Open Systems Interconnection OSI Model MindMap
Download FREE Audio Files of all the MindMaps
and a FREE Printable PDF of all the MindMaps
Your information will remain 100% private. Unsubscribe with 1 click.
Transcript
Introduction
Hey, I’m Rob Witcher from Destination Certification, and I’m here to help YOU pass the CISSP exam. We are going to go through a review of the major topics related to the OSI model in Domain 4, to understand how they interrelate, and to guide your studies.
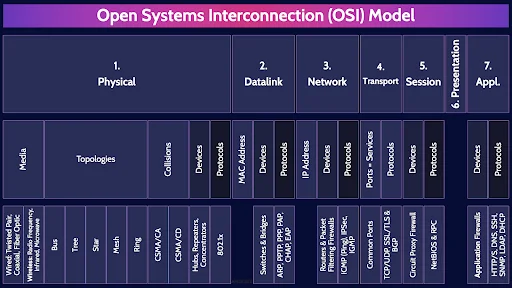
This is the first of four videos for domain 4. I have included links to the other MindMap videos in the description below. These MindMaps are one part of our complete CISSP MasterClass
Networking
Ahh domain 4 - Communication and Network Security. The domain that gives most people a headache when preparing for the CISSP exam.
You certainly don’t need to be a networking expert to pass the CISSP exam, but you do need to understand some fundamentals.
And this makes sense. Our modern-day systems are vastly interconnected through a spider’s web of different networking technologies. If we ever hope to secure our systems as Security Professionals, then it is important for us to understand the fundamentals of networking.
Let’s dive in shall we?
Open Systems Interconnection (OSI) Model

We are going to begin our whirlwind review of domain 4 with the OSI model. The Open Systems Interconnection model. The first, very important, thing to understand about the OSI model is that it is a model – a guide – a conceptual framework – which is meant to help standardize how systems should communicate with each other.
The key words in that last sentence are GUIDE & CONCEPTUAL framework. The OSI model is a suggestion, it is not a strict set of rules that must be precisely complied with.
