Network Defense MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to network defense in Domain 4, to understand how they interrelate, and to guide your studies.
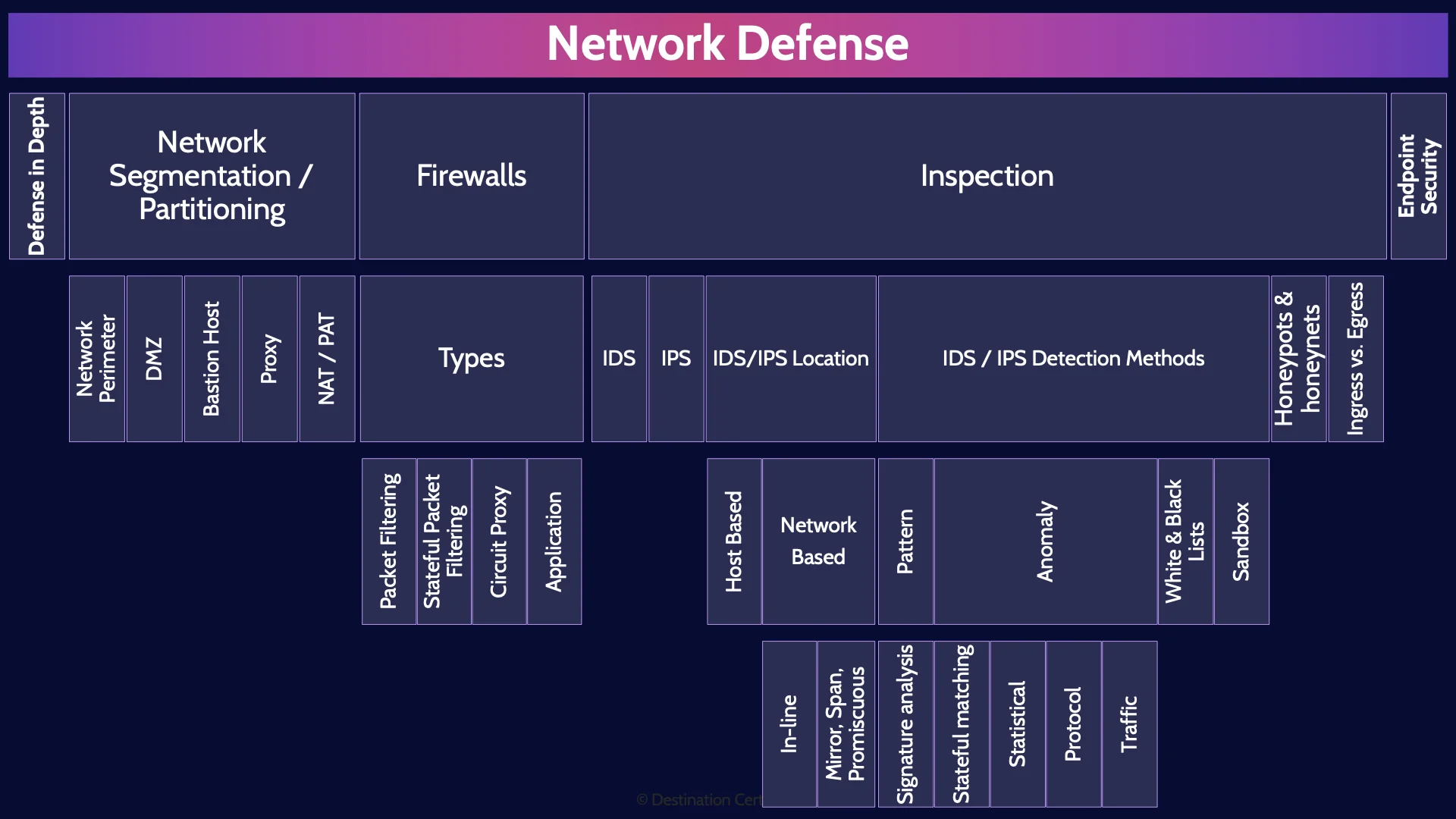
This is the third of four videos for domain 4. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass.
Network Defense
It is incredibly rare to come across a system nowadays that isn’t connected to a network and to the largest hive of villainy and scum in the world – the internet.
There is huge value in interconnecting our servers, laptops, mobile devices, smart watches, light bulbs, coffee machines, cars, and nuclear reactors.
There is also huge risk.
In this MindMap we are going to talk about some of the major tools and techniques we can use to protect our networks.
Defense in Depth
An important concept we use throughout security, and definitely need to apply to protecting networks, is defense in depth.
We want multiple layers of controls such that if one control fails our crown jewels, our valuable assets, are not exposed.
Defense in depth means that at each layer of defense we need a combination of preventive, detective and corrective controls at a minimum.
