Networking MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to Networking in Domain 4, to understand how they interrelate, and to guide your studies.
This is the second of four videos for domain 4. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass.
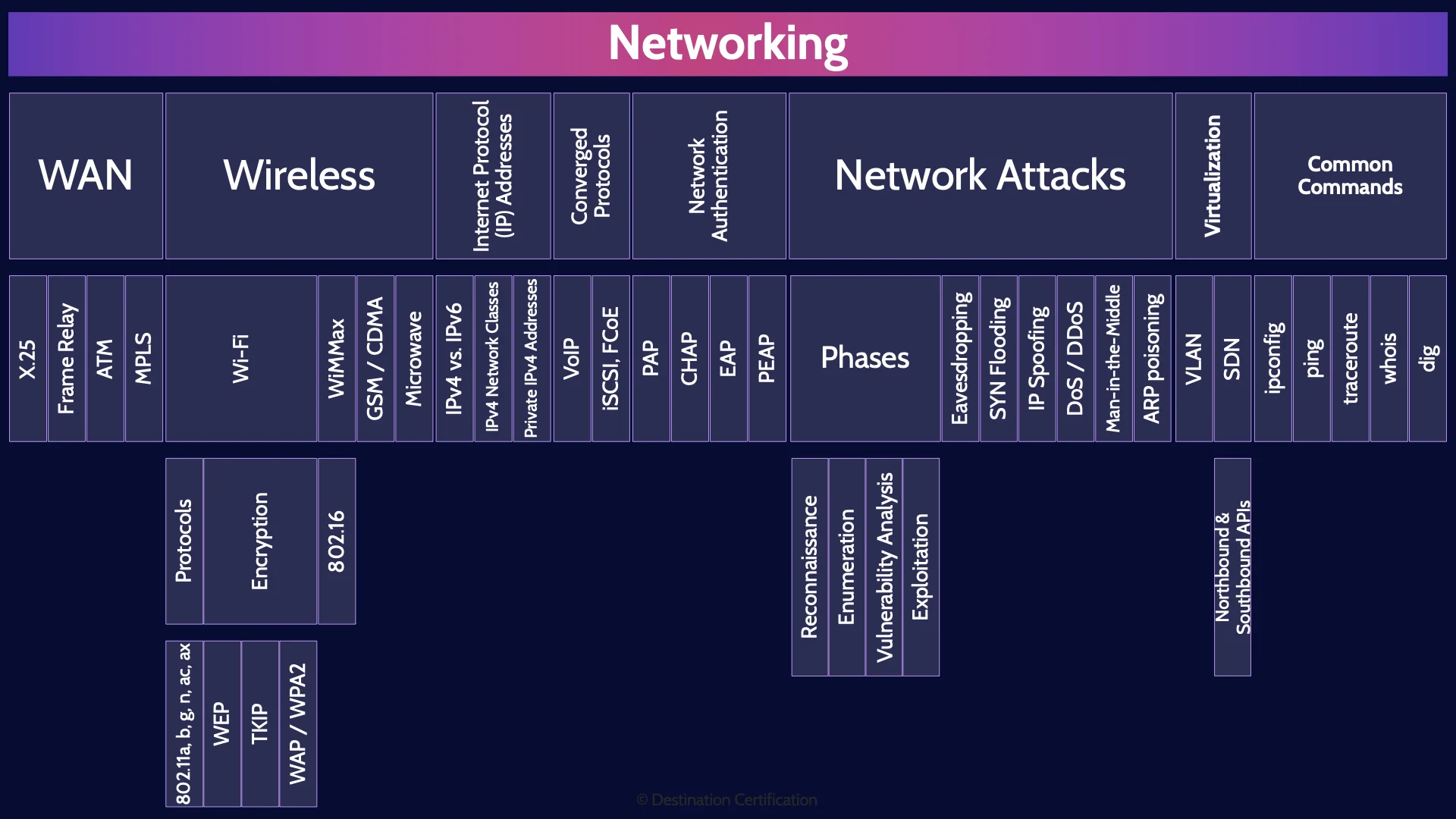
Networking
Continuing our discussion from the OSI model in the previous video, we are now going to dig into a bit more detail around networking concepts such as wide area networks, wireless, IP addressing, authentication, network attacks, virtualization and some common tools.
WAN
And we’ll start with Wide Area Networks – networks that are spread over a large geographical area, an entire country, continent or world. There are a few protocols that have been created over the years to enable wide area networks that you should know about:
X.25
X.25 was one of the first protocol suites for packet-switched networks across a WAN. X.25 was first published back in 1976, meaning it came out before IPv4 and the OSI Model.
Frame Relay
Frame Relay mostly replaced X.25
ATM
ATM - Asynchronous Transfer Mode – then mostly replaced Frame Relay
MPLS
And MPLS - Multiprotocol Label Switching – which can encapsulate various protocols including Frame Relay & ATM, has become the dominant wide area network protocol today.
Wireless
Now on to wireless. We are relentlessly marching towards our wireless future.

Can you even remember the last time you used a phone that was plugged into your wall and used a landline to call someone?

Remember when our computers used to have this plethora of ports on them? Look at all the stuff you could plug in!

Now you get this. And you should count yourself as lucky there is still a headphone jack there.
Nowadays, It’s either go wireless with everything…

Or welcome to dongle hell.
Wireless
One of the biggest challenges with wireless is that signals are much more easily intercepted.

Instead of having to physically break into a building to connect to the corporate network you can now just sit in the parking lot in your van and hack the planet.
Encrypting wireless traffic is, therefore, extremely important.
So, let’s talk about some of the various wireless technologies that we use every day and the security challenges associated with them.
