Vulnerability Assessment and Penetration Testing MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to Vulnerability Assessment and Penetration Testing in Domain 6, to understand how they interrelate, and to guide your studies
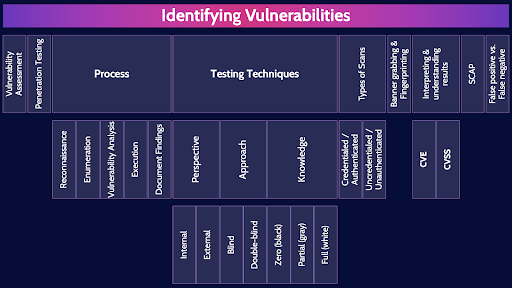
This is the second of three mind map videos for domain 6. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass.
Every system has vulnerabilities. Vulnerability assessment and penetration testing are an important part of testing a system to look for these vulnerabilities: to identify, classify and prioritize remediation.
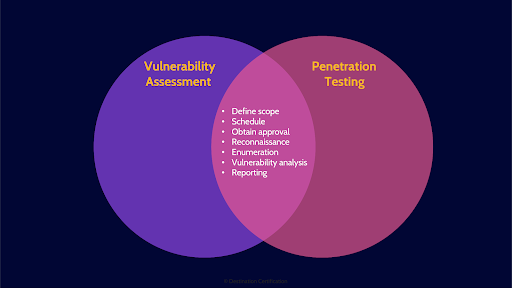
Vulnerability assessments and penetration tests are very similar and start out the same way – identifying potential vulnerabilities and reporting on them to understanding the potential impact to the organization and prioritize remediation.
Vulnerability Assessment
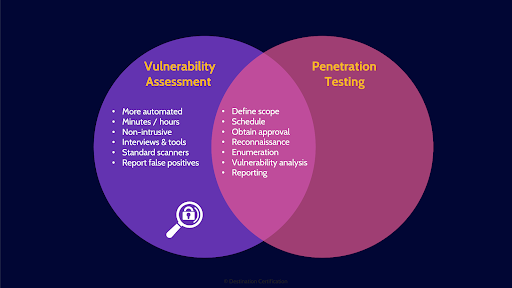
In a vulnerability assessment once a potential vulnerability has been identified, we skip straight to reporting.
Penetration Test
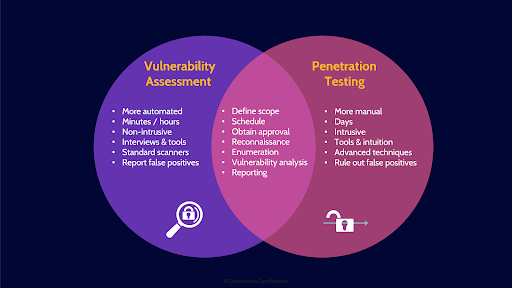
In a penetration test we identify potential vulnerabilities, and then we attempt to exploit them. To verify if the vulnerability truly exists and can be exploited, and thus eliminating false positives. Vulnerability assessments tend to be faster and more automated but generate far more false positives. Penetration tests are slower and more manual, and have a much higher likelihood of negatively impacting a system, but they provide a much clearer picture of the security of a system.
Process
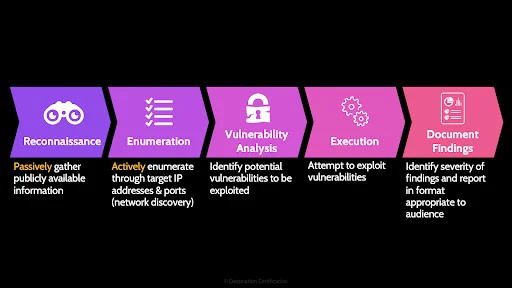
Here is the process we go through to conduct vulnerability assessments and pen tests
Reconnaissance
We start with reconnaissance, which is a passive activity, the organization being assessed cannot detect anything at this step because the assessor is gathering publicly available information from sources like job postings, linkedIn profiles, and DNS records.
Enumeration
Enumeration is ACTIVE, this step can potentially be detected by the organization. We are enumerating, systematically walking through, IP address ranges and ports to look for live systems that are offering services.
Vulnerability Analysis
Vulnerability analysis is where we determine the exact version of a system and identify potential vulnerabilities that could be exploited. We will talk about how banner grabbing, and fingerprinting can be used to identify the version of a system in a few minutes.