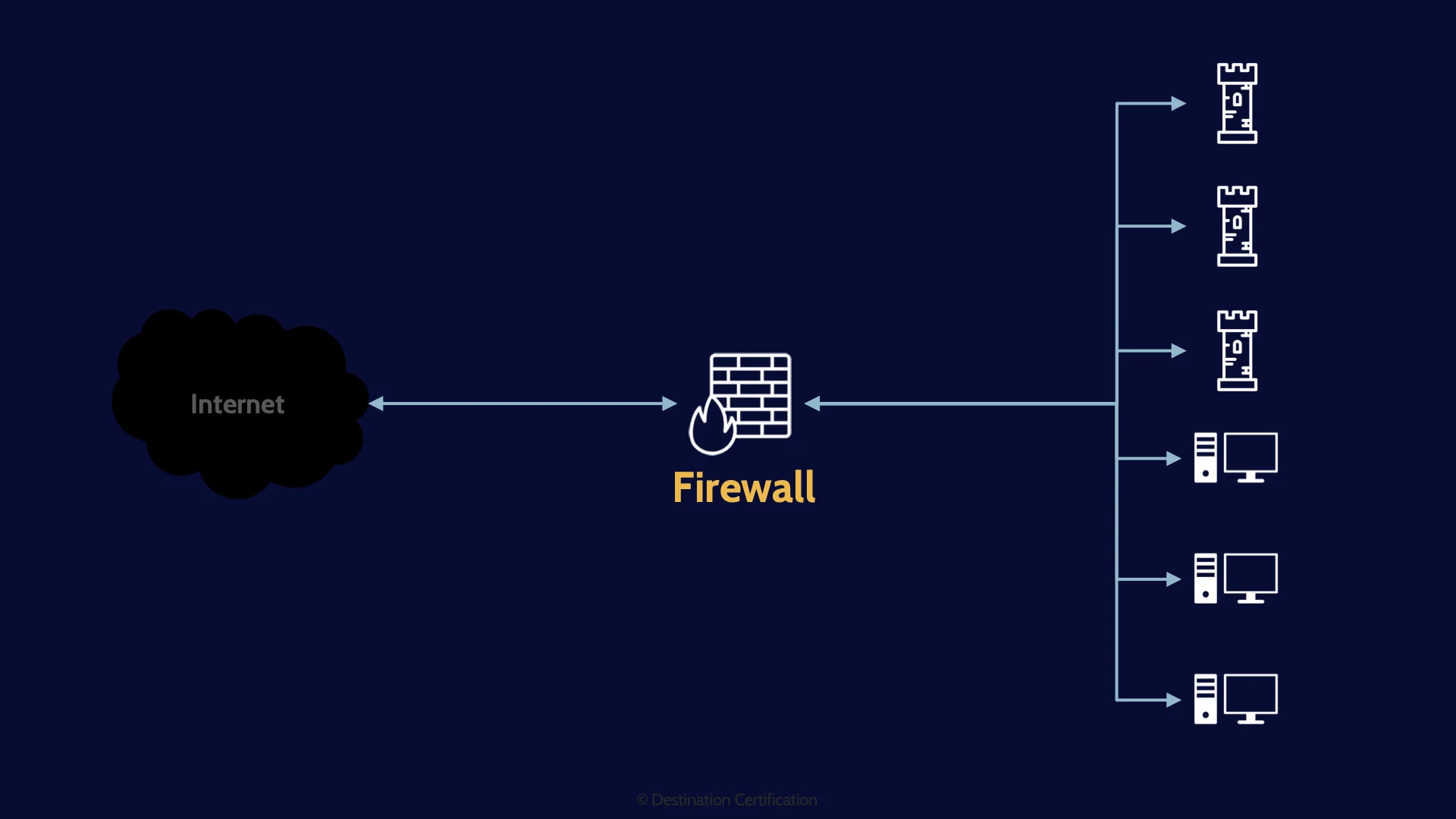
For example, instead of having just a firewall between the super sketchy internet and all our systems, including those that are internet facing like web servers, mail servers, and FTP servers
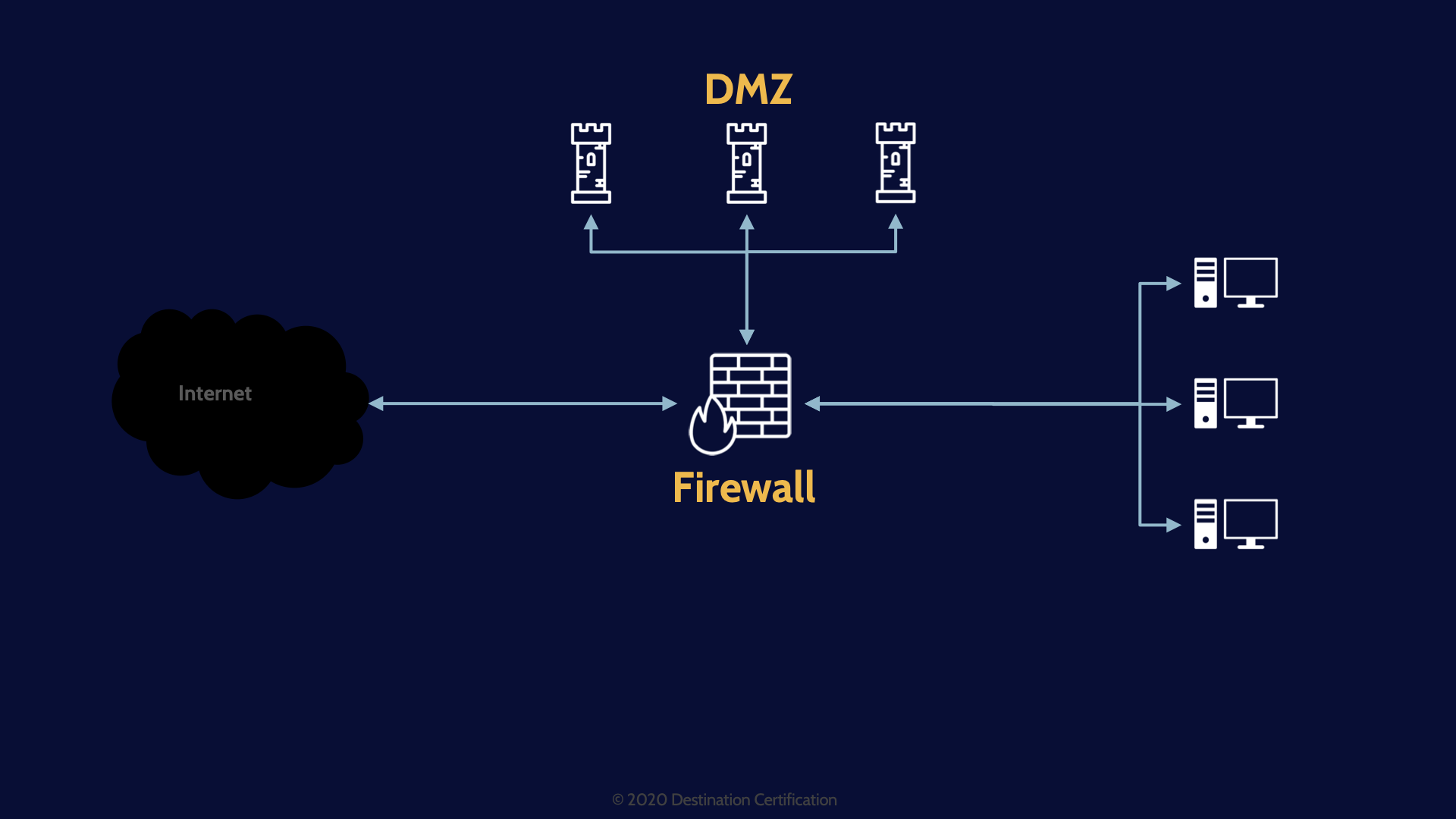