Wi-Fi
We’ll start with Wi-Fi – a technology which we pervasively use to create local area networks without any wires. Well, you still need to plug your Wi-Fi access point into a physical network, but let’s not get pedantic here.
Protocols
IEEE - the Institute of Electrical and Electronics Engineers – 802.11 is the protocol we use for wireless local area networks. There have been many generations of 802.11 ratified over the last 20+ years.
802.11a, b, g, n, ac
You should recognize the following 802.11 standards: 802.11a, 802.11b, g, n, ac & ax. These different versions of 802.11 represent the evolution of the standard towards ever greater bandwidth and capabilities.
Encryption
As I mentioned it is critically important to encrypt wireless traffic as it is so much easier to eavesdrop on a wireless network.
WEP
One of the first wireless encryption protocols created was WEP – Wired Equivalent Privacy. WEP absolutely does not live up to its name. Very significant flaws have been found in the WEP algorithm related to how it implements the RC4 encryption algorithm to encrypt wireless traffic. Specifically, the Initialization Vectors used are far too short meaning that WEP encryption can be easily broken. As such WEP should never be used. This was a huge problem when it was first discovered, and a band-aid solution needed to be quickly found to prop-up WEP until new wireless encryption protocols could be created and ratified.
TKIP
The Band-Aid that was created for WEP was TKIP - Temporal Key Integrity Protocol. TKIP has subsequently been found to also have significant flaws and should therefore not be used.
WPA / WPA2
WPA - Wi-Fi Protected Access – was also meant as an interim protocol to help deal with the WEP fiasco until the next much better protocol, WPA2, could be ratified. WPA used TKIP for encryption by default.
WPA2 uses the AES encryption algorithm by default and AES is much better than TKIP.
WiMAX
Wi-FI is used for creating Local Area Networks with a range of about 100 meters. WiMax - Wireless Interoperability for Microwave Access – is a protocol for creating wireless Metropolitan Area Networks - Wireless networks with ranges of up to 90 kilometers.
802.16
The IEEE standard behind WiMax is 802.16
GSM / CDMA
Now let’s talk about a couple protocols used for mobile phones. GSM - Global System for Mobiles – and CDMA - Code Division Multiple Access – are wireless radio protocols used by cellular companies to provide 2G & 3G voice and data services.
GSM has a couple of significant security issues that are worth noting: it is vulnerable to man-in-the-middle attacks. An attacker can create a rogue cell tower which phones will connect to, allowing the attacker to intercept communications. It is also possible to clone SIM (Subscriber Identity Module) cards by extracting a user’s IMSI (International Mobile Subscriber Identity) allowing an attacker to make calls and receive calls and also receive a user’s SMS messages. This SMS cloning attack can be done over the air.
GSM & CDMA have largely been replaced by 4G / LTE and now of course 5G networks have become prevalent.
Microwave
Microwaves are not just for unevenly heating your hot pockets.
Microwaves are also a good way of cost effectively creating data links between buildings that are a few miles apart.
Internet Protocol (IP) Addresses
Now let’s talk about the major way that we ensure data sent across a network gets to the intended destination. IP - Internet Protocol - addresses. As I mentioned in the previous video, it is useful to think of IP addresses as being similar to a post address for a house. If you want to send someone a letter through the mail, you need their address, and that address needs to be unique to them. IP Addresses serve the same function on a network.
IPv4 vs. IPv6
The pervasively used version of IP currently is v4. It’s worked great for decades, but there are some big limitations.

The address space, the total number of unique IP addresses, is only 2 to the power of 32, or 4 billion,294 million, 967 thousand, and 296 possible addresses. When IPv4 was first ratified back in 1974 - and there was no internet - 4.3 billion addresses probably sounded like such an absurdly large number that we would never run out. But here we are in 2020 with about 7.8 billion people on the planet, and many of us using multiple IP addresses. I just checked: I’m using 67 IP addresses on my little home network. Crazy. Granted, I am a wee bit of a nerd. The point stands though: 4.3 billion IP addresses are not nearly enough. Plus, IPv4 has no security built-in by default.
Enter IPv6. IPv6 addresses both the problems just mentioned with IPv4. The address space for IPv6 is 2 to the power of 128, or 340 undecillion possible addresses.

That’s this number here.

Actually it’s not. 340 undecillion is actually this number here. It’s a very very large number. We should be good for at least a couple more years with this many addresses. Once the internet manages to switch over to IPv6 that is.
Another big advantage of IPv6 is that capabilities for encryption and integrity checking are built right in, whereas with IPv4 we had to duct tape these capabilities on later.
IPv4 Network Classes
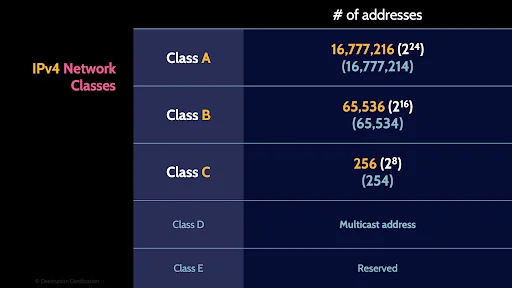
The IPv4 addressing system is divided into five classes of IP addresses. You don’t need to be able to calculate subnet masks but you should be able to recognize these 5 classes and the number of addresses in each class.
Class A network provide 2 to the power of 24 addresses: 16 million 777 thousand, and 214 useable addresses.
Class B provides 2 to the power of 16 addresses: 65 thousand, 534 useable addresses.
And Class C provides 2 to the power of 8 addresses: 254 useable addresses.