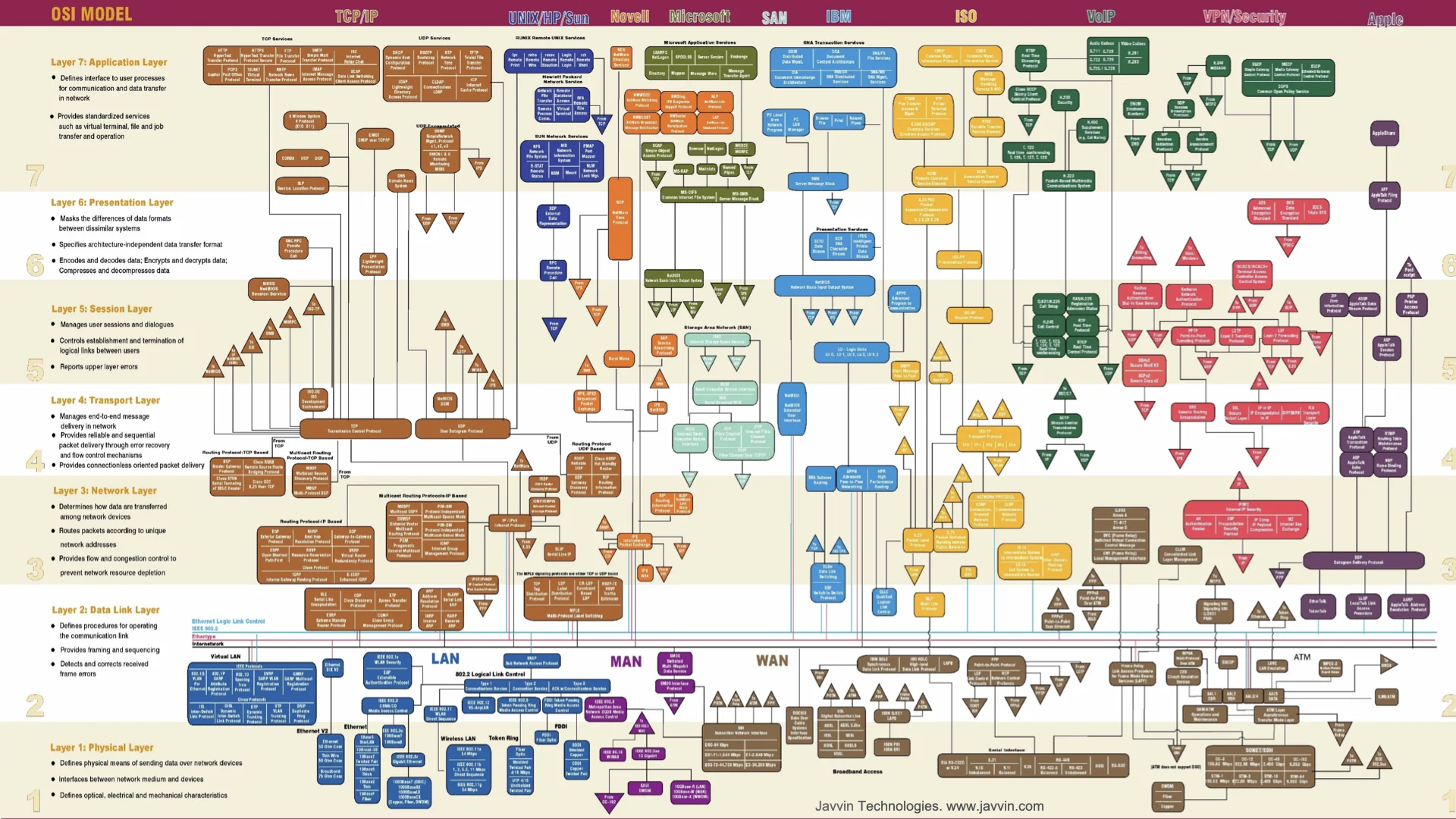
That’s why this is a highly simplified diagram of a few of the most common protocols and how they map to the 7 layers of the OSI model.
As you can see there are many protocols that operate at multiple layers of the OSI model and blur the lines between layers.
To say it is complicated is an understatement. And you certainly don’t need to understand all these protocols to this depth of detail. I do want to highlight a very important point though: when you read different books about protocols or google a protocol you will quickly find conflicting answers as to which OSI layer a protocol operates at.
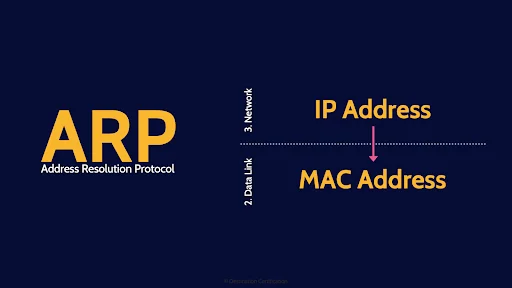
A perfect example is ARP. The address resolution protocol is used to translate an IP address – which operates at layer 3 of the OSI model down to a MAC address which operates at layer 2, the data link layer of the OSI model.
So, at which layer of the OSI model does the ARP protocol operate? Both layers 2 & 3.
Here is why I am telling you this. You will see questions on the exam asking you which layer a specific protocol or device operates at in the OSI model, and I am going to give you nice simple answers but recognize that this gets super complicated real fast if you dig into it. And you will find many conflicting answers out there.
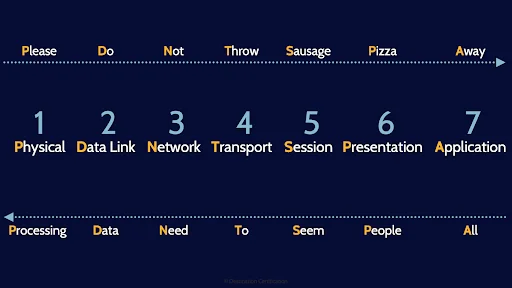
Alright, the 7 layers of the OSI model. You need to memorize the 7 layers and they are:
- Physical
- Datalink
- Network
- Transport
- Session
- Presentation
- Application
And here are a couple of mnemonics to help you memorize them.
Starting at the bottom we have the classic: Please Do Not Throw Sausage Pizza Away,
Or starting from the top we have: All People Seem to Need Data Processing.
I know some spicier ones, but I’m not going to share them here as YouTube might object.