We could implement some network segmentation and move the web, mail and FTP servers into a dedicated network segment – a DMZ.
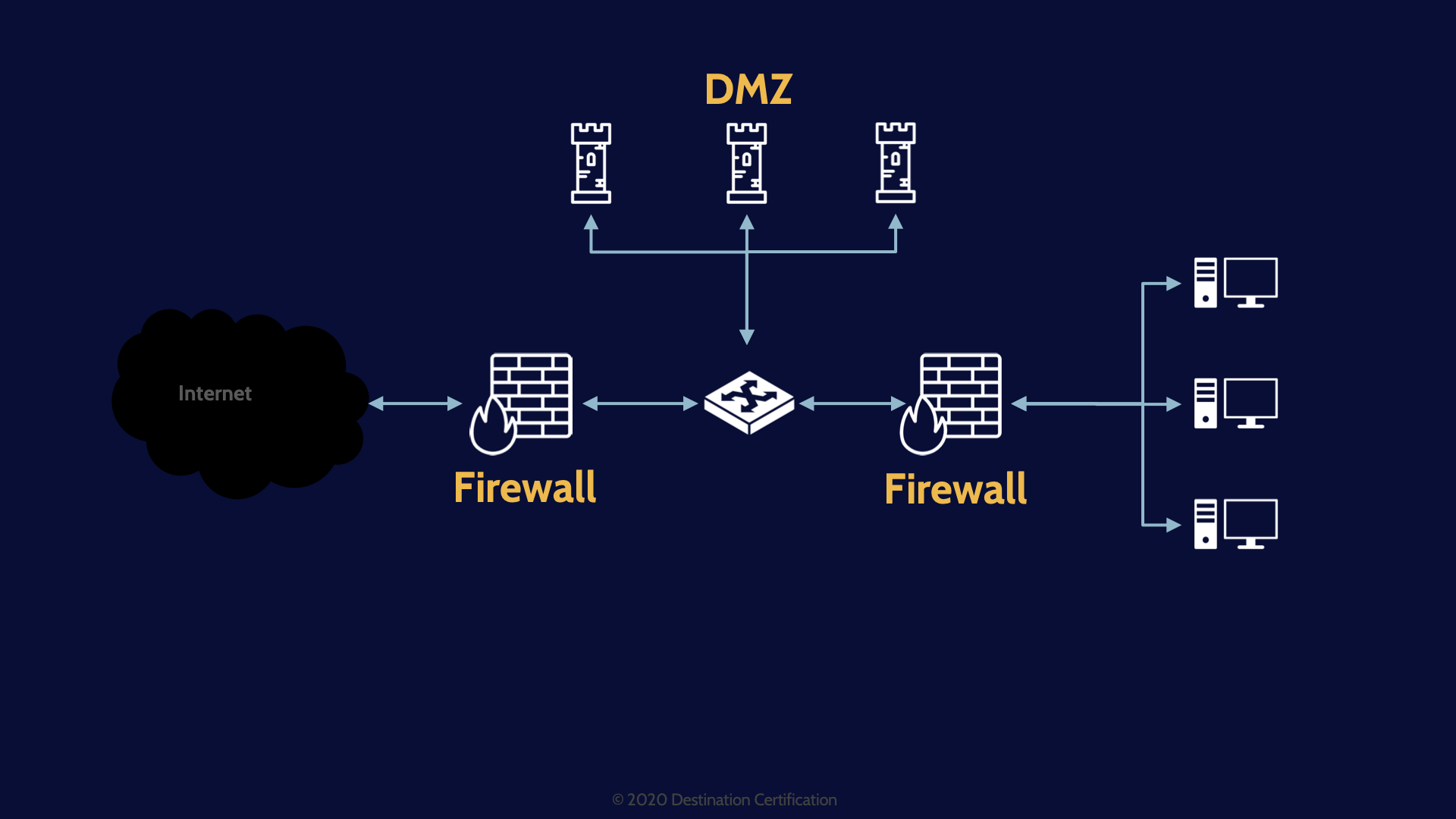
And we could further implement a screened subnet architecture with the addition of a second firewall and we could even make sure