Cryptanalysis Explored: CISSP Domain 3 MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to cryptanalysis in Domain 3, to understand how they interrelate, and to guide your studies.

This is the 8th of 9 videos for domain 3. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass.
Cryptanalysis
In the last two videos we talked about all the wondrous things we can do with cryptography.
Now let’s talk about how we can break it!
Cryptanalysis is the art and the science of understanding how cryptosystems work so that you can find ways to defeat them OR strengthen them if you want to have less fun.
Cryptanalysis is the process of decoding secrets and gaining access to encrypted messages and even forging new messages.
Cryptanalytic Attacks
There are two major types of Cryptanalysis: Cryptanalytic Attacks, and Cryptographic Attacks.
The primary goal of Cryptanalytic attacks is to deduce the key. Find the crypto variable, the key, that can be used to decrypt the ciphertext.
Remember that – the primary goal of all Cryptanalytic attacks I’m about to talk about is to deduce the key.
Brute Force
A brute force attack is the simplest type of attack - try every possible key until you find the right one. Simple but totally ineffective for algorithms that use longer keys.
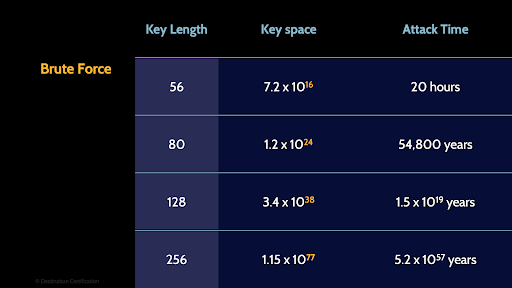
Recall the key space, the total number of possible keys, doubles every time the key length is increased by a single bit. So, the key space grows exponentially. This becomes an insurmountable problem very quickly. For algorithms that use 128-bit or especially 256-bit keys – there is no system in existence now or into the reasonably foreseeable future that could brute force keys of that length.
Ciphertext Only
So, moving on to the next type of attack: Ciphertext only attacks – this means the cryptanalyst, the attacker, only has ciphertext to work with to try and deduce the key. Accordingly, Ciphertext only attacks are very difficult.
Known Plaintext
Known plaintext attacks means the attacker has access to both the ciphertext and the associated plaintext. The attacker knows the plaintext. So, uh if the attacker knows the plaintext, then what are we doing here?
Recall the primary goal of Cryptanalytic attacks is to deduce the key. The attacker is using the plaintext and associated ciphertext to try to deduce the encryption key used. Once the attacker has the key they can decrypt other messages and even forge messages!
Chosen Plaintext
The next two types of attacks have the word chosen in them. Chosen means the attacker has access to the machine or algorithm which is being used to perform the encryption and decryption. In a chosen plaintext attack, the attacker is choosing what plaintext to feed into the machine or algorithm, and then looking at the resultant ciphertext to try and deduce the key.
Chosen Ciphertext
And chosen ciphertext is the same idea but in the other direction. The attacker is choosing what ciphertext to feed into the machine or algorithm, and then looking at the resultant plaintext to try and… you guessed it: deduce the key.
Linear & Differential Analysis
Factoring
Factoring attacks. There is only one asymmetric algorithm that you need to know about that uses factoring as the hard math problem. And that algorithm is of course… RSA. So if you see factoring attack, think RSA, or if you want to attack RSA, think of the factoring attack.
Cryptographic Attacks
Moving on. Lets now talk about cryptographic attacks. Cryptographic attacks are not solely focused on deducing the key. Some are… and some aren’t. Given that very informative introduction to cryptographic attacks, let's now talk about them.
Man-in-the-middle
Man-in-the-middle attacks are where the attacker places themselves in the middle of a conversation. This allows the attacker to eavesdrop on the communications being sent back and forth and possibly alter the communications or decipher them.