Private IPv4 Addresses
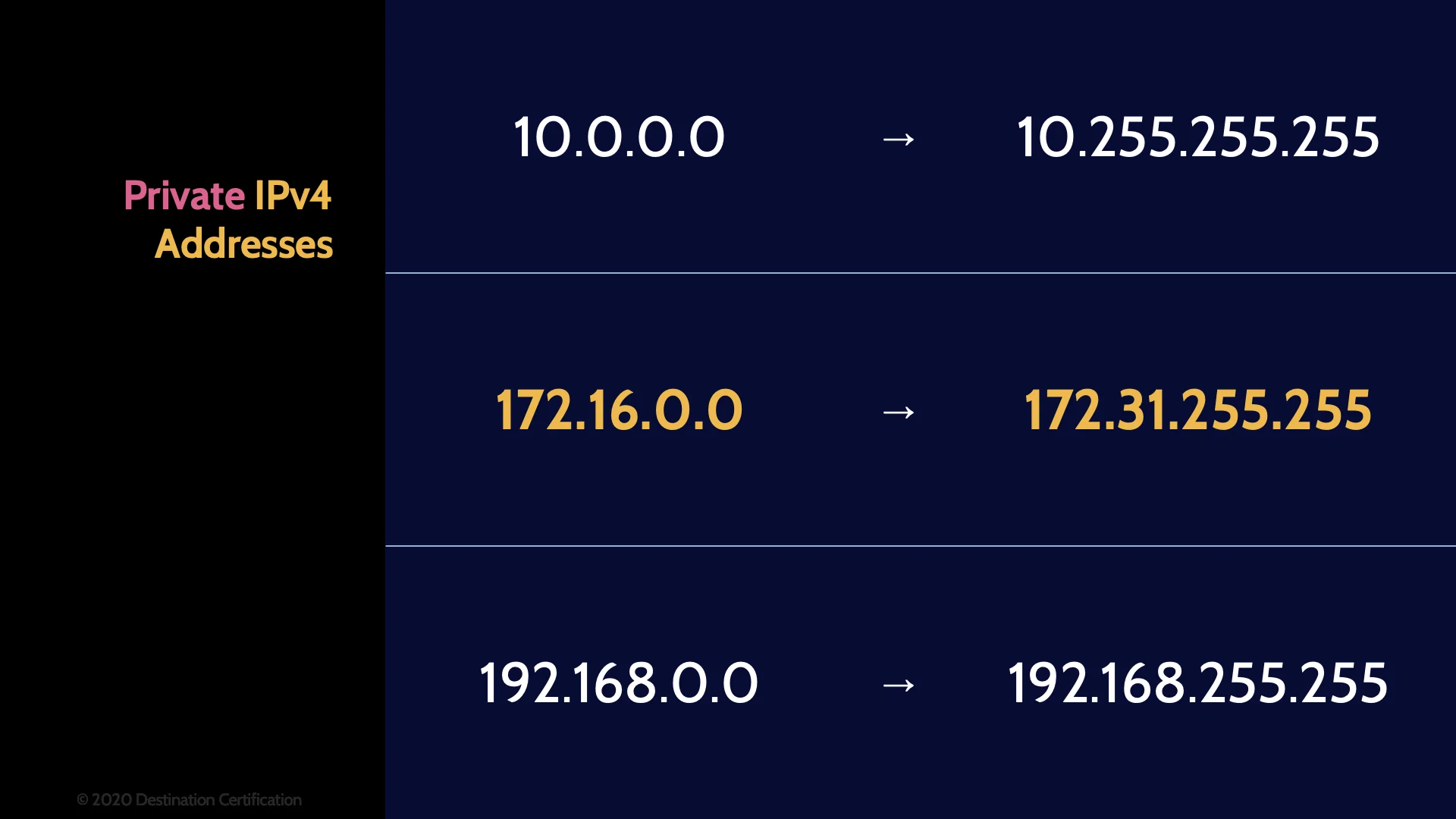
The final piece you should remember related to IPv4 addresses is that 3 ranges of addresses have been reserved for use in private networks (home networks, corporate networks, etc.).
- The 10. range
- The 172.16 to 172.31 range
- And the 192.168 range
Any of the private IP addresses in the 3 ranges above are NOT routable on the internet.
Converged Protocols
All sorts of specialty networks have been developed over the years, the plain old telephone system, surveillance camera networks, storage area networks, etc. Many of these specialty networks have required proprietary protocols and specialized dedicated networks. The idea behind convergence is this: rather than having a completely separate network for all our security cameras, why not just plug them into our existing IP data network, or hey, rather than keeping this old dedicated phone network around, let’s just plug the phones in the IP data network. Converged protocols are taking these speciality or proprietary protocols and running the traffic across a standard TCP/IP network – thus eliminating the need for separate networks that can be expensive to maintain.
VoIP
VoIP – Voice over Internet Protocol is a perfect example of a converged protocol. You’re taking telephone voice data and sending it across TCP/IP local area networks and the internet.
iSCSI, FCoE
A couple of other converged protocols that you should be aware of are both related to storing and retrieving data across an IP network: iSCSI - Internet Small Computer Systems Interface and FCoE – Fibre Channel over Ethernet.
IP Address
And it is at layer 3 that we have the crucially important Internet Protocol (IP) Addresses. IP addresses are much like your postal address. If anyone wants to mail you a letter from somewhere on the planet, then they need your postal address: your country, province or state, city, street, and house number so that a letter can be routed to your specific mailbox. IP addresses serve the same function on networks. They identify a specific system and allow datagrams (packets) to be routed to the system across local area networks and even across the vast intertubes. Lots more on IP addresses in the next video.
Network Authentication
Something we need to do all the time on networks is authentication, for example authenticating a client to a server. Many authentication protocols have been created over the years, let’s go through a few key ones you should know for the exam:
PAP
Password Authentication Protocol – is one of the oldest authentication protocols and it's absolutely useless from a security perspective as both the username and password are sent in clear text / in plaintext. I need to find some good stock footage of a dumpster fire for when I talk about protocols like this.