our second firewall is from a completely different firewall vendor.
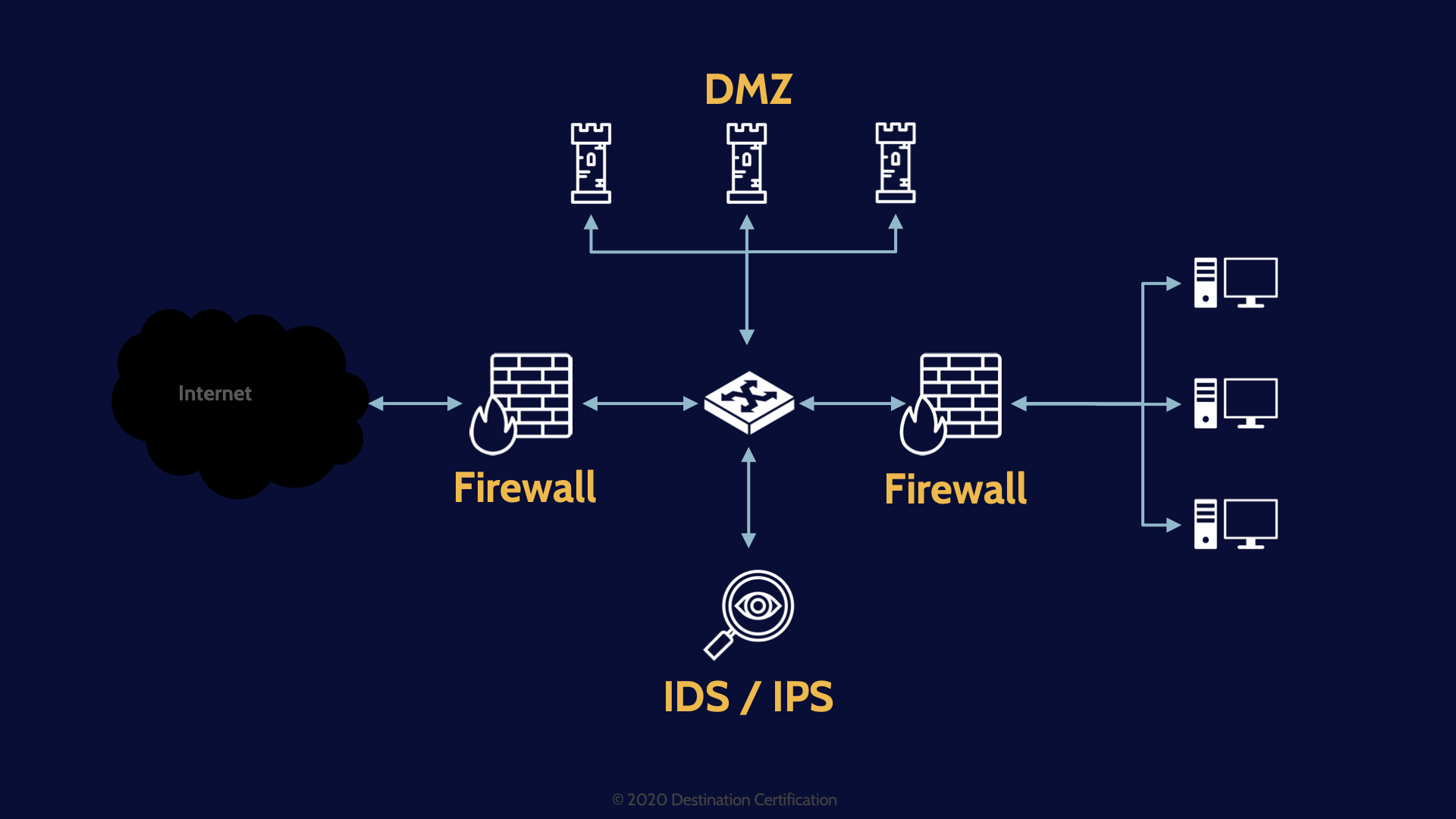
And moving beyond preventative controls we could implement IDS systems to provide a detective capability, or even an IPS to provide both detective and corrective capabilities.