Ok, now with that introduction out of the way, let’s go through each layer and I am going to start at the bottom, with layer 1, and briefly explain what is supposed to happen at each layer and the major protocols, devices, and other interesting tidbits at each layer.
1.Physical
Layer 1, the physical layer – is where the Binary transmission of data across physical media occurs. Electrons across wires, photons through fiber optic cables, and electromagnetic waves through the air for wireless. All different ways of moving bits.
Media
How specifically do we move bits? There are two major methods, with wires of some sort, or wirelessly through the air.
Wired: Twisted Pair, Coaxial, Fiber Optic
The types of wires you need to know a wee bit about include: twisted pair, also known as ethernet cable AKA Category 5 or more commonly CAT5 cable and there are newer standards like CAT6, CAT7 and CAT 8 cable and they all use the venerable RJ45 jack. There is also coaxial cable and Fiber Optic cable.
Wireless: Radio Frequency, Infrared, Microwave
From a wireless perspective, there are 3 major ways we can send bits wirelessly that you should know about: Radio Frequency which includes WiFi, Infrared, and Microwave. Microwave is a good way to connect buildings that are within line of sight and you want to save the cost of burying cable in the ground.
Topologies
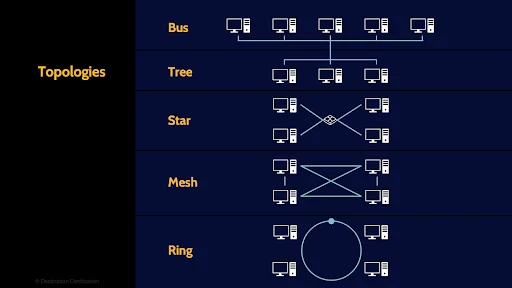
Now let’s talk about how we interconnect several systems together. There are different ways we can connect the wires to create different topologies.
Bus
The vast majority of the networks that we use today are fundamentally bus topologies. Every system is connected to every other system across a wire. This is a broadcast technology, and the major issue here is collisions. If two systems try to send data across the bus at the same time you will have a collision. And the more systems, the more collisions. This is a major problem.
Tree
This brings us to Tree topology which is still fundamentally a bus topology but we are beginning to segment the network, to force signals to go down a particular branch which helps reduce collisions.
Star
Star topology means all the systems are interconnected through a central device, like a switch. The big advantage of having a switch in the middle here is the switch can have some intelligence and only direct packets to the intended recipient which is a huge help in reducing collisions and increasing network throughput.
Mesh
Mesh topology means every device is interconnected with every other device. This is wonderful for redundancy. Full mesh networks are very rare but partial mesh networks where critical devices are interconnected, like boundary firewalls and routers, are very common.
Ring
And the final topology we will cover is the old school token ring. Token Ring has the big advantage of built-in collision avoidance. A token is passed around the ring, and a system can only send data when it has the token – meaning only one system can send data at a time. No collisions. But if a system malfunctions and doesn’t pass on the ring. No one gets to talk. That’s one reason token ring networks are pretty rare these days.
Collisions
As I mentioned the vast majority of networks that we use today are fundamentally bus topology which has the big problem of collisions. We therefore need methods of effectively dealing with collisions
CSMA/CA
CSMA/CA - Carrier Sense Multiple Access with Collision Avoidance – as the name implies avoids collisions and is used primarily in wireless networks.
CSMA/CD
CSMA/CD - Carrier Sense Multiple Access with Collision Detection – on the other hand detects if a collision has occurred and deals with it. CSMA/CD is used primarily in wired networks.
Devices
The major devices you should know about that operate at the Physical layer are:
Hubs, Repeaters, Concentrators
hubs, repeaters and concentrators. These devices have no intelligence, they just repeat signals, but they do it incredibly quickly and efficiently. That is a common theme we will see here in the OSI model. At the lowest level of the OSI model, the physical layer, there is essentially zero intelligence – zero ability to make decisions, but wicked good speed. As we move up, we gain more intelligence at each layer, at the cost of efficiency.
Protocols
The major protocol you should know about at layer 1 is:
802.1x
802.11 which is a whole family of protocols for wireless local area networks. You will no doubt have heard of protocols such as 802.11a, 802.11b, g, n, ac, and perhaps even the upcoming Wi-Fi 6 802.11ax.