CHAP
The Challenge Handshake Authentication Protocol – CHAP - sends the authentication data in plaintext but does so in a much cleverer way, and in fact it’s where the Challenge part comes from in the name of this protocol. The server generates a random string, a challenge, and sends it to the client. The client then feeds their password and the challenge into the MD5 hashing algorithm and sends the hash result to the server. The server can then confirm the user knows their password without the user sending their password across the network in plaintext. The hash value that the client generates can be sent in plaintext because as we discussed in domain 3, hashing is a one-way mathematical function and therefore a man-in-the-middle cannot determine the user’s password by intercepting the hash value. Like is said: Clever.
ICMP (Ping), IPSec, IGMP
ICMP - Internet Control Message Protocol - allows network devices to send error and control messages and enables the Ping & Traceroute utilities.
IPSec - Internet Protocol Security – is the bewildering suite of protocols that provide data authentication, integrity, and confidentiality. I’ll talk about the components of IPSec in video 4.
And IGMP - Internet Group Management Protocol – which is used by hosts and adjacent routers to establish multicast group memberships. IGMP enables multicast groups – the ability to transmit the same packets to multiple systems at once.
EAP
The Extensible Authentication Protocol was originally developed as an authentication protocol for the Point-to-Point Protocol (PPP), but EAP is widely used for authentication on wired LANs, wireless LANs, and even WiMAX. It is so widely used because it is extremely flexible and essentially provides a framework upon which all sorts of different authentication methods – EAP methods - can be used. A couple of EAP-Methods you should be familiar with:
- EAP-MD5 uses the MD5 hashing algorithm and is pretty limited. For example, it only allows server authentication
- EAP-TLS on the other hand is way more secure and enables dual authentication of both the server and the client through the use of certificates.
PEAP
And the final authentication protocol we’ll talk about isn’t actually a standalone authentication protocol, it’s just a wrapper for EAP. PEAP – Protected EAP – encapsulates EAP within an encrypted TLS – Transport Layer Security tunnel – thus encrypting any EAP traffic that is being sent across a network.
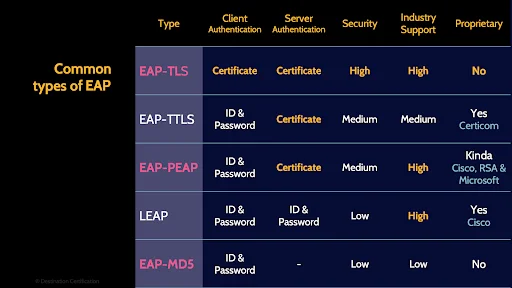
Here’s a table that summarizes a few of the important types of EAP.
Network Attacks
Let’s now shift gears and talk about some common types of network attacks and generally how network attacks are perpetrated.
Phases
There are 4 major phases to a network attack that you should be familiar with.
Reconnaissance
The defining characteristic of Reconnaissance is that it is a passive activity, the organization that is being attacked has no way of detecting the attack at this phase because only publicly available information is being gathered from sources like job postings, LinkedIn profiles, and DNS records.
Enumeration
Enumeration is where a network attack can begin to be detected because enumeration is an ACTIVE activity. The attacker is enumerating, systematically scanning through IP address ranges and ports to look for live systems that are offering services. The attacker is scanning for potential targets of attack.
Vulnerability Analysis
Vulnerability analysis is where the attacker tries to determine the exact version of a system and identify potential vulnerabilities that could be exploited.
Exploitation
And in the final step, exploitation, the attacker will attempt to exploit any vulnerabilities identified.
Eavesdropping
Now onto some of the common types of network attacks. As I mentioned in the previous domain 4 video, the prevailing network topology is bus, which means an attacker connected to the bus (connected to a wired or wireless network) can usually quite easily passively listen in and eavesdrop on network traffic. This is eavesdropping, passively listening to network traffic.
SYN Flooding
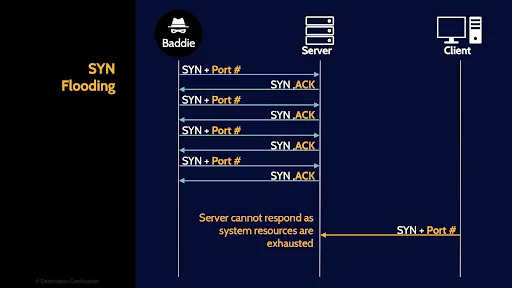
SYN Flooding is a form of denial-of-service attack in which an attacker sends a succession of SYN packets to a target systems in an attempt to consume enough resources such that the target system is unresponsive to legitimate traffic.
IP Spoofing
IP Spoofing is where an attacker changes the source IP address of a packet to either hide the attacker’s identity or to match another IP address on the network, thus allowing the attacker to pretend (to spoof) to be another system.
DoS / DDoS
Denial of Service is any attack that negatively impacts the availability of the victim system such that authorized users cannot access the victim system for business purposes. A Distributed Denial of Service attack is simply a DoS attack that originates from multiple attacking systems, possibly thousands, hundreds of thousands, or even millions of attacking systems focusing on making one target unavailable.
Man-in-the-Middle
Man-in-the-middle attacks are where an attacker places themselves in the middle of computers which are communicating with each other such that the attacker can intercept or even modify the communications between the systems.
ARP poisoning
And finally Address Resolution Protocol Poisoning is where an attacker modifies an Address Resolution Protocol (ARP) table, often their own ARP table, such that the router reads the update and begins redirecting traffic to a new destination. For example, an ARP poisoning attack could cause traffic destined for the victim to actually be sent to the attacker instead – this is a way of establishing a man-in-the-middle attack.
Virtualization
Next up let’s talk about how we can use virtualization to logically segment our networks, and with SDN – achieve some really cool security benefits.