There are lots of options for implementing defense in depth. And as usual all this cool expensive technology needs to be balanced against the value of the assets you are protecting.
Controls must be cost effective.
Network Segmentation / Partitioning
Let’s get into the details of these controls I just blitzed through. Network segmentation, also referred as partitioning, is the idea that we break our networks up into pieces, segments, partitions and then we can control the flow of traffic between these segments. We can create different segments and apply differing levels of controls to these segments. One segment could be our guest network that we just allow out to the internet and we have very limited controls in place, another segment could contain our back-end, high-value, databases and we have extensive controls in place to prevent and detect unauthorized access to the segment.
Network Perimeter
The largest segmentation is going to be between an organization's internal network and the internet. You ideally want a clearly defined boundary between your internal network and the public facing side of your network and then control the flow of traffic between those two segments – typically with a firewall which we’ll get into.

A moment on my soapbox here: you should never use the concept of an internal TRUSTED network.

You must always assume that the baddies are inside your network. There is no trusted network. Zero Trust.
DMZ
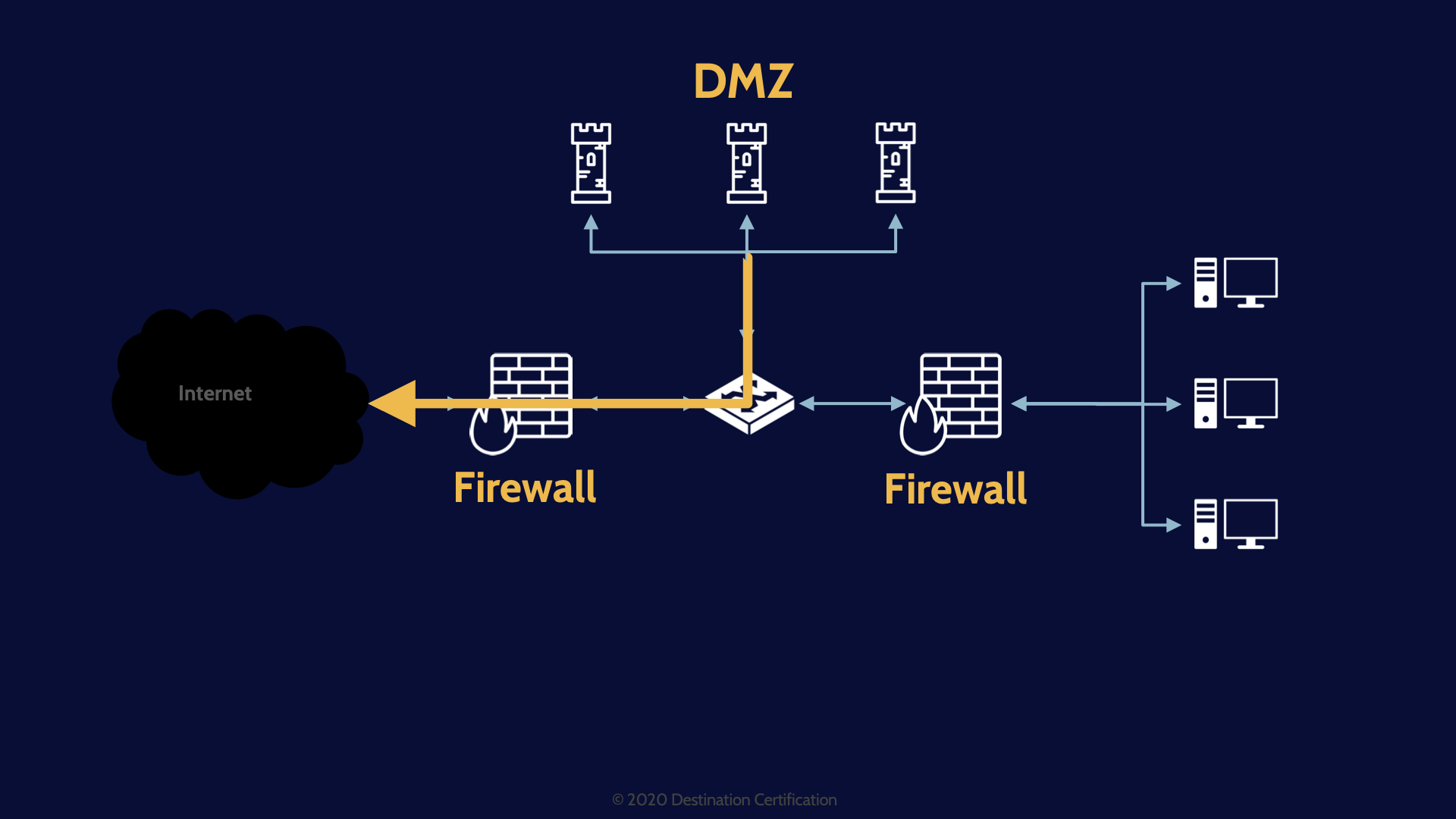
DMZ – Stands for Demilitarized Zone. DMZs are a network segment where we place our bastion hosts, our systems that are intentionally accessible by the public over the internet. Systems like web servers, mail servers and FTP servers. We fully expect these publicly facing systems will be attacked and if they are compromised and they are within a DMZ ,then the attacker does not have a foothold within our internal network. We severely restrict any traffic that can come from or DMZ into our internal network. The DMZ network segment is essentially just connected out to the internet.