Replay
A replay attack is a form of man-in-the middle attack. The attacker eavesdrops and intercepts data being sent, such as intercepting a user’s hashed password being sent to a server to authenticate the user. In a replay attack, the attacker cannot necessarily decipher the data they have intercepted, but they can replay it, re-send it later on to their advantage. For example, the attacker could resend the hash of a user’s password later on masquerading as the user to gain unauthorized access.
Pass the Hash
And a Pass the Hash attack is a type or Replay attack. Specifically, what I just used as the example for replay where the attacker captures a hashed password and then re-sends the password later to authenticate as a user.
So remember, a pass the hash attack is a type of replay attack, and a replay attack is a type of man-in-the-middle attack.
Temporary Files
When a crypto system is encrypting and decrypting data, temporary files are often used to temporarily store plaintext, ciphertext and encryption keys. These temporary files may not be sufficiently secured and thus in a temporary file attack the attacker gains access to the sensitive plaintext or encryption keys by accessing these temporary files.
Implementation attacks
Implementation attacks target weaknesses in how an algorithm, cryptosystem, protocol or application has been implemented. A perfect example that you should remember for the exam is WEP – Wired Equivalency Protocol which implements the RC4 encryption algorithm to secure wireless traffic. WEP should never be used because it is horribly broken and insecure. And yet, the RC4 encryption algorithm is excellent - WEP does a terrible job of implementing RC4. The initialization vectors used are two short and a portion is static – among other issues.
Side Channel
Side channel attacks are any type of attack where sensitive information is gathered by carefully monitoring a system that is performing some cryptographic tasks.
Power
Power side channel attacks measure how much power is consumed by certain calculations.
Timing
Timing attacks measure how long certain operations take.
Radiation Emissions
And in side channel radiation emission attacks the electromagnetic waves that are emanated by a system are closely monitored
Dictionary Attack
Dictionary attacks are a form of brute force attack used to find encryption keys or a user’s password. Rather than trying every possible combination in some sequential order, dictionary attacks try the MOST LIKELY combinations first – thus dictionary attacks can be a much more efficient and faster method than just a simple brute force attack. For example, if you want to figure out a user’s password, the best password to try first is the most common password in the world: password or 123456. There are dictionaries, giant data sets, of the most common passwords in the world that can be used for dictionary attacks.
Rainbow Tables
Rainbow tables are an extension of password dictionaries. Here’s the idea, a user’s password should never be stored in plaintext in a password database. Instead it is much more secure to store the hash value of a user’s password. This poses a problem for attackers. If they steal a password database they will just have a bunch of hashed passwords and of course hashing is one way, you cannot take a hash value of a password and go backwards to determine the password. Ahh but what you could do is hash the password 123456, and then compare the hash value you just generated to a hash value of a user’s password. If the hash values match then boom you know the user’s password is 123456. So devious attackers have taken these giant dictionaries of the most common passwords in the world, and then for each password they pre-computed the hash value. This is a rainbow table, a giant database of the most common passwords and their associated hash values. You can no doubt see how rainbow tables would help an attacker. How do we defeat rainbow tables? Salt & Pepper. I created a video on Salt & Pepper which I’ve linked to.
Birthday Attack
Birthday attacks exploit the mathematics behind the birthday paradox in probability theory. You should associate birthday attacks with finding collisions in hashing algorithms.
Social Engineering
And the final, truly excellent way of attacking a cryptosystem is by targeting the weakest link in any system: people.
Purchase Key
Often the easiest way to figure out some super secure key is to bribe someone. Thus, the purchase key attack
Rubber Hose
Or if the carrot approach doesn’t work, move on to the stick, and torture someone. That is rubber hose cryptanalysis – your torture someone.

And on that super cheery note, we have now reached the end of our review of cryptography. We still have one more video in Domain 3 which is focused on physical security.
If you haven’t happened upon them already, we have a free series of practice question videos here on our YouTube channel. By going through example questions, we teach you how to best read a question, pick out the keywords, understand what the question is asking you and thus be able to find the best answer to the question.
Link to the practice videos is in the description below.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