VLAN
VLANs – Virtual Local Area Networks – allows you to logically segment a network. Put another way you can segment a network through software instead of having to physically segment a network by buying and configuring new network hardware. A VLAN can comprise a subset of the ports on a single switch or subsets of ports on multiple switches thus allowing systems to be logically separated / segmented into groups. Network segmentation has a lot of security benefits and VLANs can be a good way of achieving segmentation efficiently and economically.
SDN
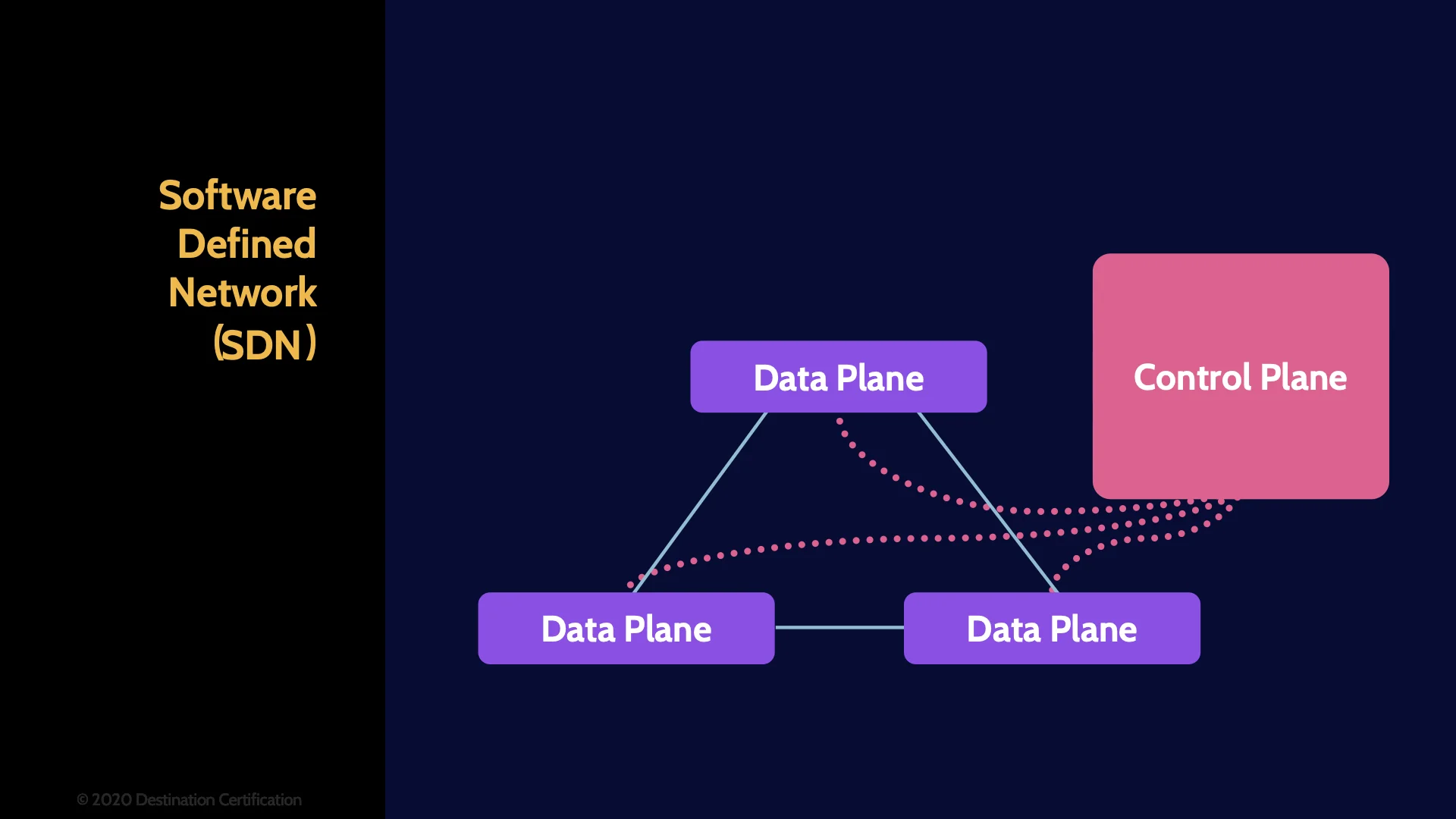
Software Defined Networks are a massive leap forward in virtualization beyond just simple VLANs. An SDN allows you to create multiple completely virtualized, software-controlled networks, on top of a physical network. SDNs provide far greater flexibility to reconfigure a network rapidly by centralizing all the control of the virtualized network. SDNs are a critical part of what makes the cloud work. Fundamentally, SDN provides abstraction for network topology, network flow, and network protocols.
Northbound & Southbound APIs
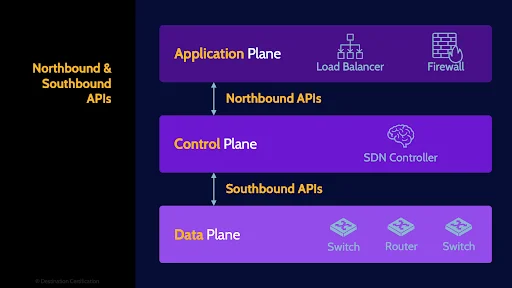
Software Defined Networks are a massive leap forward in virtualization beyond just simple VLANs. An SDN allows you to create multiple completely virtualized, software-controlled networks, on top of a physical network. SDNs provide far greater flexibility to reconfigure a network rapidly by centralizing all the control of the virtualized network. SDNs are a critical part of what makes the cloud work. Fundamentally, SDN provides abstraction for network topology, network flow, and network protocols.