Bastion Host
Bastion hosts, as I just mentioned, are Computers / servers that are specifically configured to withstand attacks. Bastion hosts are typically a public facing server like a web server.
Proxy
A proxy is a server located between two devices. A proxy acts as an intermediary such that all traffic between the devices must pass through the proxy. This allows the proxy to read, filter and control the communications and even hide the devices behind the proxy.
NAT / PAT
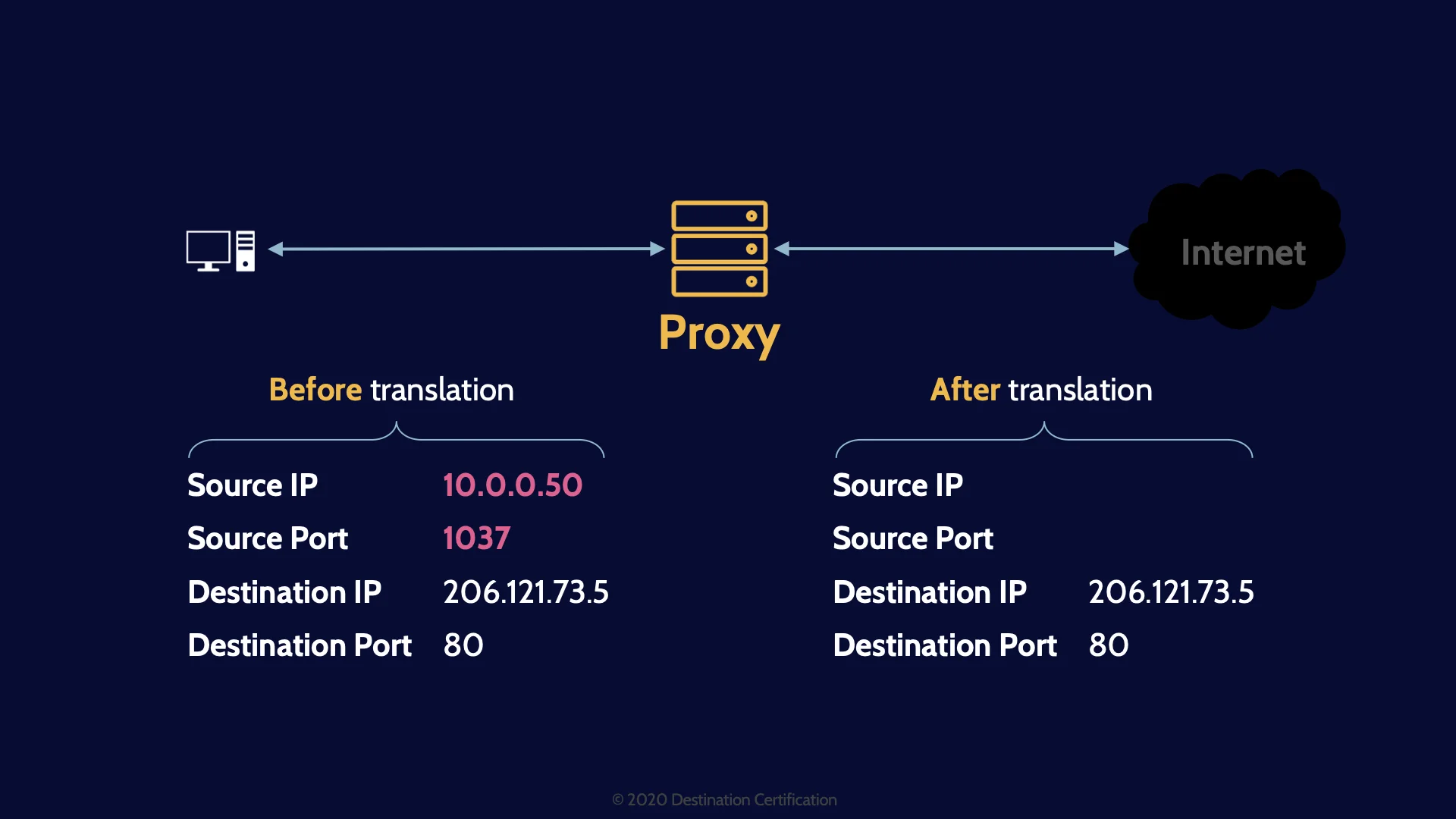
NAT and PAT are examples of proxies. NAT – Network Address Translation – is a method of remapping (swapping) an IP address to another by modifying the IP header of packets when they pass through a proxy. Typically remapping from an internal unrouteable IP address to a publicly routable address when a packet passes from inside the network out onto the internet.
