risk is the impact. Impact refers to the potential harm or damage that could result from a particular risk occurring. Impact is essentially whatever bad thing is going to happen to the organization as a result of a risk occurring: downtime, reputational damage, data integrity issues, a breach, ransomware, the list unfortunately goes on, and on, … and on.
Quantitative
Alright, so as part of risk analysis we are going to come up with a giant list of risks. We need to rank these risks to figure out which risks are of greater or lesser concern. There are two techniques we can use to rank the risks: Quantitative & Qualitative analysis. The same techniques we talked about for ranking assets.
Quantitative risk analysis is where we try to calculate exactly how much a given risk is going to cost the organization per year.
It’s super helpful if we can calculate this, as it makes it much easier to determine what controls are cost justified to put in place to mitigate a risk.
ALE = SLE(Value x Exposure) x ARO
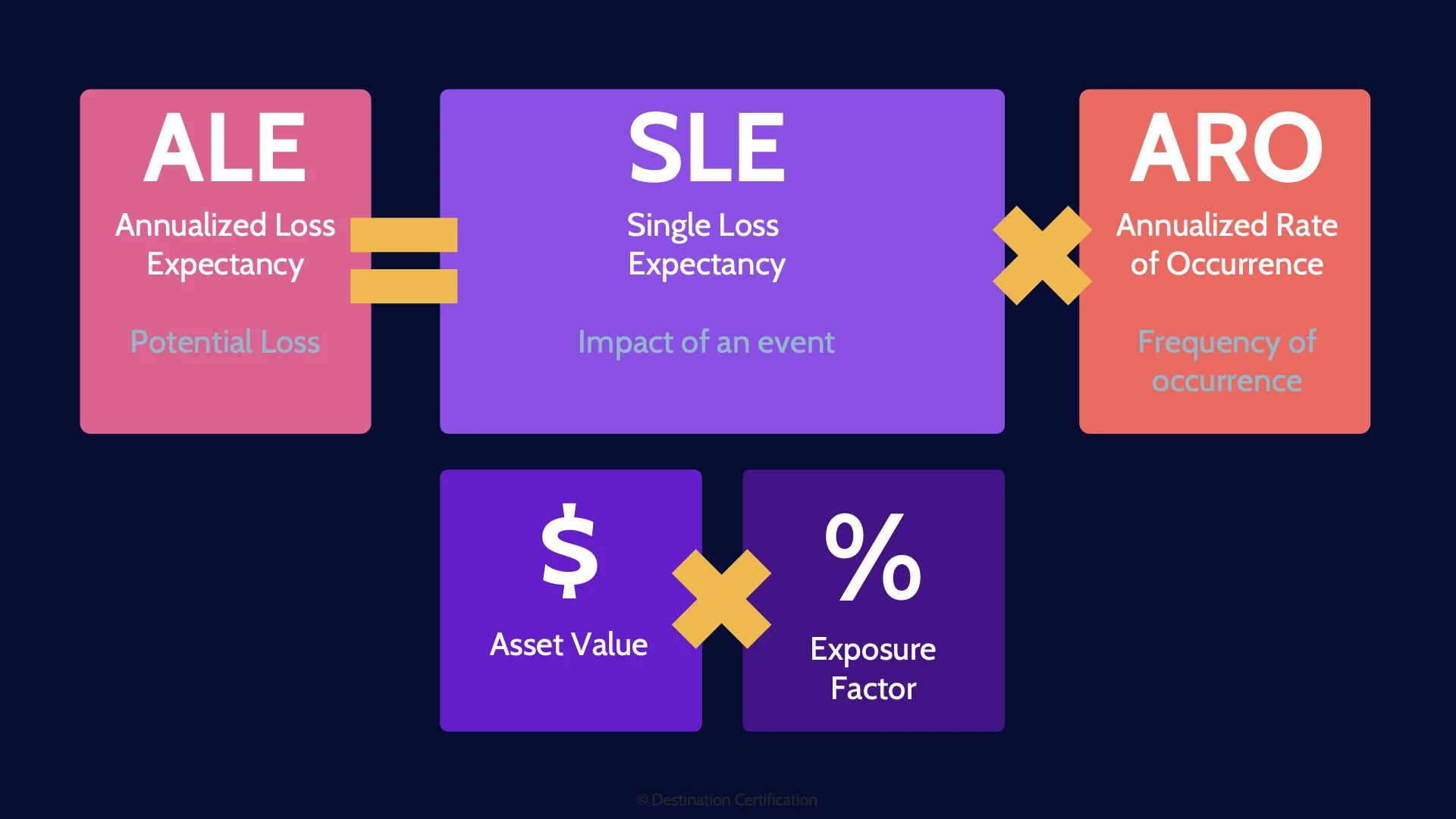
There is a super simple formula you can use to calculate how much a risk is going to cost the organization per year. It’s known as the ALE calculation. The Annualized Loss Expectancy Calculation. And you definitely need to know this formula for the exam.