Common Commands
Okay, final section in this MindMap, a very brief overview of some of the most common network tools we use to manage and maintain networks:
Ipconfig
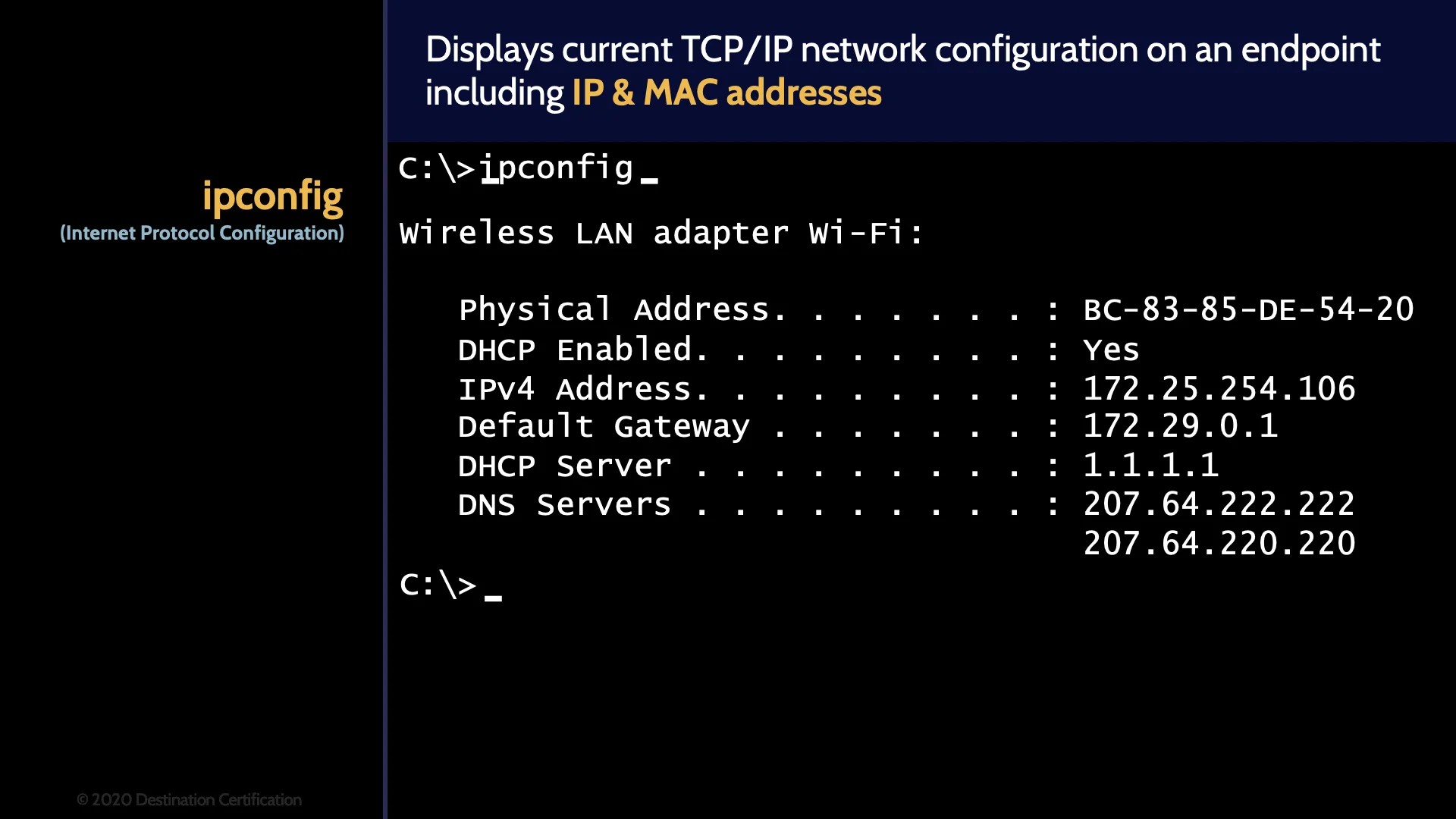
Ipconfig displays current TCP/IP network configuration on an endpoint – for example a computer - providing the IP & MAC addresses of any Network Interface Cards in the system plus the gateway, DHCP and DNS IP addresses.