And the proxy would remap any returning responses, changing the destination IP address on returning packets from the IP address of the proxy to some internal system’s IP address.
And PAT – Port Address Translation – is exactly the same idea except instead of changing the IP address, the port number is remapped.
Firewalls
Ok now on to one of the most fundamental tools in network security: Firewalls. At the most basic level, the job of a firewall is to control the flow of traffic between network segments. For instance, controlling what traffic from out on the sketchy internet is allowed through to the internal network.
Types
Firewalls have evolved significantly over the years and become a lot smarter about how they inspect traffic and make decisions on what traffic to allowed through.
Packet Filtering
We’ll start with the oldest simplest types of firewalls: Packet filtering firewalls. Packet filtering firewalls only inspect packet headers looking at the source and destination IP address & ports against a set of rules typically defined in an Access Control List (ACL). Packet filtering firewalls are not very smart, but they are extremely efficient and can make decisions very quickly meaning they have very low latency – they don’t slow down the flow of traffic much.
Stateful Packet Filtering
Stateful Packet Filtering firewalls still only look at a packet’s header, but they are a little more intelligent in that they maintain a state table – a little bit of memory that keeps a history of recent traffic through the firewall.
Here’s how the state table can be useful: when systems want to establish, say, a TCP connection, they must go through the TCP three-way handshake process of SYN, SYN / ACK, ACK.
The stateful Packet Filtering firewall will record that these two systems have completed the handshake and established a connection, and then if either system wants to send a packet to the other, the firewall will likely allow it because the firewall knows they have established a connection. But if another system were to send a TCP packet out of the blue the firewall is likely to block it because it has no memory of this system establishing a connection.
To simplify: if a Stateful Packet Filtering firewall sees a packet going out it will allow the reply to come back in, because it remembers the outgoing packet in its state table. Packet filtering and stateful packet filtering firewalls both operate at layer 3, the network layer.
Circuit Proxy
Circuit Proxy Firewalls operate at Layer 5 – the session layer. Circuit proxies therefore understand what is happening at the session layer and will allow a circuit, a session, to be established if it complies with predefined rules.
Application
And all the way at the top of the OSI model we have Application Firewalls which operate at Layer 7 the application layer. This means that application firewalls can do deep packet inspection, they can inspect anything in the packet header and reassemble a series of packets to inspect the contents of the data that is being sent in the packets. For instance, application firewalls can scan a file being sent to look for viruses.
Application firewalls are very intelligent and can make very sophisticated decisions. However, all this intelligence comes at the cost of speed. They are the slowest type of firewall, and cause the highest latency.
Most modern firewalls offer the capabilities of all the firewall types we just discussed. They can make quick and simple decisions by just looking at a packet header and if necessary, they can apply much more thorough analysis by inspecting the contents of packets. So you get the benefits of speed and intelligence where you want it.
Inspection
Moving on from firewalls we’ll now talk about the major network monitoring tools we use: IDS & IPS systems.
IDS
And we’ll start with some simple definitions. IDS – Intrusion Detection Systems – are designed to inspect network traffic – packets – to detect potentially suspicious activity. And if an IDS detects something suspicious it will raise an alarm.
IPS
IPS – Intrusion Prevention Systems – do exactly the same thing as an IDS – attempt to detect suspicious activity, but then go an important step further – if they detect something suspicious they can block the suspicious traffic – hence preventing an attack from occurring.
IDSs can work in combination with say a firewall to block traffic, but IPSs can detect and block traffic on their own.
IDS/IPS Location
There are two major locations where we can put IDSs & IPSs.
Host Based
Host based means the IDS or IPS is installed on a specific host, typically a high-value server, and the IDS or IPS is monitoring just the host it is installed on. If you want to monitor multiple hosts then you need a host-based IDS or IPS system on each host.
Network Based
A network-based IDS or IPS is connected to a network segment and monitors all the traffic within that network segment
In-line
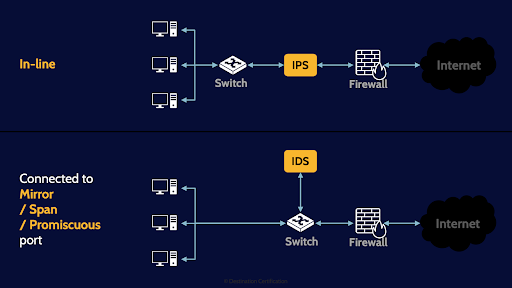
There are a couple of ways that a network-based IDS or IPS can be connected to a network segment. One method is in-line which means that all the traffic coming in and out of a network segment must pass through the IDS or IPS. IPSs are often installed in-line and the advantage of in-line is that if the IPS detects some traffic it doesn’t like it can easily block the traffic as all traffic must pass through the IPS. The major downside of in-line is it is another point of failure. If the in-line IDS or IPS system goes down or fails-secure then all traffic will be blocked causing a Denial of Service.