Execution
If we are performing a vulnerability assessment, then we skip execution and go straight to reporting. In a pen test however, the execution step is where we attempt to exploit any vulnerabilities we have identified. Actually break-in to a system.
Document Findings
And documenting findings is all about reporting on vulnerabilities identified, the potential impact to the organization and prioritization, and tailoring reports to various audiences.
Testing Techniques
Now let’s go through some testing techniques we can use. We can mix and match these different techniques to achieve different types of tests. We can simulate an outside hacker, or a malicious insider as examples.
Perspective
Perspective is about where the ethical hacker is performing the test from.
Internal
Internal means the testing is performed from within the organization’s network. Simulating the attacker being inside the network.
External
External means the testing is performed from outside the organizations network. Simulating the attacker being outside the firewall, typically out on the internet.
Approach
There are a couple of major approaches we can use in conducting tests.
Blind
In a blind test, we give the ethical hacker very limited information on the system to be tested. Perhaps just an IP address. The ethical hacker is blind.
Double-blind
Double blinds means, not only do we not give the ethical hacker any information, we also don’t tell the organization’s security operations team that the hack is occurring. Double blind tests not only what the hacker can get into, but also how effectively the organization can detect and respond to the attack.
Knowledge
Knowledge is all about how much information is given to the ethical hacker
Zero (black)
In Zero knowledge or black-box testing, the tester is given zero knowledge on the system and must rely on publicly available information and whatever they can deduce. This simulates an outsider trying to break in. Zero knowledge and blind tests are the same thing.
Partial (gray)
In partial knowledge or gray-box testing, the tester is given the knowledge of a user, potentially even elevated privileges on the system, and some basic info on system and network architecture. This makes testing more efficient.
Full (white)
Full knowledge, White-box, open-box, clear-box testing is where the testers are given full access to source code, full credentials, and detailed architectural documentation. White box testing is much more focused on going through the source code in detail.
Types of Scans
There are a couple of different types of scans we can perform with vulnerability assessment tools like Nessus or Rapid7.
Credentialed / Authenticated
A credentialed or authenticated scan is where we give the scanning tool the credentials necessary to log into the system or systems being scanned. A credentialed scan can take a deeper look into the exact configuration of a system and thus help eliminate false positives and also help with baseline compliance.
Uncredentialed / Unauthenticated
An uncredentialed scan, as you can probably guess, means we don’t give the scanning tool the credentials necessary to login. This is more a simulation of an external attacker and what vulnerabilities can be identified from the outside.
Banner grabbing & Fingerprinting
A critical requirement in identifying vulnerabilities is knowing the exact version of an operating system and application. Different versions of software are vulnerable to different things. Banner grabbing is where we intentionally get the system to generate something like an error message, like say an error 404 file not found on a web server, and looking at the error message to see if the version number of the system is listed. Systems should be configured not to show this information.
Fingerprinting is far more subtle. By either passively monitoring network traffic going to a system, or actively sending a few specially crafted packets, we can carefully evaluate the exact structure and the contents of packets. Different versions of systems will craft packets in subtly different ways allowing us to fingerprint the exact version.
Interpreting & understanding results
When reporting on vulnerabilities there are a couple of different important numbers that should be included.
CVE
The CVE or Common Vulnerabilities and Exposures number is a unique identifier for each vulnerability and a public database of all these vulnerabilities is maintained. Each vulnerability that has been discovered has a unique CVE number assigned to it.
CVSS
The CVSS or Common Vulnerability Scoring System is a standard for assessing the severity of a vulnerability from a zero which means meh all the way up to 10 which means everyone should be running around screaming.
SCAP
SCAP - The Security Content Automation Protocol - is a whole bunch of Interoperable specifications to help organizations automate vulnerability management and policy compliance evaluation.
False positive vs. False negative
Finally, false positives and false negatives are important challenges we need to deal with. A false positive is where we identify a potential vulnerability and upon further investigation, we realize there is no vulnerability – so we have spent some time chasing something that wasn’t there. False negatives are far worse. This is where a vulnerability exists, and we don’t identify it. We are blind to the vulnerability.

And that is an overview of Vulnerability Assessments and Penetration Testing within Domain 6, covering the most critical concepts you need to know for the exam.
Like these MindMap summary videos? Our CISSP MasterClass delves into all the details.
You can learn more about our CISSP MasterClass here: destcert.com/CISSP
Link in the description below as well.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