You need to know a bit about a few of these 802.11 protocols which I’ll cover in the next MindMap.
2. Datalink
Let’s move on up to Layer 2, the Data Link layer which is responsible for Physical addressing, and reliable point-to-point connections.
MAC Address
It is at layer 2 that we have the very important MAC – Media Access Control address. MAC addresses are a unique identifier assigned to every network interface controller ever manufactured. Every device that connects to a network has one of these unique MAC addresses. Layer 2 switches use MAC addresses to figure out which system to send data to.
Devices
Layer 2 devices you should know about are:
Switches & Bridges
Switches and bridges. Bridges connect two physical network segments together and switches interconnect multiple devices so they can talk to each other and switches intelligently only forward data to an intended recipient based on MAC address greatly improving network performance over hubs. There are newer, more intelligent Switches that operate at layer 2 & layer 3. However, unless specifically stated you should assume a switch operates at layer 2.
Protocols
And the layer 2 protocols:
ARP, PPTP, PPP, PAP, CHAP, EAP
802.1x which is used for authenticating network devices to a network - it is a protocol used for Network Access Control
ARP – Address Resolution Protocol, which as I mentioned in the intro, translates an IP address down to a MAC address. It’s worth mentioning there is also RARP – Reverse Address Resolution Protocol which as you can probably guess translates a MAC address on up to an IP Address
PPTP - Point-to-Point Tunneling Protocol is used for creating tunnels. Lots more on tunnels and VPNs in video 4 of domain 4.
PPP – Point to Point Protocol - which encapsulates Internet Protocol (IP) traffic so that it can be transmitted over analog connections and provides authentication, encryption & compression
And authentication protocols PAP, CHAP and EAP which I will talk about in more detail in the next video.
3. Network
Next layer up is Layer 3, the network layer and it is responsible for logical addressing, routing and
delivery of datagrams
IP Address
And it is at layer 3 that we have the crucially important Internet Protocol (IP) Addresses. IP addresses are much like your postal address. If anyone wants to mail you a letter from somewhere on the planet, then they need your postal address: your country, province or state, city, street, and house number so that a letter can be routed to your specific mailbox. IP addresses serve the same function on networks. They identify a specific system and allow datagrams (packets) to be routed to the system across local area networks and even across the vast intertubes. Lots more on IP addresses in the next video.
Devices
Layer 3 devices you should know about are: Routers and Packet Filtering Firewalls.
Routers & Packet Filtering Firewalls
Routers forwards packets between different network segments based on IP addresses.
And Packet Filtering Firewalls are the simplest and fastest firewalls. I’ll talk a lot more about firewalls in video 3 of domain 4.
Protocols
And the layer 3 protocols:
ICMP (Ping), IPSec, IGMP
ICMP - Internet Control Message Protocol - allows network devices to send error and control messages and enables the Ping & Traceroute utilities.
IPSec - Internet Protocol Security – is the bewildering suite of protocols that provide data authentication, integrity, and confidentiality. I’ll talk about the components of IPSec in video 4.
And IGMP - Internet Group Management Protocol – which is used by hosts and adjacent routers to establish multicast group memberships. IGMP enables multicast groups – the ability to transmit the same packets to multiple systems at once.
4. Transport
Moving on up we have Layer 4, the Transport layer, which is responsible for End-to-end connections with error correction & detection.
Ports = Services
It is at Layer 4 that we have ports. Different ports equate to different services that are offered by a system across a network. You can kinda think of ports as the doors in a building. If a port is open, if a door is open to a room then you can access the services of that room. A door might be open to a cafeteria, or a washroom, or a bedroom.
There are 65,535 ports and I would recommend you memorize what all of them are used for.
Not funny?