Ping
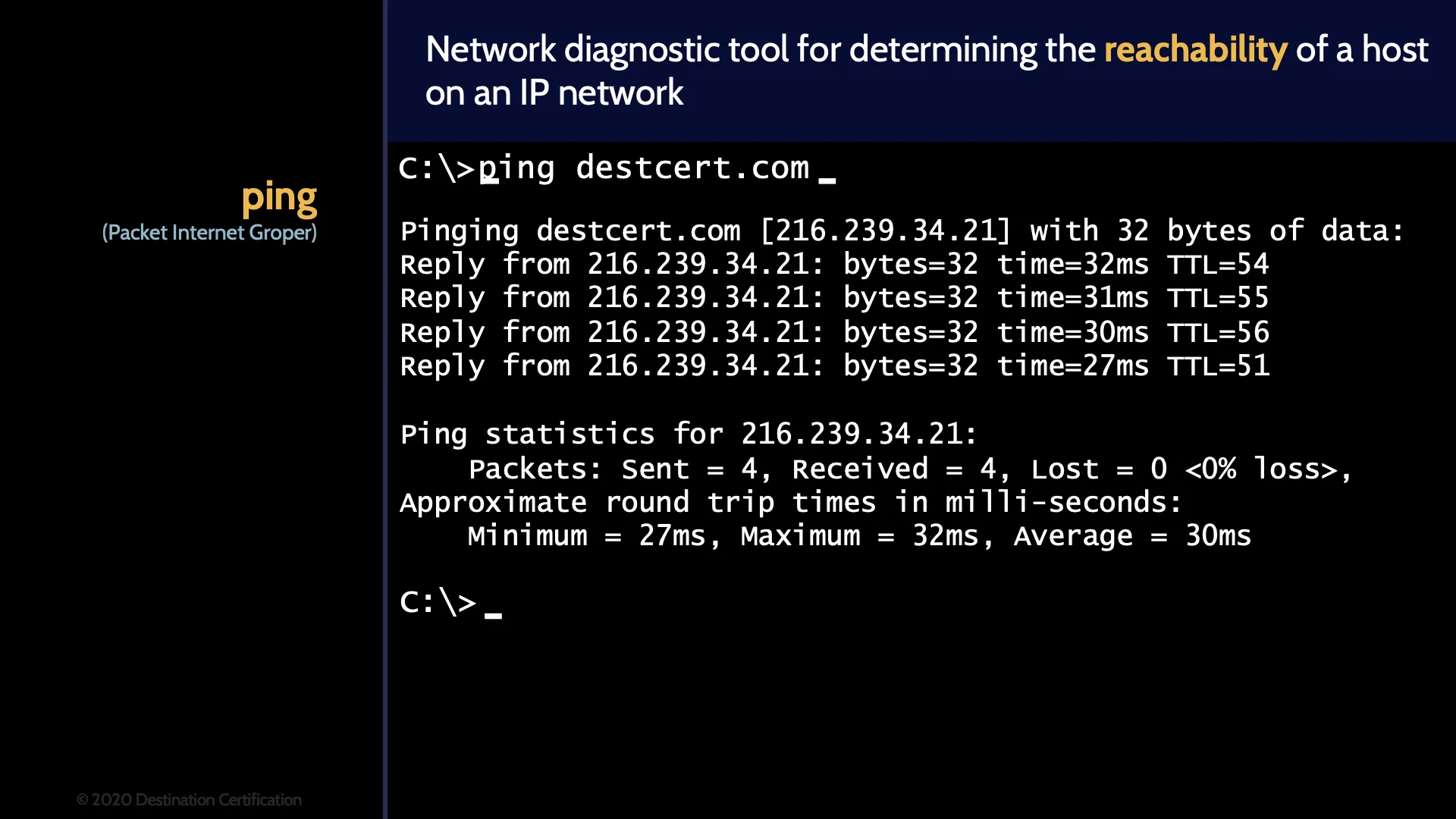
Ping is used to determine the reachability of a host on an IP network. Ping is commonly used to see if a system is online and responding.
Traceroute
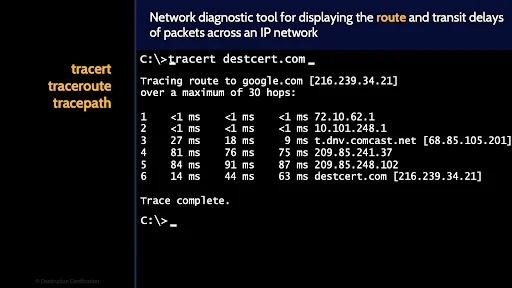
Ping is used to determine the reachability of a host on an IP network. Ping is commonly used to see if a system is online and responding.
whois
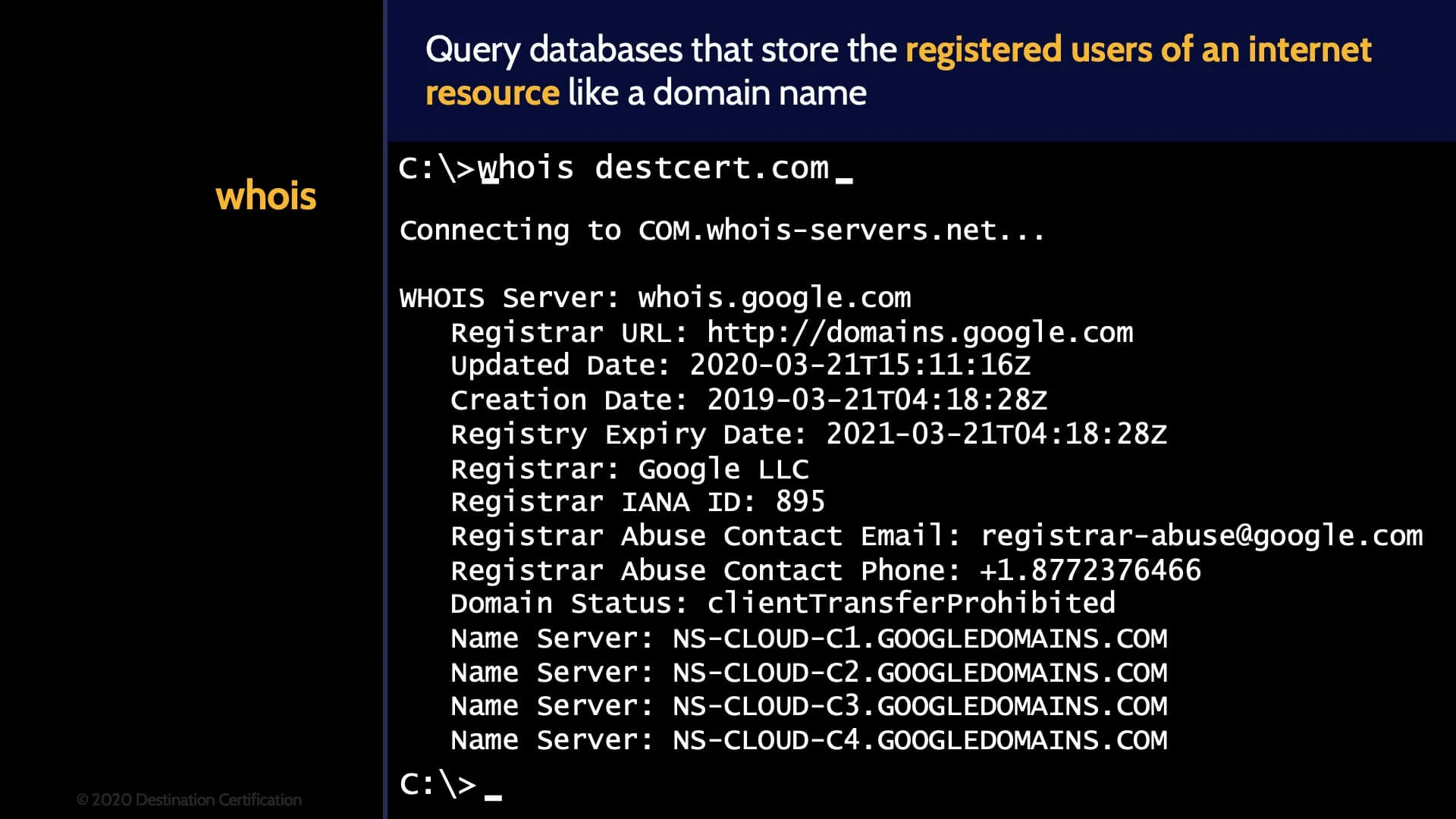
Whois is used to query databases that store the registered users of an internet resource like a domain name. You can use whois to find out who is the owner of a domain name.