To calculate the ALE, you first need to calculate the SLE. The single loss expectancy, which is simply how much is a risk going to cost the organization if the risk occurs once. To calculate the SLE you multiply the Asset Value times the Exposure Factor.
The asset value is simply what the asset is worth. And the Exposure Factor is a percentage that represents what percent of the asset you expect to lose if the risk occurs. And exposure factor of 10% would mean you expect to lose 10% of the asset if the risk occurs. Or an Exposure Factor of 100% would mean you expect to lose ALL of the asset if the risk occurs.
So to calculate SLE, multiply the Asset Value with the Exposure factor and that will tell you how much it’s going to cost the organization if the risk occurs once.
But of course the whole point of this ALE formula is to calculate how much a risk is going to cost the organization annually - per year. So we need to multiply the SLE times the ARO. The ARO is the Annualized Rate of Occurrence. The ARO represents how many times per year you expect a risk to occur. If you expect the risk to occur once per year: the ARO will be one. Five times per year, the ARO would be 5, and so on.
So super simple formula that we would love to use all the time, but we can’t. Because the three simple numbers we need: Asset Value, Exposure Factor, and ARO are often totally impossible to determine with any sort of reasonable accuracy.
Qualitative
And that is what forces us to use Qualitative analysis most of the time. And like I said before, qualitative analysis is a relative ranking system. Not great, but a whole lot better than nothing.
3. Treatment
Which brings us to the third major step is Risk Management. Treatment. Treatment is where we figure out how to treat the risks we’ve identified - do something about the risks. There are 4 major treatment methods: Avoid, Transfer, Mitigate and Accept. Let’s go through them.
Avoid
Starting with risk avoidance. Risk avoidance means implementing measures to prevent the risk from occurring or choosing not to engage in activities that would cause the risk to occur. Don’t want to face the risk of near certain death of jumping out of an airplane with no parachute?
Don’t jump out of an airplane with no parachute. That’s risk avoidance.
Transfer
Risk transference means buying an insurance policy. An organization can purchase an insurance policy to transfer the financial burden of a particular risk to their insurer. Super critical to remember from a security perspective though: you can never transfer or delegate accountability. So if an organization has purchased an insurance policy, they are not transfering the accountability for a risk to their insurer.
Mitigate
Risk mitigation is what we spend most of our time on as security professionals. Risk mitigation is implementing various controls to reduce the risk. We’ll talk through a bunch of different types of controls in just a moment - preventative controls, detective controls, corrective controls, etc. So risk mitigation is about reducing the risk by implementing various controls. Which raises an important question: can we ever find the perfect set of controls that will completely eliminate a risk? The answer is no. Which brings up another important term: residual risk. Residual risk is the risk that is left over after we have implemented mitigating controls.
There are three major methods we can use to implement mitigating controls.
Administrative
Administrative means policies, procedures, and other organizational practices that we put in place to manage risks. Administrative controls are things like security policies and employee training and awareness.
Technical / Logical
Technical / logical controls are the technologies we put in place to manage risks. Things like firewalls, Intrusion Detection Systems, encryption, automated backups, etc.
Physical
And Physical controls are the physical security stuff such as fences, cameras, locks, fire suppression systems, etc.
So we can implement controls using any of those three major methods: Administrative, Technical / logical & Physical.
Safeguards
And one more layer here to define before we get into the actual controls. We can categorize the controls into two major groups: Safeguards and Countermeasures. Safeguards are the controls we put in place to try and ensure a risk doesn’t occur. So within this category of safeguards we have the following three controls:
Directive
Directive controls are measures that provide guidance and instruction to personnel on how to handle risks. Directive controls direct behavior. How do we tell someone to do something within an organization? Policies. Policies are a perfect example of a directive control.