Mirror, Span, Promiscuous
The other method of connecting an IDS or IPS to a network segment is to connect it to a switch, and then configure the specific switch port that the IDS or IPS is connected to, to be a mirror or span, or my favorite name, a promiscuous port. By default, a switch will only forward packets to the intended system, thus by default the IDS or IPS wouldn’t see most of the traffic transiting the switch.
Setting a port to mirror, span or promiscuous means all the packets going through the switch will be copied and sent to the IDS or IPS so that it can monitor everything. It is more common to install an IDS in this configuration.
IDS / IPS Detection Methods
Now let’s talk about the two major methods that IDS or IPS systems can use to look for suspicious activity.
Pattern
Pattern matching means the IDS or IPS has been programmed to look for a specific pattern, for example a specific type of network attack, and will alert or block if that pattern is detected. The advantage of pattern matching systems is they can be fast and efficient, but the downside is they can only detect what they have been programmed to detect.
Signature analysis
The way a pattern matching IDS or IPS is told to look for a specific pattern is often referred to as signature analysis.
You can think of a signature as a unique fingerprint for a specific type of network attack. Therefore, the IDS or IPS system can have specific patterns or signatures programmed into it to look for things like byte sequences in network traffic or known malicious instruction sequences.
Anomaly
Anomaly based detection is a different approach that doesn’t rely on signatures and is meant to address the weakness that pattern matching systems can only detect what they have been programmed to detect.
With Anomaly based detection the IDS or IPS learns what normal looks like (it establishes a baseline) and then the system can look for behaviors that fall outside the accepted model of behavior – behaviors that are anomalous.
Stateful matching
There are four major ways anomalies can be detected. Stateful matching means the IDS or IPS looks for anomalies in the context of a stream of traffic. The IDS or IPS maintains a state table and can for instance detect if a system starts sending TCP packets to another system that it hasn’t established a session with.
Statistical
In Statistical anomaly based detection the IDS or IPS compares traffic to typical, known, or predicted traffic profiles to look for statistically significant anomalies from the norm
Protocol
Protocol anomaly based detection is where anomalies can be detected based on network protocols being used. For instance, certain protocols can be defined as allowed, and all others will be an anomaly. An organization might allow only SFTP. And if FTP or especially TFTP traffic is detected that is an anomaly.
Traffic
And finally traffic Identifies anomalies in expected pattern and behavior of network traffic transmitted within a session.
White & Black lists
IDS and IPS systems can use white lists or black lists as a means of detecting suspicious traffic. A better name for white list is an allow list – it is a list of IPs that a system is allowed to connect to and all other IPs are blocked.
And a better name for black list is a deny list – it is a list of IPs that a system is not allowed to connect to – access is denied – and all other IPs are allowed.
An IDS or IPS can be programmed to inspect traffic based on these allow or deny lists.
Sandbox
The final method that I’ll discuss that IPS or IDS can use to detect suspicious traffic is sandboxes. Sandboxes provide a safe area to run untrusted code and then observe what the code is doing: attempting to install ransomware perhaps…
An IDS or IPS system could detect that an executable file is being transmitted. The IDS or IPS could then take a copy of the executable and run it in a sandbox to see what the code does and if it is something nefarious then the IDS or IPS can alert and potentially even block the file from being sent to the intended victim system.
Honeypots & honeynets
A really cool way to detect an attacker on a network is to use honey pots or honeynets. A honey pot is a system that looks as close as possible to a real system – like a file server, or print server, or database, or industrial control system – however the honey pot is not a real system that is meant to be used by employees or clients of the organization.
Rather the honeypot is carefully monitored and if someone is trying to connect to and use the honeypot system that is a very good indicator that you may have a threat actor in your network that is exploring and looking for systems to compromise. A honey pot is a single system, and a honey net is a whole network of honeypots.
Honeypots and honeypots are a good way of detecting Advanced Persistent Threats.
Ingress vs. Egress
And the final inspection method that I’ll talk about is ingress and egress monitoring. Monitoring the traffic that is coming into a network (ingress) from say the internet OR the traffic that is leaving a network – egress.
It’s not uncommon for organizations to detect that they’ve had a breach by watching the traffic that is leaving – egressing - their network. If traffic is going out to a known bad IP address, then that’s a good indication that some malware has somehow infected a company system and the malware is calling home.

E.T. phone home
Endpoint Security
You can never have a secure network if the endpoints, the laptops, mobile phones, iPads, Alexa devices, IP Security cameras, etc. are not secure. As I discussed in the fourth video of Domain 3, it is critical to secure, to harden endpoint devices, by ensuring they are correctly configured, patched, have strong authentication, and so forth.

And that is an overview of Network Defense within Domain 4, covering the most critical concepts you need to know for the exam.
These MindMap videos are just meant to be a review tool. Want to see what our full / in-depth CISSP training videos look like? You can check them out here: https://destcert.com/CISSP-videos/

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