dig
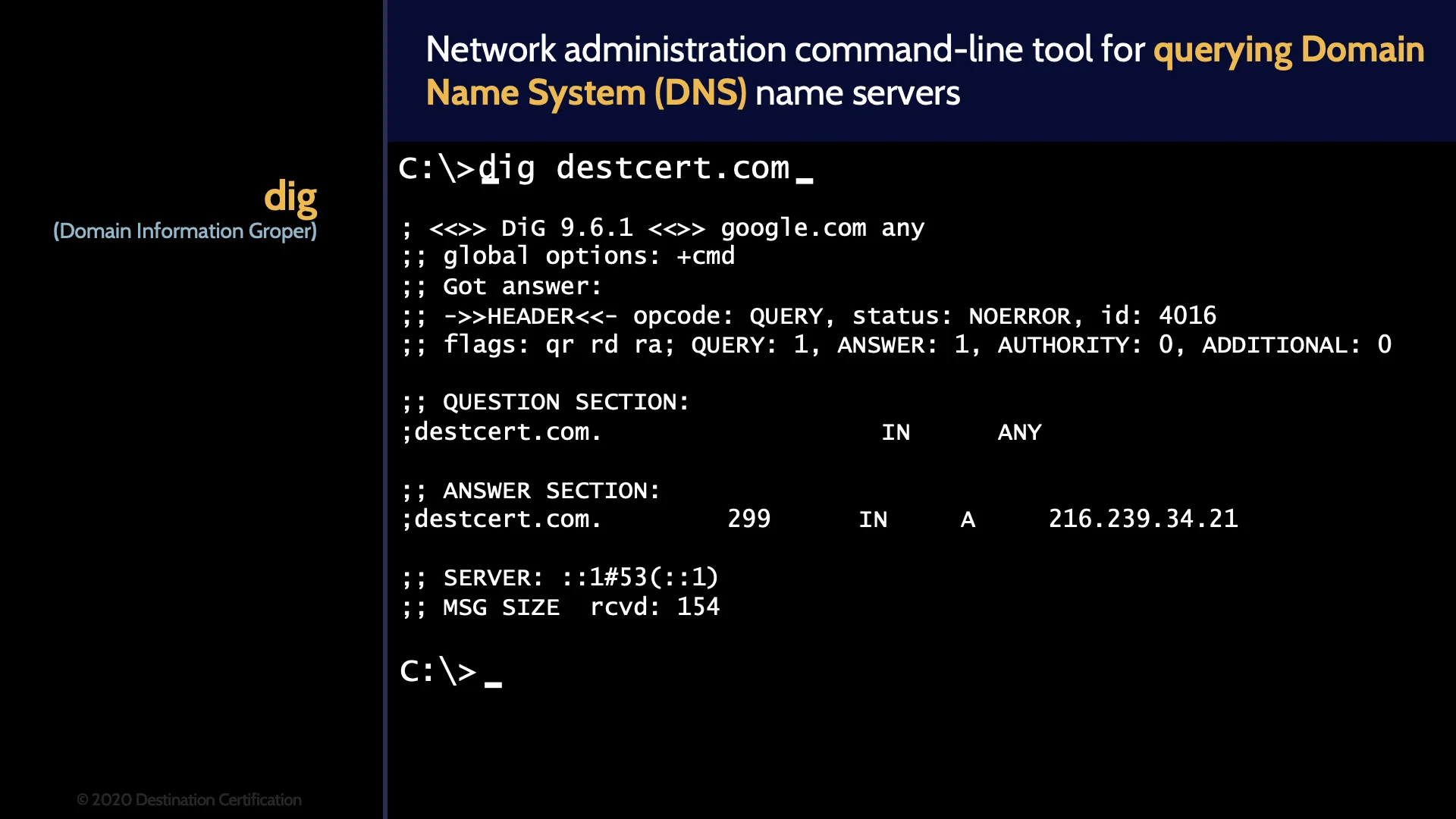
And dig is used to query DNS – domain name systems – to get all the details on a domain name such as the name servers the domain name uses, the mail server, etc.

And that is an overview of Networking within Domain 4, covering the most critical concepts you need to know for the exam.
Hey have you downloaded our FREE OSI model cheat sheet yet? If not, why not? It makes it super easy for you to memorize the critical protocols I just covered in this MindMap.
Link to download this FREE PDF is in the description below.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