Common Ports
Okay just remember a few of the most common ports:
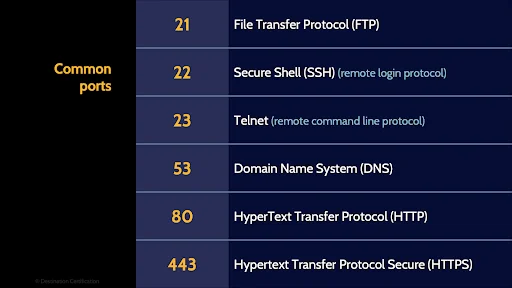
Port 21 is FTP – File Transfer Protocol used to transfer files between a client and a server
Port 22 is SSH - Secure Shell used for remotely connecting to a system
Port 23 is Telnet a remote command line protocol
Port 53 is DNS - The Domain Name System protocol which translates Domain Names to IP addresses. So we can remember nice simple domain names like Google.com and not have to remember 142.251.46.174
Port 80 is for HTTP – HyperText Transfer Protocol – the protocol that our web browsers use to connect to a web server
And ports 443 is Secure HTTP – secured using TLS – Transport Layer Security protocol that I’ll delve into in video 4
Protocols
And the layer 4 protocols:
TCP/UDP, SSL/TLS & BGP
TCP - Transmission Control Protocol - provides reliable, ordered, and error-checked delivery of packets
UDP - User Datagram Protocol – also delivers packets and does so with great speed and efficiency at the expense of a reliable connection and error correction. Good old send and pray.
TCP and UDP are two very important protocols to understand.
SSL/TLS - Secure Sockets Layer - and it’s latest version TLS which I just mentioned a few moments ago are used to encrypt HTTP traffic
And BGP – Border Gateway Protocol which is used to exchange routing and reachability information between routers - essentially the protocol looks at all of the available paths that a packet could travel and picks the best route based on numerous variables. It’s a critical protocol for getting packets to where they need to be across the internet.
5. Session
Next up: Layer 5, the session layer which is responsible for Interhost communication
Devices
The lone Layer 5 device you should know about is:
Circuit Proxy Firewall
A Circuit Proxy Firewall. Again, lots more on firewalls in the next video
Protocols
And the layer 5 protocols:
NetBIOS & RPC
NetBIOS - Network Basic Input/output System - which allows applications on computers to communicate with one another over a LAN
And RPC - Remote Procedure Call - which enables a client to send a request to a remote server to execute a specified procedure with supplied parameters
6. Presentation
That brings us to Layer 6, the Presentation layer which is all about… presentation. Character conversion. CODECS (compression & decompression for streaming audio and video). Image conversion. Formatting.
That’s really all you need to know about layer 6.
7. Application
And that brings us, inescapably, to the upper echelon of the OSI model: Layer 7. The application layer. Layer 7 is where we have the greatest intelligence to make decisions and layer 7 is responsible for human-computer interaction and where applications can access network services.
Devices
The major device that you should recognize as a layer 7 device is:
Application Firewalls
Application Firewalls. Very intelligent firewalls that can make very advanced decisions on what they allow through by performing things like deep packet inspection at the cost of a lot of latency.
Protocols
And some layer 7 protocols to now about:
HTTP/S, DNS, SSH, SNMP, LDAP, DHCP
HTTP/S - Hypertext Transfer Protocol – as I mentioned provides request-response services to allow a client to request web pages from a web server
DNS – Domain Name System
SSH - Secure Shell
SNMP - Simple Network Management Protocol is a protocol for collecting data from, and managing configuration of, network devices such as switches & routers.
LDAP - Lightweight Directory Access Protocol – is used for accessing and maintaining distributed directory information - connecting to, accessing, modifying, and searching directories – for example a corporate email directory
And DHCP - Dynamic Host Configuration Protocol – is used to assign IP addresses to devices as they are added to the network – to ensure there are no duplicate IP addresses

And that is an overview of the OSI Model within Domain 4, covering the most critical concepts you need to know for the exam.
Yeah, there’s a lot of networking stuff that you need to memorize for the CISSP exam. I have an incredibly helpful free resource to share with you. It’s a PDF document that summarizes each of the 7 layers of the OSI model, including the major devices, protocols, attacks and mitigations that you need to memorize for the exam. Plus, the free PDF also provides concise definitions of all these major protocols, devices, etc.
You should download it; you’re going to find it exceptionally helpful in your studies.
Link to download this FREE PDF is in the description below.

If you found this video helpful you can hit the thumbs up button and if you want to be notified when we release additional videos in this MindMap series, then please subscribe and hit the bell icon to get notifications.
I will provide links to the other MindMap videos in the description below.
Thanks very much for watching! And all the best in your studies!