Deterrent
Deterrent controls discourage individuals from engaging in risky behavior. Keyword here is discourage. Deterrent controls don’t prevent someone from doing something, they discourage them. A perfect example of a deterrent control is a sign that says private property - all trespassers will be shot.
That sign wouldn’t prevent me from walking onto a property but if this was in the US where everyone has at least 37 guns, and there’s no public healthcare, it would definitely discourage me. Sorry for picking on the US here - but I’m Canadian, I’m allowed to. We’re like the annoying younger sibling of the US.
Preventative
Alright, now preventative controls are measures that aim to prevent / stop a risk from occurring. Examples of preventative controls include razor wire topped fences, login mechanisms, and firewalls.
Countermeasures
As I said, we can categorize the controls into two major groups: Safeguards and Countermeasures. Countermeasures are the controls we put in place to detect and respond to a risk that has occurred. So within this category of countermeasures we have the following three controls:
Detective
Detective controls are measures that help identify risks that have occurred or are currently ongoing. Examples of detective controls include SIEM systems - Security Information and Event Management systems, Intrusion Detection System, smoke detectors, etc.
Corrective
Corrective controls are measures that aim to reduce the negative impacts of risks after they have occurred. A perfect example of a corrective control would be a fire suppression system that activates to put out a fire.
Recovery
Recovery controls are measures that help organizations recover from the negative impacts of risks - get back to business as usual. A good example of a recovery control is a Disaster Recovery Plan (DRP).
Compensating
And, finally, compensating controls are the measures we put in place to mitigate the negative impacts of risks when other controls are not effective or feasible. So essentially, compensating controls make up for the lack of a better control.
Functional
Okay, and now the final piece to cover related to controls. Functional and Assurance. Every good control is supported by these two key aspects: functional and assurance.
The Functional aspect refers to the function that a control is meant to perform. For example, what is the function of a firewall? Firewalls control the flow of traffic between two network segments. So a good firewall control is going to provide this functionality - the ability to control the flow of traffic. Any good control is going to perform some sort of useful function.
Assurance
The second aspect that any good controls needs to provide is assurance. We need to be able to get assurance that a control is working correctly on an ongoing basis. So going back to a firewall, how would we typically get assurance that a firewall is working correctly on an ongoing basis? By logging and monitoring the firewall. So any good control is going to provide this assurance aspect. And that finally wraps up discussion of risk mitigation.
Accept
So let's zoom back up to the final risk treatment method. Risk acceptance. Risk acceptance is a deliberate decision to accept a certain level of risk and its potential consequences. Who within an organization should be accepting the risk associated with a particular asset? The asset OWNER. Owners are accountable for the security of an asset, so owners are best positioned to deliberately accept a risk or not.
Risk Frameworks
Risk management frameworks provide a structured and systematic approach to managing risks within an organization. There are a few risk management frameworks that you should recognize the names of, and there is one framework in particular that you really need to focus on. Let’s start with the framework that you need to focus on.
RMF (NIST 800-37)
The RMF. The Risk Management Framework. This is a National Institute of Standards and Technology (NIST) publication. NIST 800-37. The RMF defines a structured, seven-step process that helps organizations to manage risks to their information systems and data. You need to remember the 7 steps at a high-level. The order of the steps and what is happening at each step.
Prepare
Categorize
Select
Implement
Assess
Authorize
Monitor

The seven steps of the RMF are:
- Prepare to execute the RMF
- Categorize systems - this step is essentially focused on identify the risks
- Select security controls - select the appropriate mitigating controls for the risks you identified
- Implement the controls
- Assess the effectiveness of the implemented controls
- Authorize, based on the results of the assessment, ideally the owner of the system should make the decision as to whether the system can be put into production.
- Monitor. Perform ongoing monitoring of the controls to ensure they continue to operate effectively in production.
ISO 31000
The three other frameworks you should be able to recognize as being risk management frameworks are: ISO 31000
COSO
The COSO risk management framework
ISACA Risk IT
And ISACA Risk IT

And that is an overview of Risk Management within Domain 1, covering the most critical concepts you need to know for the exam.
In our over 20 years of teaching CISSP classes, we have noticed that folks tend to make a few critical mistakes in their CISSP preparation. Accordingly we have created this super useful free guide that will explain 3 of the most common mistakes - and most importantly how to avoid them.
You can access the free guide here: https://destcert.com/3-mistakes-to-avoid/
Link in the description below as well.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
